
Give your organization access to dark web data with our dark web API
Seamlessly integrate pre-attack intelligence into your security stack, so you can identify cybercriminals while they are still in the reconnaissance stage of their attack — giving your team the power to prevent rather than respond to threats.
Benefits of Integrating Dark Web Data into Your SIEM via API
Searchlight’s API and integrations make it easier to ingest, manage, and act on threat intelligence alongside your existing data.
Enrich your SIEM event data
Enrich your existing data with Searchlight’s automated dark web intelligence
Prioritize threats more efficiently
View all log and event data in real time from a single platform
Automate tasks and processes
Build workflows to automatically identify and resolve security issues quicker

Prioritize threats more efficiently
Integrate our dark web intelligence feed with your existing security solutions
Enrich your event and log data with automated dark web intelligence. Searchlight’s REST API provides context-rich dark web data in JSON format for cross-referencing past findings, reducing false positives and unnecessary alerts.

Simple, safe, secure access to dark web data
Secure Single-sign-on (SSO)
No matter which identity provider (IdP) you use, your team can effortlessly access dark web data in Searchlight through your preferred SSO provider using the SAML 2.0 protocol.
Our most popular integration for SOC teams
Splunk and Searchlight
Enrich your event and log data with automated dark web intelligence from Searchlight Cyber’s dark web monitoring platform, DarkIQ. Use Splunk to view and resolve dark web actions, freeing up time for SOC teams, security analysts, and engineers, and empowering faster risk mitigation and more reliable decision-making.
Detect and remove malware
Enhance your VirusTotal detections
DarkIQ integrates with VirusTotal to instantly identify harmful files, URLs, domains, and IP addresses, automatically detecting malware and malicious content. All actions are automatically prioritized in a single platform, with the option to explore the relationship between files using the Threat Graph for ongoing investigations.
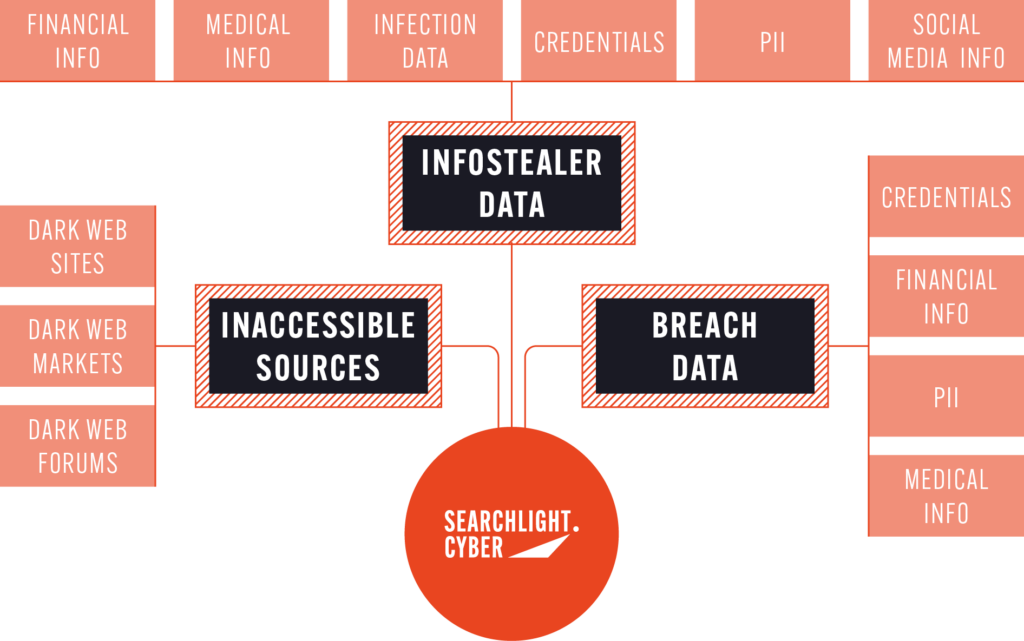
Unlock access to over 475 billion recaptured data points
Integrate context-rich dark web data to your security solutions
Draw from the world’s most comprehensive dark web dataset to give your organization unprecedented access to deep and dark web marketplaces, forums, and onion sites, as well as code repositories, social chats, CVEs, domains, phishing sites, and more.

