Due to its anonymity, the dark web is a haven for those who wish to trade in illegal goods, including financial data.
dark web marketplaces
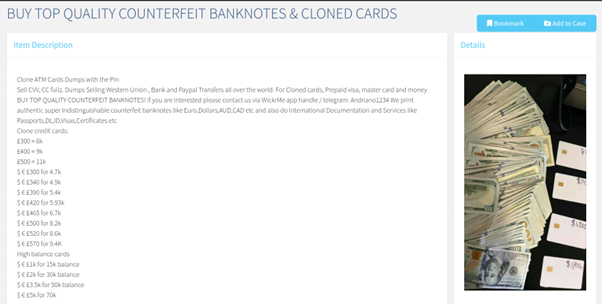
While dark web markets are perhaps best known for the sale of drugs, arms, and explicit material, there are also ever-increasing amounts of financial related data for sale. In fact, there are entire markets on the dark web concerned exclusively in the supply of data used in financial crime. Criminals also offer their dark web financial services for everything from procuring the information used in carding attacks (see details below), tutorials in fraud techniques, money laundering services, and everything in between.
With a cloned credit card for sale for as little as $20 on the dark web, or a New York Drivers licence for just $70, this type of crime has a low barrier to entry, and can be very lucrative for criminals. Consequently, research suggests that financial crime and fraud is on the rise:
- Crypto and banking both experienced a nearly two-fold increase in identity fraud in 2022.
- Payment fraud increased by 40 percent in 2022.
- More than half (51 percent) of organizations surveyed by PWC said they experienced fraud in the past two years, the highest level in 20 years of research.
- The Federal Trade Commission reports that US consumers lost $8.8 billion to fraud in 2022, an increase of 30 percent on 2021.
In this post we examine some of the most common dark web terms and tactics for financial crime and demonstrate that we are also seeing an upward trend in this criminal activity on the dark web.
What is Carding?
Carding is the process of using stolen credit/debit card details for goods or prepaid cards that can then be used by an attacker, or sold for a profit.
The attack starts with a threat actor gaining a list of credit or debit cards to use to commit fraudulent purchases. These card details are often purchased from dark web marketplaces (see post below) but originate from cyberattacks including hacked payment software on e-commerce sites or stealer malware that gathers information from a victim’s browser as they input sensitive information.
The criminal will then use these compromised cards to either complete purchases on the internet – typically high value goods that will resell quickly, and don’t require registration – think gift cards, electronic devices such as games consoles or TV’s etc.
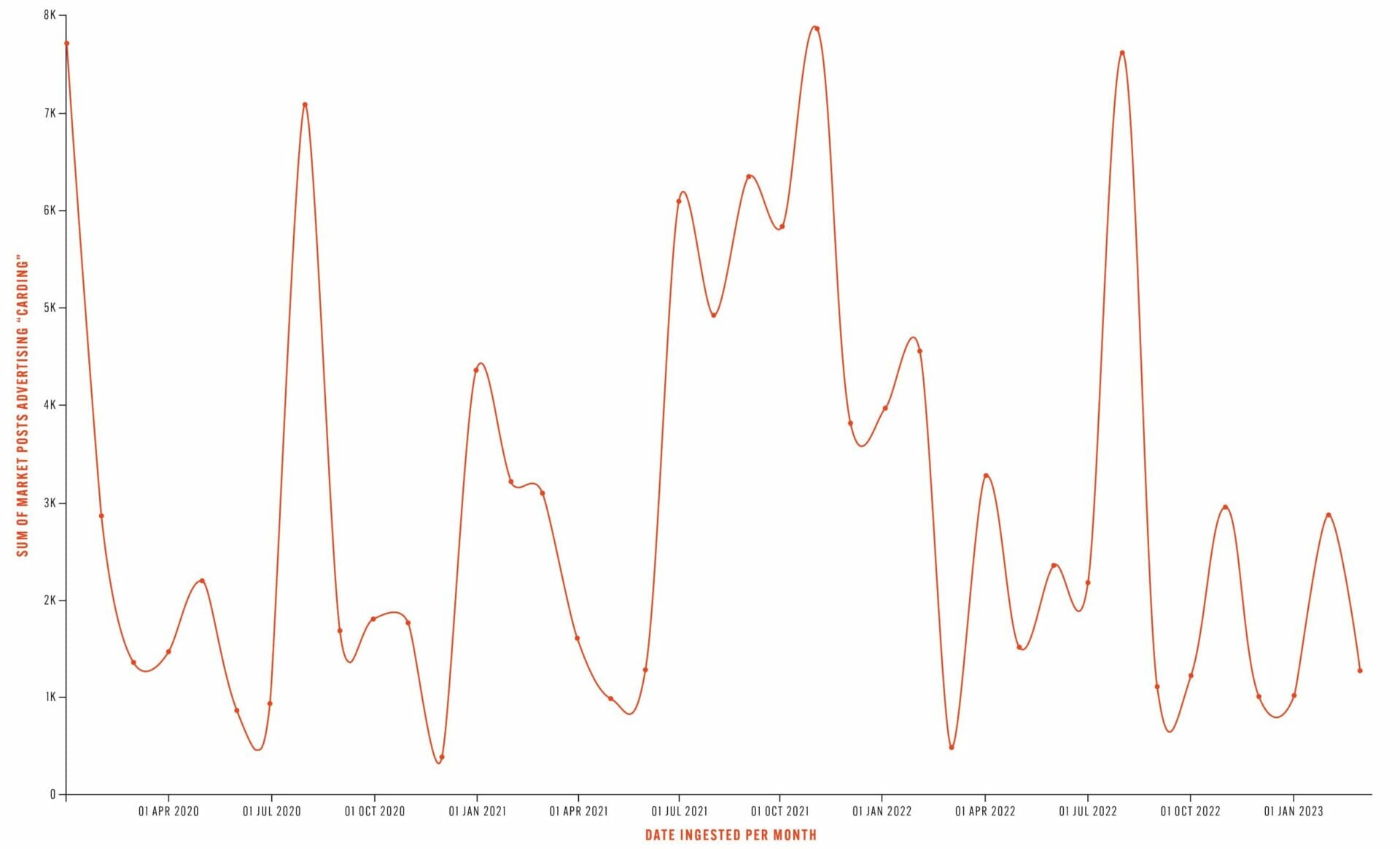
The graph below, derived from our dark web dataset, shows the number of market posts advertising “Carding” since April 2020, with a notable spike between summer 2021 and summer 2022.
What is a BIN attack?
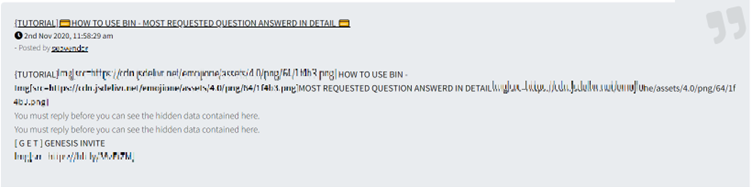
Another method that cybercriminals use to find valid bank details is called a BIN attack. In this instance, the criminal takes a Bank Identification Number (the first 6 digits of a card number) and uses a brute force method to find valid combinations for the remainder of the card number, CVV and expiry date. They then take these successful combinations and either sell them to other cybercriminals or make purchases themselves.
Below: A cybercriminal offers a tutorial on BIN attacks on a dark web forum:
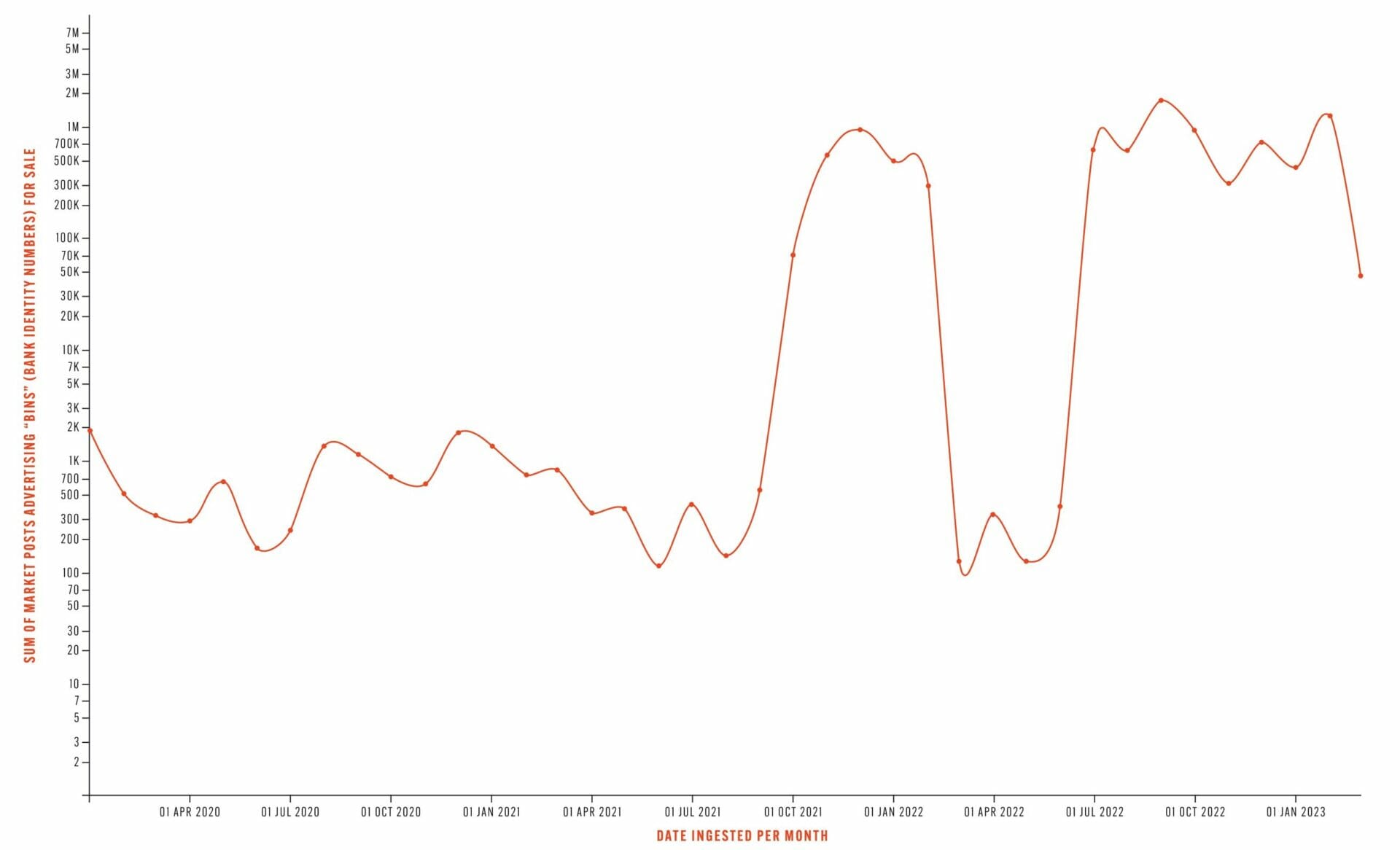
Our dataset shows a clear increase in advertisements for BINs over the past few years:
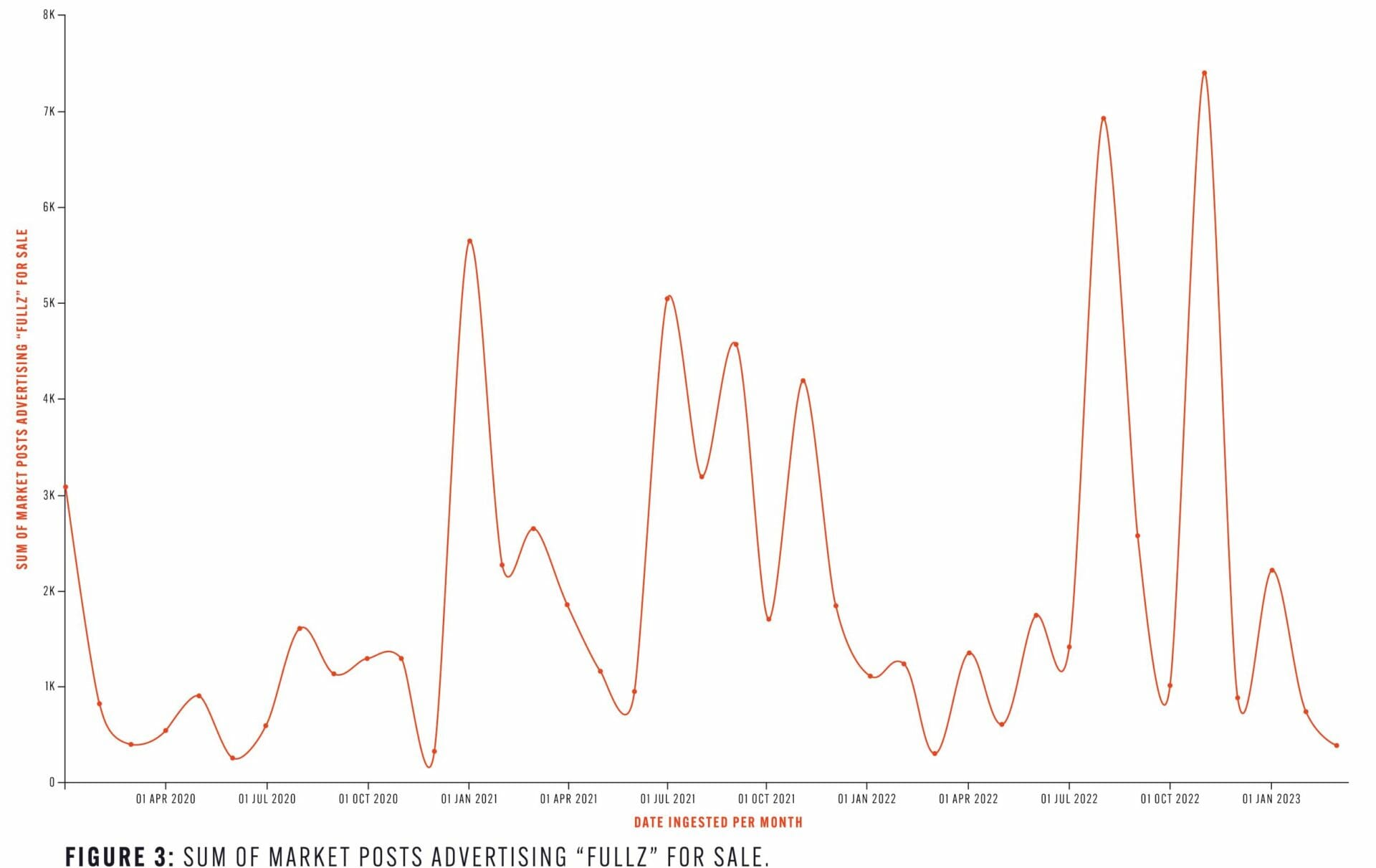
What are Fullz?
A slang term for “full information”, Fullz is a common term used on dark web marketplaces to describe a package of data containing all of the information needed to commit identity fraud – such as name, address, date of birth, social security number, etc. It also usually contains a proof of identity that can be used by a criminal. The post below is a typical advertisement for “Fullz”.
Once again, our dataset shows an upward trends in dark web advertisements featuring this term:
What Can be Done to Combat Dark Web Financial Crime?
With such a bustling black market for financial crime on the dark web, what can be done to stop it? Often, a lot of the onus is put onto e-commerce vendors and, indeed, there are some steps they can take to prevent the use of stolen credit card details on their sites. For example, they can monitor for signs of anonymous activity such as multiple low value transactions, unusually high volumes of international cards, large numbers of transactions being attempted in a short period of time, and card numbers being used repeatedly with variations in the security features (e.g. expiration date, card security code, and postal codes). There are also technical solutions they can put in place to try and limit fraudulent transactions, such as 3D secure and CAPTCHA tests.
However, if monitoring dark web activity teaches us anything, it is that cybercriminals will always find new ways to bypass the latest security methods. There is therefore an argument to be made that instead we should be looking at new tactics for financial services institutions themselves to cut financial crime operations off at the source, in the dark web.
For example, by monitoring the dark web for its BIN numbers, a bank could find all of its credit card details leaked on autoshops, pastebins and forums. With the stolen card details identified, the bank could then block the cards, inform customers so they are alert to any suspicious account activity, and contact the authorities to make sure they are aware of the cybercriminal operation – preventing fraud at scale.
Same Problem, New Solutions
Criminals have been exploiting credit cards since they were first invented. However, our insight into the dark web shows that tactics are becoming increasingly sophisticated, commoditised, and popular. The financial services industry therefore needs to be equally innovative in finding new solutions to fight back.