
OUR Threat Intelligence Analysts unpick LockBit’s obfuscation of a recent cyberattack.
What Happened to Royal Mail?
Last Wednesday (January 11) Royal Mail, the UK’s postal service, warned its customers that its services were disrupted due to a “cyber incident”. The incident, which was quickly assumed to be a ransomware attack, impacted a back office system and prevented letters and parcels from being sent overseas while the company worked with the UK’s National Cyber Security Centre (NCSC) to resolve the incident.
A week later, Royal Mail confirmed that it has begun processing a “limited volume” of overseas mail through “operational workarounds”, but is still working with authorities to mitigate the impact of the attack.
Who Is Responsible For The Attack?
The cyberattack on Royal Mail has now been claimed by the Ransomware-as-a-Service (RaaS) gang known as LockBit, attributing its execution to one of its affiliates. However, for a few days this was unclear – seemingly even to LockBit itself.
Let’s break down the sequence of events:
Thursday, January 12, 2023
One day after the incident was announced, LockBit was reported to be the culprit by the Daily Telegraph, based on ransom notes that were printed from the UK postal service’s hijacked printers titled “LockBit Black Ransomware”.
Friday, January 13, 2023
Confusion ensued when the gang’s PR persona LockBitSupp distanced itself from the incident, claiming in a dark web LockBit forum post (below) that it had “nothing to do with it”. Citing last year’s leak of its ransomware builder, LockBitSupp hypothesized that this was the work of an unrelated actor attempting to discredit the gang’s “honest name” and that there was “no need to pay a ransom”.
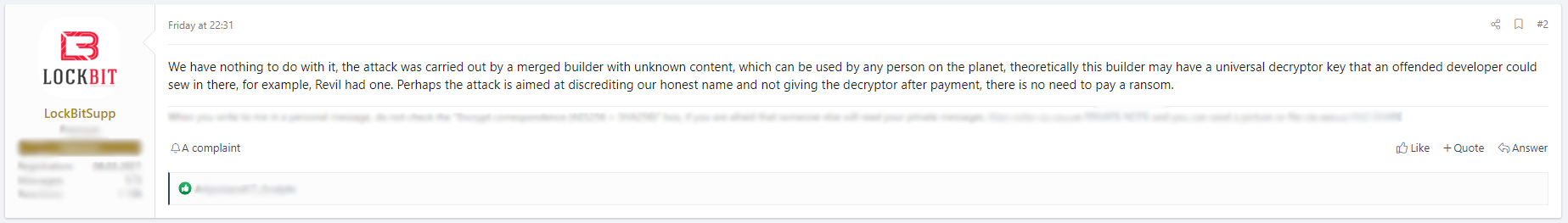
There were some aspects of this argument that weren’t immediately inconceivable. The ransomware builder for LockBit Black was leaked in September, reportedly by a disgruntled developer, so it was plausible that Royal Mail was dealing with a copycat using a ripped-off version of LockBit ransomware. Moreover, LockBit victims are typically listed on its dark web leak site, along with a timer counting down to when they need to pay the ransom in order to receive a decryption tool, and to prevent their data from being leaked. Royal Mail’s absence from the leak site either indicated that the group wasn’t behind it or that – for some reason – they didn’t want to be tied to the attack.
Another hypothesis was that the attack was conducted by a “legitimate” LockBit affiliate but that the group was denying it due to the high profile of the victim, which might attract unwanted attention from law enforcement. This has led to the downfall of RaaS operations before. Most notably, DarkSide was forced to shut down – or rather, rebrand – after its extremely high profile attack on Colonial Pipeline.
Saturday, January 14, 2023
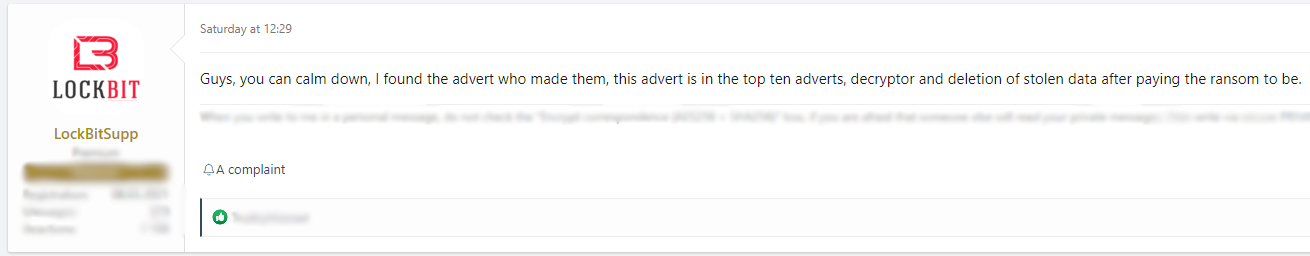
Less than 24 hours later, the same PR account (LockBitSupp) backtracked. It confirmed in a message (below) that one of its affiliates was indeed behind the attack, and assured readers of their good reputation for releasing decryptors and deleting stolen data once a ransom has been paid.
To understand this confusion, you need to understand how a RaaS operation – and LockBit in particular – operates.
Who is LockBit?
LockBit is a RaaS gang, meaning that it leases out the use of its malware to other cybercriminals who utilize it in their attacks. This model means that RaaS gangs typically have a lot of victims, as there are often multiple ransomware attacks being undertaken at once.
However, LockBit is extremely prolific even by RaaS standards. It was the most commonly used RaaS in 2022 and it has more than 1,300 known victims since it first emerged in September 2019. LockBit’s large network of affiliates means that it has victims across most industries, all around the world.
What Does This Debacle Tell Us?
Behind all of the drama there is a serious lesson to be learned from this incident about how RaaS gangs operate and why they are so serious. Defending themselves, LockBitSupp posted another message effectively saying that they can’t keep up with the amount of attacks their affiliates are conducting:
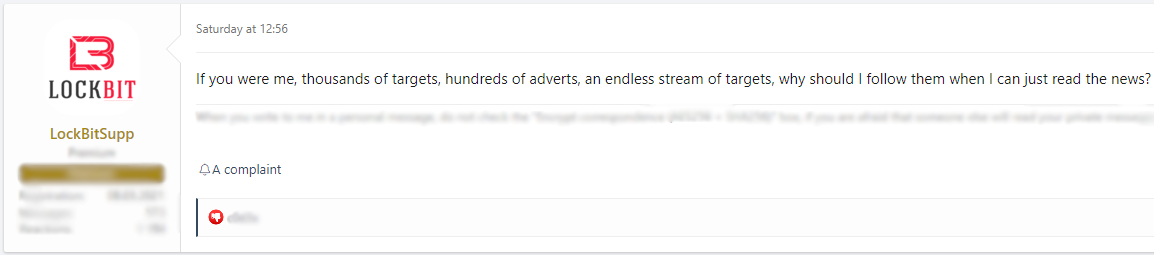
This underlines how little control and oversight ransomware operators have over their affiliates, while they put incredibly dangerous technology into their hands.
This is the second “reputational incident” for LockBit this month. The first was the ransomware attack on Toronto’s Hospital for Sick Children (SickKids), again apparently conducted by an affiliate without the approval of core LockBit operators. In this case, LockBit “formally apologized” for the attack, banned the affiliate for breaking its rules, and offered the hospital a free decryptor.
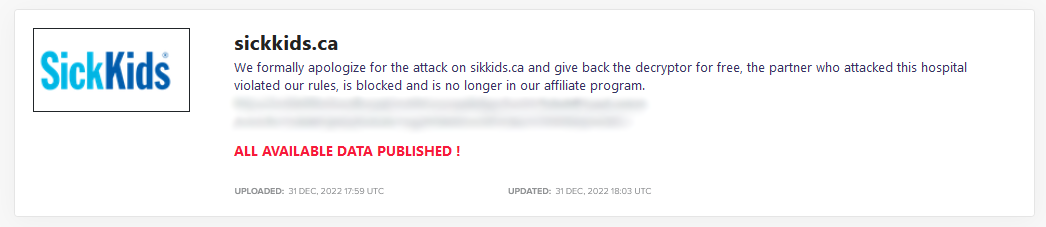
While the gang likely intended for this response to be seen as honorable, it’s presumably cold comfort for the children’s hospital that had to choose between mitigating the incident alone or accepting a tool from the criminal group responsible for the ransomware that infected it in the first place.
Both the SickKids and Royal Mail incidents indicate that the size of LockBit’s operation is making it unmanageable, which is bad news for organizations around the world who are face an ever-increasing chance of being impacted by LockBit ransomware – whether the RaaS operators are behind it or not.



