The second part of our Initial Access Brokers blog discusses how cybersecurity teams can mitigate the risk of an attack by monitoring the dark web
Using dark web intelligence to protect against Initial Access Brokers
In the first blog we discussed everything you need to know about Initial Access Brokers, how they obtain their access, and how they sell it. We also delved into some examples of Initial Access Brokers we have observed on the dark web.
We have already established that Initial Access Brokers are a common threat to organizations, and that they specialize in breaking into networks to establish a foothold, which is then sold to cybercriminals on dark web marketplaces.
So, how can cybersecurity teams use the information on the dark web to their advantage to catch Initial Access Brokers and cybercriminals in the act, identify if they are being targeted, and patch the access that is being sold before it is exploited by the buyer?
Identify Whether Your Organization Is Being Targeted in an Initial Access Broker Post
Security teams should be monitoring dark web forums for Initial Access Broker posts that might pertain to their business.
It sounds unbelievable, but some cybercriminals even name the organization they are selling access to – presumably with the belief that security teams are not monitoring the dark web or, even if they are, that they are sufficiently anonymous that they don’t have to worry about repercussions. In these cases, security teams have a clear indication that they are a potential victim and can start to investigate the possible paths of attack.
However, in most cases, Initial Access Brokers don’t make it quite that easy and security teams have to do some work to identify whether they are the potential victim of the attack. While many Initial Access Broker posts won’t have the victim’s actual name – because the cybercriminal doesn’t want to tip the organization off before the access is solved – the advertisement does need to have some information about the victim, otherwise potential buyers won’t be able to identify what they are purchasing.
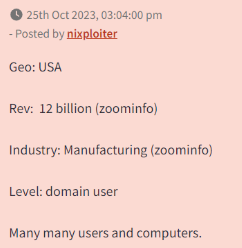
Often this information is pulled by the Broker from public sources such as ZoomInfo, and they sometimes even provide the source. Which means security teams can cross reference the information to determine the exact organization being targeted. Security teams can use these details to determine whether their organization (or perhaps one of their suppliers) fits the profile of the advertisement, which would then warrant further investigation.
Information in an Initial Access Broker post that may identify your organization
The organization information listed on an Initial Access Broker post can include:
- Company description.
- Geography.
- Revenue.
- Technology stack.
Determine the Credibility of the Post
If an organization determines that they fit the profile of the victim the next step is to verify the credibility of the post.
Modern day defenders are overwhelmed with alerts, data, and threats – they can’t chase every single lead they have. Pivoting on the profile of the Initial Access Broker can help them determine the likelihood of whether the threat is genuine and potentially gather more intelligence on the nature of the threat, based on the Initial Access Broker’s past activity.
This activity can help triage out any threat actors not assessed as credible threats. For example, a threat actor who has previously posted on the dark web asking what a webshell is might not be considered worthy of investigation, even if they make big claims about the access they have.
Monitor Cybercriminal Interaction with the Initial Access Broker Post
If the security team has assessed that the Initial Access Broker post is of high credibility it then becomes imperative to monitor for cybercriminals interacting with the post to determine whether the access has been sold, to who, and the capabilities of the buyer.
The actual bidding process sometimes takes place in private messages but you will often observe threat actors enquiring about the access or interacting with the post.
This can be invaluable information that could allow a security team to harden their internal defenses and monitoring, even if the initial attack vector cannot be remediated. For example, we have observed threat actors that are known to be associated with ransomware groups interacting with Initial Access Broker posts, which has allowed the organizations to prepare for that specific threat.
Security teams investigating potential buyers should be assessing details such as:
- The reputation of the buyer – which is an indicator of the level of threat they pose.
- The buyer’s association with larger criminal enterprises – such as ransomware gangs.
- The tools used by the buyer – based on information they have previously posted on dark web forums.
Continuous evaluation of intelligence
Once all the information and intelligence has been reviewed, organizations then need to accumulate all the data that has been gathered and continually analyze it holistically against the groups.
While you may not have seen access relating to your organization for sale on the dark web initially, it doesn’t mean there won’t be a listing tomorrow. Continuously monitoring activity on the dark web allows cybersecurity teams to act with speed, mitigate the risk and prevent an attack before it escalates.
Identify cybercriminals before access is exploited
If security teams are continuously monitoring for Initial Access Brokers posts as part of their intelligence requirements, this gives them a good chance of identifying the fact they are the victim before the access is exploited by the buyer. Effectively, they are catching the buyer right at the beginning of their “kill chain”, when they are purchasing the access they need to execute their attack. This provides security professionals with invaluable time to identify the access that has been sold and mitigate it before it can be exploited – effectively stopping the attack in its tracks.