
In this blog we explain how fraudsters target ATMs, based on the devices and software they sell and the techniques they divulge on the dark web
Fraud, Theft, and the Dark Web
Criminals have been targeting automated teller machines (ATM) ever since they were introduced, honing their craft over decades. Some criminals are interested in obtaining the cash stored inside them, while others prefer to target customers – taking the opportunity to steal credit card information as they make a withdrawal.
As with most types of crime, the targeting of ATMs is a topic of discussion on the dark web. Criminals that specialize in ATM and card fraud share techniques on dark web forums, there are active markets for buying and selling the technology that is used to conduct these attacks, and there are special markets for monetizing the card data that is stolen from customers using ATM machines as well. All of which need to be monitored using dark web threat intelligence.
In this blog we’ll discuss some of the most popular techniques – based on our threat intelligence team’s observations – including what we have learnt from a source on a dark web forum that conducted an interview with a threat actor that specializes in selling card skimming devices.
Card Skimmers and Shimmers
Skimmers are tiny devices designed to capture card data as a victim is attempting to use the ATM or other point-of-sale services. These devices come in many shapes and sizes, some of them requiring installation at the entrance of the card slot, usually mimicking the green plastic bezel that we expect to see there. However, more sophisticated skimmers, known as “deep-insert” can be pushed inside the ATM card acceptance tray, where they cannot be seen by customers (Figure 1). These devices are very thin and feature a battery, card reader and a memory chip to store card data.
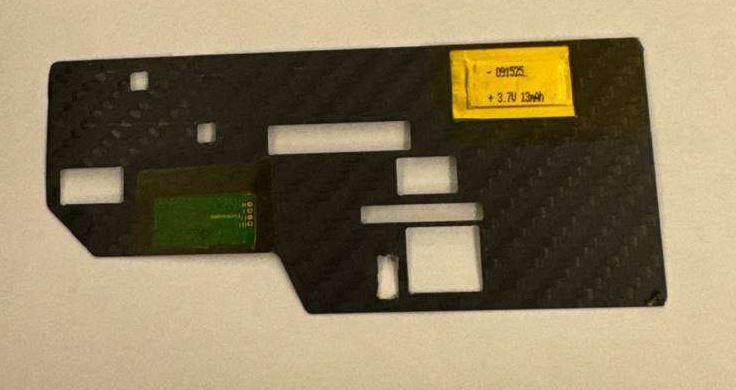
Figure 1: A deep insert skimmer for ATMs
Fraudsters have to use a specially crafted extraction tool to retrieve the device once the battery runs out, usually after a couple of days. Once retrieved, data can be downloaded on a computer using special software. In order to successfully clone a card with data captured using a skimming method an attacker also needs the card PIN, which is captured using a fake PIN pad (Figure 2) that can be glued on top of the legitimate one or by using a small camera hidden on the ATM’s surface. The skimmers and the auxiliary devices are often sold as part of a bundle, alongside instructions on how to use them.

Figure 2: A fake PIN pad keyboard
Once again, it is worth noting that it is not only ATMs that are targeted. We also observe point-of-sale (POS) device targeting, for example the device in Figure 3, which is specially designed to overlay the devices used in 7-Eleven stores.

Figure 3: POS overlay for devices used in 7-Eleven stores
Skimmers work by capturing data from the magnetic stripe of the card, which means that these devices are gradually going out of date as more cards adopt the “Europay, Mastercard, and Visa” (EMV) chip. Of course, criminals have developed similar devices that capture chip data instead – known as shimmers – which serve the same purpose of enabling payment card cloning.
Devices for Sale on Dark Web Forums and Marketplaces
Threat actors who manage to design functional skimmers and shimmers often choose to sell the products on dedicated cybercrime forums and marketplaces (as opposed to popular hacking forums such as Exploit, XSS, and BreachForums – where we rarely observe these products advertised).
There are a number of specialized carding forums where discussions about payment card cloning and related activities are more prevalent. For example, the Club2CRD underground forum is the home of a notorious seller of skimming devices, the actor BlackMass – who has been active since at least 2016 and has received multiple positive reviews from buyers. The thread captured in Figure 4 demonstrates the actor’s flexibility in crafting skimming devices customized to customers’ requirements.
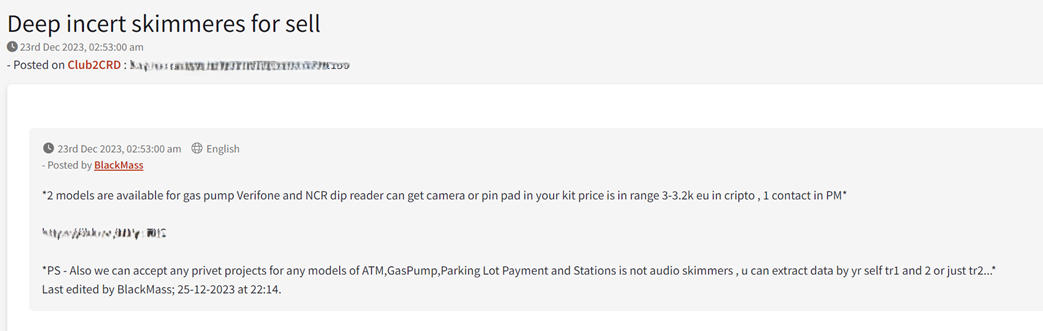
Figure 4: The actor BlackMass advertises skimmer devices on the Club2CRD forum
The actor seems to also have experience in crafting skimmers that can be used on gas pumps that have a self-service function (like the one in Figure 5). Gas pumps and parking meters are often targeted as they are rarely supervised, meaning that criminals can easily install skimmers without raising suspicion.
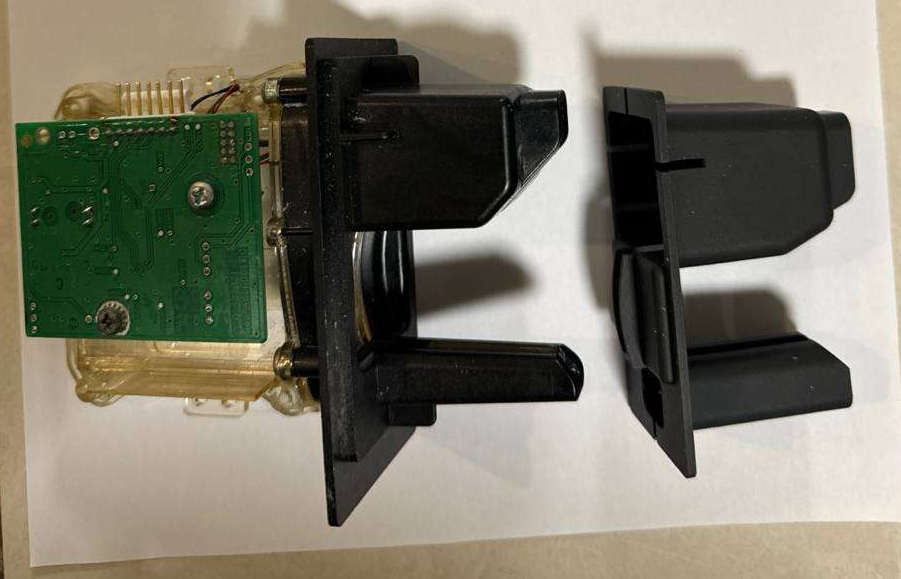
Figure 5: Gas pump skimmer
Interview with a Threat Actor
Our source in the Club2CRD cybercrime forum was able to conduct a brief interview with a threat actor who specializes in the sale of skimming equipment. To protect our source, the actor’s identity cannot be revealed. The actor communicated via Jabber and appeared to speak both Russian and English.
When asked about their experience, the actor claimed they had been active in the industry since before the dark web existed and worked with local “ATM specialists”. The actor implied that some of the “specialists” were insiders working for companies who ensured the physical security of ATMs, but insisted this was back when ATM security was not as sophisticated as it is now. Today, the actor only sells skimming equipment, auxiliary devices, and the software required to decrypt card data.
The actor mentioned that most of their sales consist of skimming devices for older ATM models (pre-2019) and gas pump skimmers. Newer ATMs are much more difficult to target. The skimming devices are crafted by modifying legitimate spare parts (especially for POS skimmers), 3-D printing (in the case of deep insert plastic skimmers) and custom Computer Numerical Control (CNC) cutting for metal, fiberglass and carbon skimmers, however these are much more expensive (starting from US $3,000 per kit). The actor stated that CNC machinery is required to obtain the very slim skimmers that can be inserted into newer ATM models. PIN pads and cameras are bought online from Chinese marketplaces and slightly modified based on customer requirements and adapted for the desired ATM model. The actor did not want to reveal additional information about the card data readers and the software used, claiming that a partner is in charge of these operations.
The actor also stated that worldwide delivery is available but most of their products are delivered to countries in the Middle East and a few countries in Europe. They claimed to use legitimate delivery methods for sending out the devices, such as DHL or FedEx, packaging the devices within childrens’ toys such as toy cars or dolls.
Monetization of Skimmer Data
As with most cybercriminal activities, the end goal is to obtain profits – so what happens after a card is successfully skimmed? There are two main ways that criminals monetize the data from card skimmers:
- Selling card data on the dark web: The easiest way is to sell the card’s data via a specialized marketplace, such as BidenCash. This marketplace offers thousands of cards for sale with starting prices as low as a few US dollars. This method is not very profitable but some criminals may prefer to sell the cards this way given the lower associated risks.
- Card fraud: The second method involves copying the stolen information on bank cards and using them to make purchases or withdraw money. Card cloning is a much more profitable way of cashing out but carries greater risk and requires an extra layer of technical expertise.
ATM Malware for Dispensing Cash
Getting access to the actual cash within an ATM is more difficult but there are methods advertised on the dark web that are more easily deployed than stealing the whole device and blowing it up. In a much quieter manner and without attracting any unwanted attention, crooks are able to make the ATM dispense banknotes with the help of malware.
If there are insufficient physical and digital security measures in place and criminals can gain access to the ATM cabinet, they can then connect a USB stick and keyboard to the computer. This allows them to install a specially crafted malware strain and instruct the ATM to dispense all the cash inside it. This type of attack is known as a “cash-out attack” or “jackpotting”. Figures 6, 7, and 8 show threat actors requesting or advertising jackpotting malware on a variety of dark web forums.
Figure 6: A threat actor posts that they are looking to engage in jackpotting on the dark web forum Exploit.
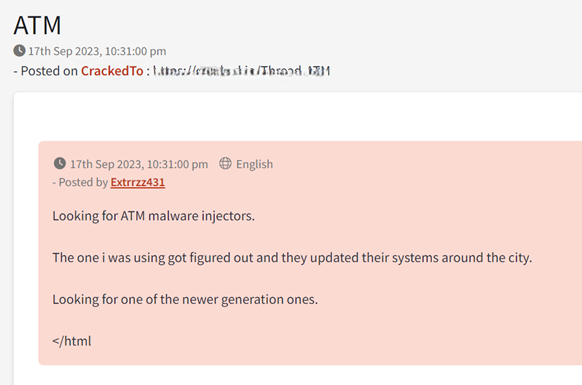
Figure 7: A threat actor requests ATM malware on the Cracked forum
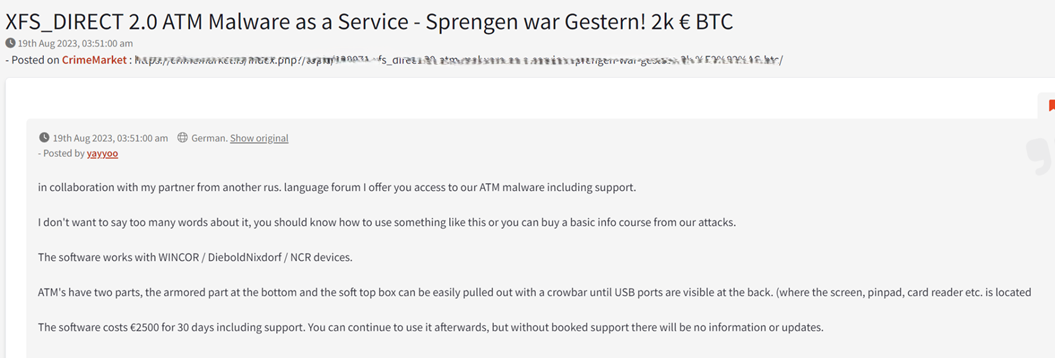
Figure 8: A threat actor advertises ATM malware for EUR 2,500 on a German-speaking hacking forum, CrimeMarket
In the past, we have seen criminals also use special EMV cards that were able to instruct the ATMs to dispense cash. The malware delivered with these cards was known as “Ripper”. However, more recently criminals have returned to the classic keyboard and USB stick to deliver malware such as FiXS, a strain that has been used to steal cash from ATMs in the LATAM region since 2023.
Another method used by criminals includes the use of a “black box”, a device usually in the form of a Raspberry Pi or similar product. The criminal has to gain access to the ATM internals, sometimes needing to drill a hole in the ATM case to connect to the internal hardware. Once the wired connection is in place the attacker can send legitimate commands to the ATM’s dispenser to eject cash, emulating the ATM’s software.
Of course, other than the EMV card delivery system, these methods require prolonged access to the internal ATM machine, which makes these techniques difficult to execute in geographies with a high level of security. However, as these posts and notable cases have shown, using malware to steal from ATMs is not impossible.
Identifying Criminal Trends Through Dark Web Monitoring
Monitoring specialized dark web forums where these conversations and sales take place can help law enforcement and financial institutions to identify what attack techniques are in vogue, the software and hardware that is being used, and some of the key “players” in this space – like the threat actor BlackMass.
This can help law enforcement agencies to investigate and crack down on these types of crimes – for example, alerting customs agencies that devices are being shipped in the packaging of childrens’ toys. It can also help banks or ATM developers to develop new security strategies based on the latest intelligence and put in place safeguards to protect their machines and their customers’ card details.




