If you missed our “Ransomware in H1 2024 – Dark Web Trends, Groups & Insights” webinar, this blog takes you through three of our key takeaways.
Understanding the ransomware threat
In this webinar Luke Donovan, Head of Threat Intelligence, and Joe Honey, Threat Intelligence Engineer at Searchlight Cyber talked about how the landscape of the ransomware ecosystem has changed in the first half of 2024. This blog looks at some of the key takeaways from the webinar.
Want to watch the full webinar? Click here to watch the webinar on demand.
How has the ransomware environment changed since 2023?
Since the start of the year there has been a perceived increase in law enforcement activity against ransomware groups. The type of law enforcement disruption we’ve seen has included:
- Arrests.
- Sanctions.
- Public/private and international partnerships.
- Infrastructure seizure.
- Decryption tools.
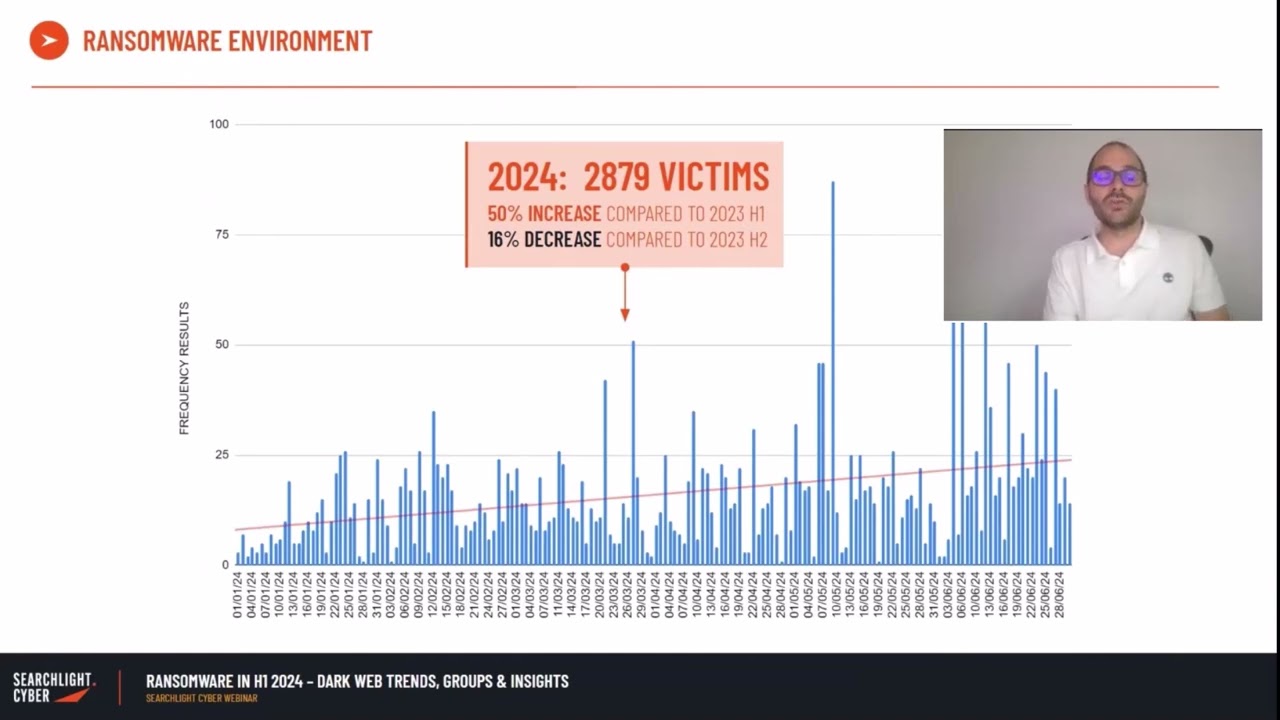
However, our experts explained in the webinar that there has also been an increase in the number of ransomware groups publishing victims in the first half of 2024. In the first half of 2023 there were 46 groups posting victims on their dark web sites, but in 2024 there have already been 72 groups. This equates to a 57 percent increase. The increase in ransomware groups has also seen an increase in listed victims in H1 2024 compared to H1 2023.
If you’d like to get the latest intel on ransomware groups and up-to-date cybersecurity news, SUBSCRIBE TO OUR WEEKLY CYBERSECURITY NEWSLETTER, Beacon.
Learning from past ransomware breaches
With ransomware still very much an ever-present threat, our speakers shared guidance of how organizations can learn from past attacks to mitigate the risk of a ransomware attack moving forward.
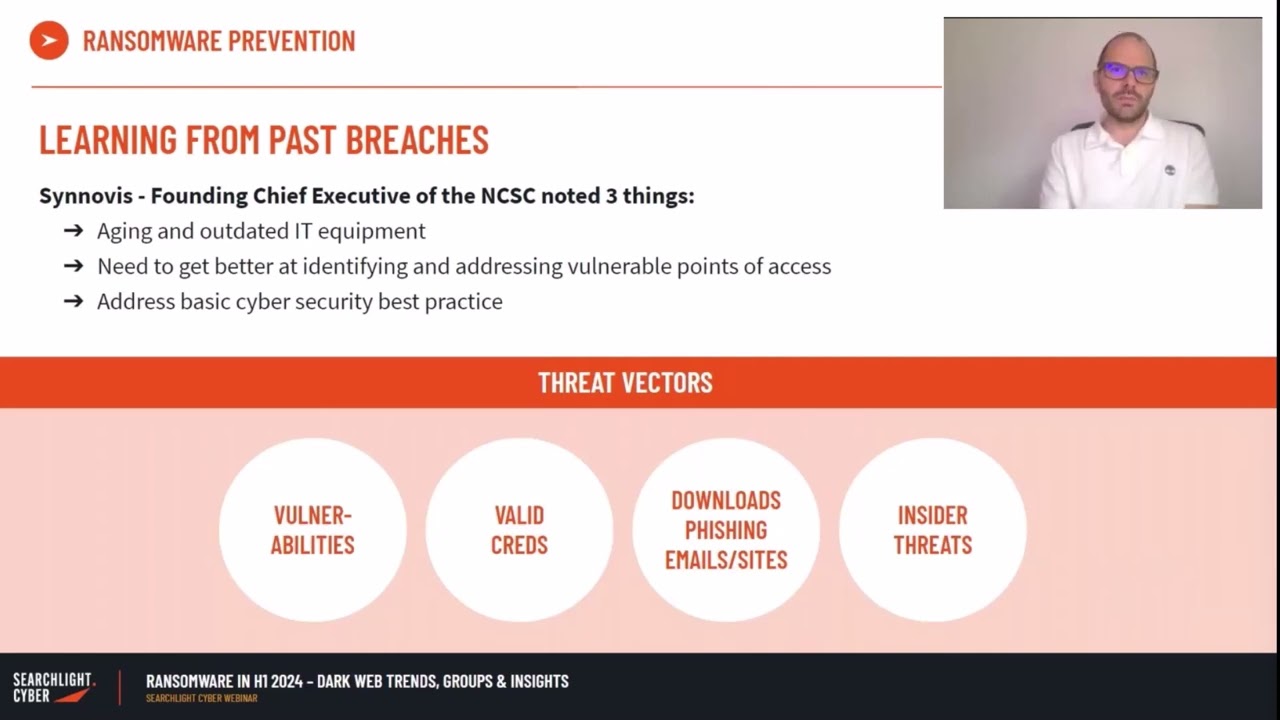
Luke Donovan pointed to guidance from the UK’s National Cyber Security Centre:
#1 Outdated IT equipment
Outdated IT equipment can leave your organization at risk of not only ransomware attacks, but other cybersecurity breaches and hacks. When software is not updated or the latest security patch hasn’t been made, it leaves you vulnerable. Cybercriminals will seek out the weaknesses in outdated equipment and systems to exploit them. By neglecting this element of your IT infrastructure you are making your systems an easy target for cybercriminals who will attack your organization and steal sensitive data, or lock you out of your own network. Therefore, regularly updating your software is a crucial step in maintaining the overall health and security of your organization’s IT infrastructure.
#2 Better identify and address points of access
To help you identify points of access in your infrastructure that may be vulnerable, conduct regular comprehensive risk assessments and penetration tests to determine how resilient your cybersecurity structure is. This involves scrutinizing the preparedness of your organization in terms of the tools available, the processes in place, and the skills of your cybersecurity team to effectively defend against potential attacks. By doing so, you can identify vulnerabilities and areas for improvement to strengthen your security posture.
#3 Address basic cybersecurity best practices
To mitigate the risk of a ransomware attack, as an organization you really should be covering the cybersecurity basics. It’s important to stay proactive and follow cyber security best practices to put yourself in the best position to defend an attack. But, what are the best practices?
- Backup your data.
- Keep all systems and software updated.
- Install antivirus software and firewalls.
- Provide constant cybersecurity awareness training to your employees.
- Limit user access privileges.
Should the three points we have discussed be addressed, cybercriminals will have a tougher time accessing your network, but if they aren’t, what are the ways in which cybercriminals can deploy a ransomware attack?
#1 Exploit vulnerability
If you have vulnerabilities in your cybersecurity defense, such as outdated IT equipment or unpatched software, cybercriminals will exploit those weaknesses and easily gain access to your infrastructure.
#2 Exploit valid credentials
Cybercriminals that want to attack your organization will search the dark web and identify any credentials which have been posted on the internet. This will essentially open a door into your business where they can take over the network and hijack your infrastructure.
#3 Downloads
Cybercriminals will target employees in your organization with phishing emails. It can take just one person to click the link in a phishing email, or download something from a fake website to open the door for a cybercriminal. This is where regular cybersecurity training plays a huge part in the fight against ransomware.
#4 Insider threats
Lastly, instead of a ransomware gang coming to your organization and planning an attack on your infrastructure, you should be aware of potential threats from inside your business. Disgruntled staff, suppliers, vendors, and clients who are looking for financial gain could download your sensitive data and sell it on the dark web to cybercriminals, who will then use that data to deploy a ransomware attack.
Combating ransomware attacks with dark web intelligence
Now we understand that the threat from ransomware gangs is growing and how these gangs may exploit and gain entry into your organization, how can you fight back against these cybercriminals?
Gather pre-attack intelligence
Before a ransomware attack even happens, there are ways your cybersecurity teams can be proactive by using dark web investigation tools.
Dark web investigation tools allow you to see cybercriminal activity that is happening off of your network, in what is known as the reconnaissance phase.
These tools will allow you to scour the dark web and understand how ransomware groups are targeting organizations in your industry and territory. Who are the gangs, what tactics are they using to gain entry, what are they doing once they gain entry? Having this insight means you can adjust your cybersecurity posture to match the potential threats posed.
Informed incident response
Having the pre-attack knowledge in your armory will make incident response easier. Already knowing about potential threats means that instead of interrogating thousands of rows of data and intelligence, you can really narrow down your search. This is especially helpful when trying to understand whether any sensitive data or credentials have been leaked – where have they been sold, who have they been sold to.
Post-attack actions
In your post attack debrief, having valuable insights from dark web investigation data can help you to understand where you can improve your processes:
- Which part of your cybersecurity posture needs adjusting to close any gaps in your infrastructure?
- What processes can be improved to ensure you know about threats earlier?
- Are you still vulnerable to a ransomware attack?
Using dark web intelligence to mitigate ransomware attacks
Many businesses will spend time developing their cybersecurity infrastructure to mitigate the threat of a ransomware attack but only put in place controls to identify and stop the cybercriminal once they have already gained access to their network. However, the work of a cybercriminal actually starts months before an attack.
This is where dark web intelligence comes in. Dark web monitoring and intelligence gives organizations the capability to see ransomware gang activity that takes place off your network, providing a unique chance to take action against cybercriminals before your network is breached.