Did you miss our “Gaining visibility of the entire ransomware kill chain” webinar? This blog rounds up some of the key takeaways.
Understanding the Ransomware Kill Chain
In collaboration with Dark Reading, our recent webinar talked about how you can gain visibility of the entire ransomware kill chain. Luke Donovan, Head of Threat Intelligence at Searchlight Cyber, and Mo Ahddoud CISO, Chameleon Cyber Consultants explained the entire process of a ransomware attack – from the reconnaissance that takes place on the dark web, the day a ransomware attack strikes, all the way to incident response. This blog summarizes some of the key takeaways.
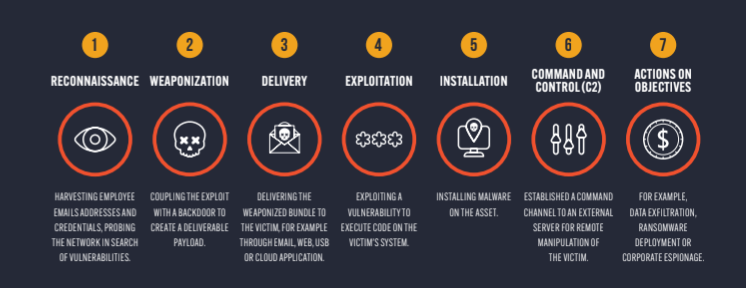
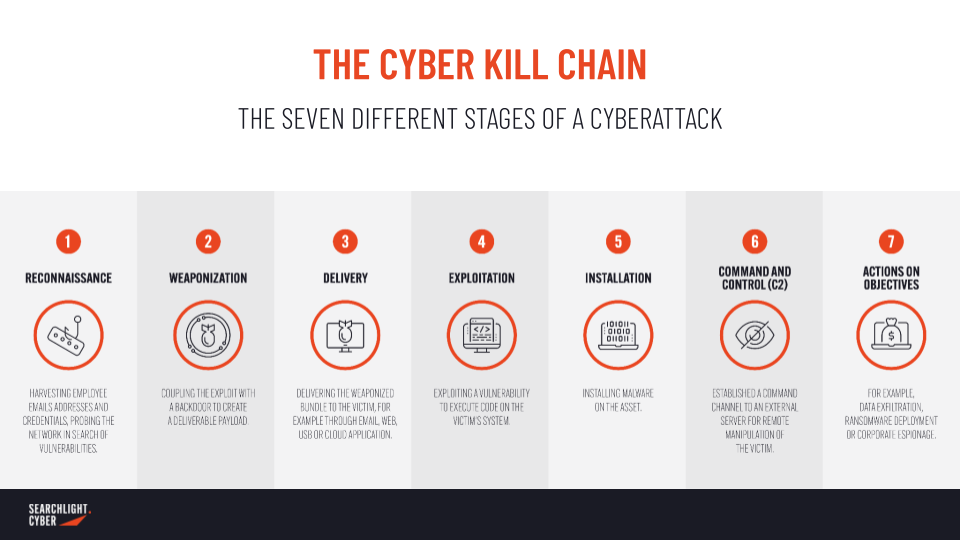
#1 What is the Cyber Kill Chain?
The Cyber Kill Chain is one of the more commonly referenced frameworks in cybersecurity. Originally developed by the aerospace and defense company Lockheed Martin, the framework is a part of the Intelligence Driven Defense model for identification and prevention of cyber intrusion activity, highlighting different stages of an attack a threat actor must complete in order to achieve their objective. To the left of the kill chain are the weaponization and reconnaissance, which will be done in a threat actor’s own environment, and from delivery onwards is where the breach happens.
There are seven stages in the Cyber Kill Chain:
An overview of the Cyber Kill Chain.
The webinar demonstrated that dark web intelligence can give security teams oversight of parts of the ransomware kill chain that were previously hidden – in particular, those initial reconnaissance and weaponization stages, which often take place on dark web forums or sites.
#2 What are the challenges businesses face when it comes to tackling ransomware?
Mo started with the difficult question of what challenges businesses face when it comes to tackling ransomware. In this clip he talks about how organizations are all-too-often still tripped up by traditional attack techniques.
“In many cases the root cause of the exploitation isn’t the route that was anticipated in an organization’s pre-planning. Although contradictory, cybercriminals are still using the same routes, with phishing emails being the main route. Immature organizations are still being exploited by the traditional attack techniques, whereas in mature organizations, there is simply a false confidence.”
#3 Gaining visibility earlier in the kill chain
In this clip, Luke talks about how threat intelligence has changed the visibility of the reconnaissance stage of a ransomware attack. Security teams can now gather intelligence that allows them to determine which of the dozens of ransomware groups out there are likely to target them. For example, they can observe discussions on dark web forums, where ransomware groups often buy the “initial access” they need to execute their attacks and – in some cases – organizations can even spot if a group is targeting them.
“If you can gain visibility earlier in the kill chain, there is more probability that you will be able to prevent an attack and a threat from escalating. A lot of time is spent in the reconnaissance stage, for example obtaining credentials to weaponize. It used to be difficult to do this because it takes place off your network, but with threat intelligence the reconnaissance stage is being seen.”
#4 Gaining insight from the dark web
Next, the panelists looked at the information that can be gleaned from digging into the ransomware leak site of a hacking group, and how this intelligence can help you inform your traditional cyber security plans.
“A lot of these ransomware groups are creating dark web leak sites, which can give you insight into who the victims are. If they mainly target your industry, you can understand:
- What the threat is.
- What entry points do they use?
- What are their tactics and procedures?
- What do they do when they gain access?
Having this information helps when you are putting your wider security infrastructure in place.”
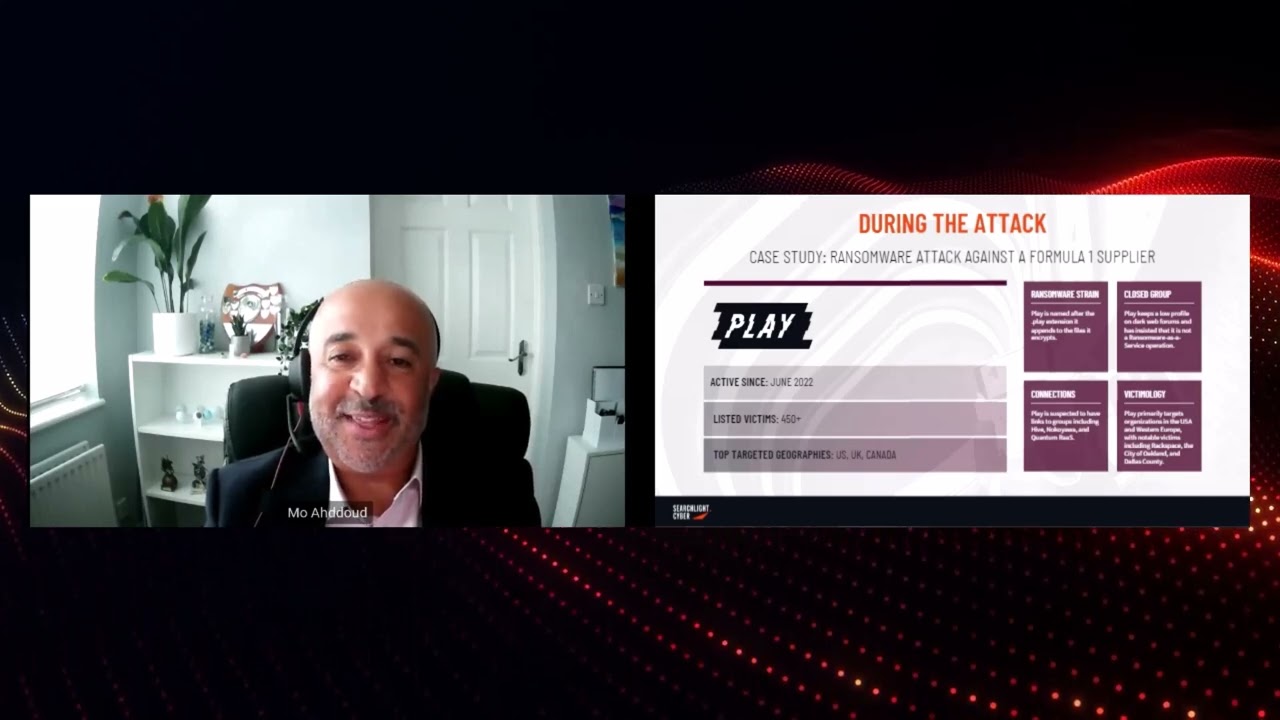
#5 Often, paying the ransomware doesn’t mean it’s over
When a ransomware attack does strike, organizations have to make the difficult decision whether to pay the ransom, with the hope that it will protect their systems or data, or not. Mo Ahddoud shared his experience of working with an executive team when the company was hit by a ransom attack.
“When looking at decisions around whether you should pay the ransom or not, there’s no confidence or any assurance you aren’t going to be targeted again, it’s a more complex environment than that. If you pay, the dark web group may say “we aren’t going to target you again”, but that doesn’t mean sprinter groups and others won’t. But having threat intelligence will give you the insight as to whether your organization is being talked about or not, which can give you a level of confidence.”
#6 The emotional impact of a ransomware attack
In this clip, Mo discusses how the emotional impact of a ransomware attack is often forgotten about during the incident response stage.
“When talking about cybersecurity, we miss out the emotional impact on the CEO and the leadership team, as well as those members of the response team. There could also be pressure from investors and the board. With lots of things happening, sometimes it’s easy to look at an attack from a cyber process driven machine, when it can be really difficult for the people involved.”
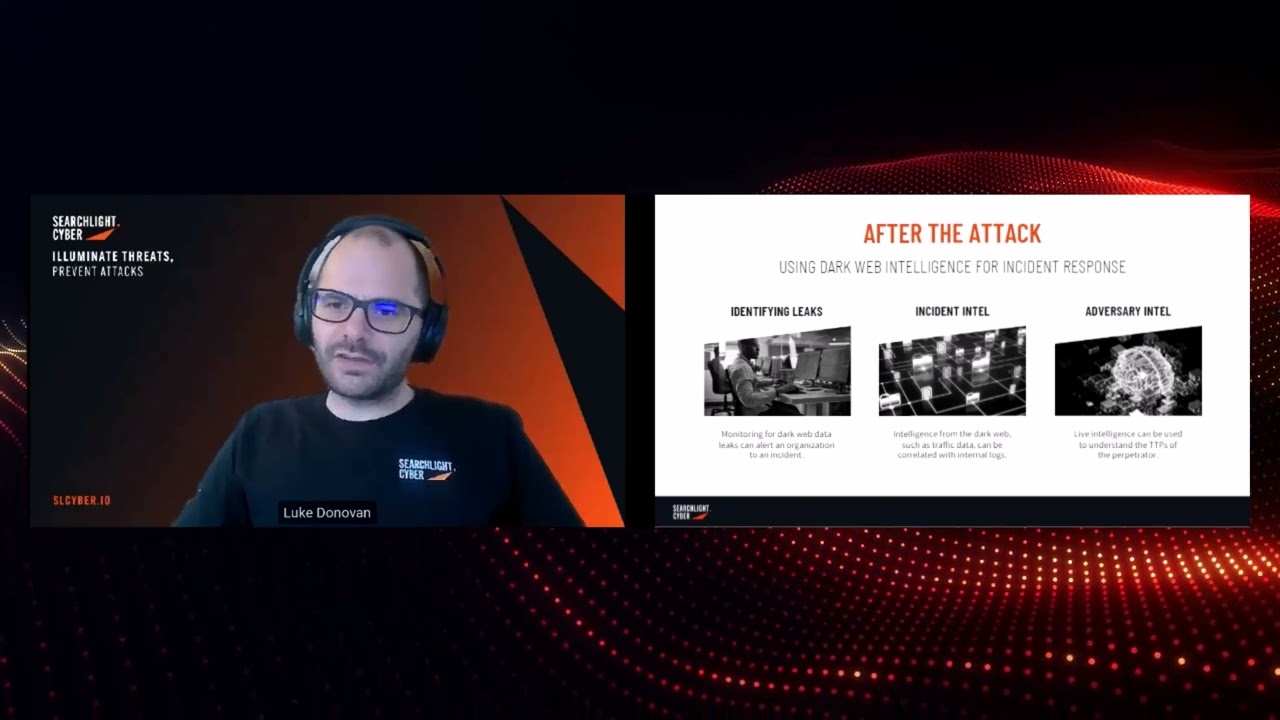
#7 How dark web intelligence helps with incident response
Luke shared his experience in coordinating the response to ransomware incidents, right at the far right of the Cyber Kill Chain. Key elements he pulls out are breach verification – establishing what data has been impacted by the ransomware group, which systems it came from, and how it could be misused.
Dark web intelligence can also help inform response through threat actor profiling – understanding the modus operandi of the ransomware group that has impacted you – for example, the systems they typically target and the techniques they typically use. This intelligence can be critical to informing the investigation into the incident and ensuring the vulnerabilities that led to the attack are closed:
“You have been hit by a ransomware attack: how on earth did they get into our systems? What information was out there that could have been exploited beforehand? If you can identify the initial access, you can establish which system was compromised, and put in place mitigative measures to ensure the same vulnerability is not exploited again.”
How does dark web intelligence help with the Cyber Kill Chain?
While many businesses spend time developing their cybersecurity infrastructure to mitigate the threat of a cyberattack, the work of a cybercriminal doesn’t start on your network. Many weeks, or even months before an attack, threat actors do their due diligence on their target, and plan their attack. This is where dark web intelligence comes in.
Dark web monitoring and intelligence gives organizations the capability to see threat actor activity that takes place off your network, early in the Cyber Kill Chain, providing a unique opportunity to take action and strike back against threat actors before your network is breached.
If you’d like to learn more about the ransomware kill chain, you can watch the full webinar on demand.
Stay on top of the latest cybersecurity news:
Sign up for our cybersecurity newsletter to get the latest cybersecurity news, insights, and dark web intelligence straight to your inbox, plus exclusive first access to Searchlight’s reports, blogs, and much more.
Sign up for our cybersecurity newsletter