Stealth Browser enhances award-winning Cerberus investigation platform by allowing investigators to isolate their infrastructure from malware on the dark web
Washington DC, US & Portsmouth, UK – April 12 2023
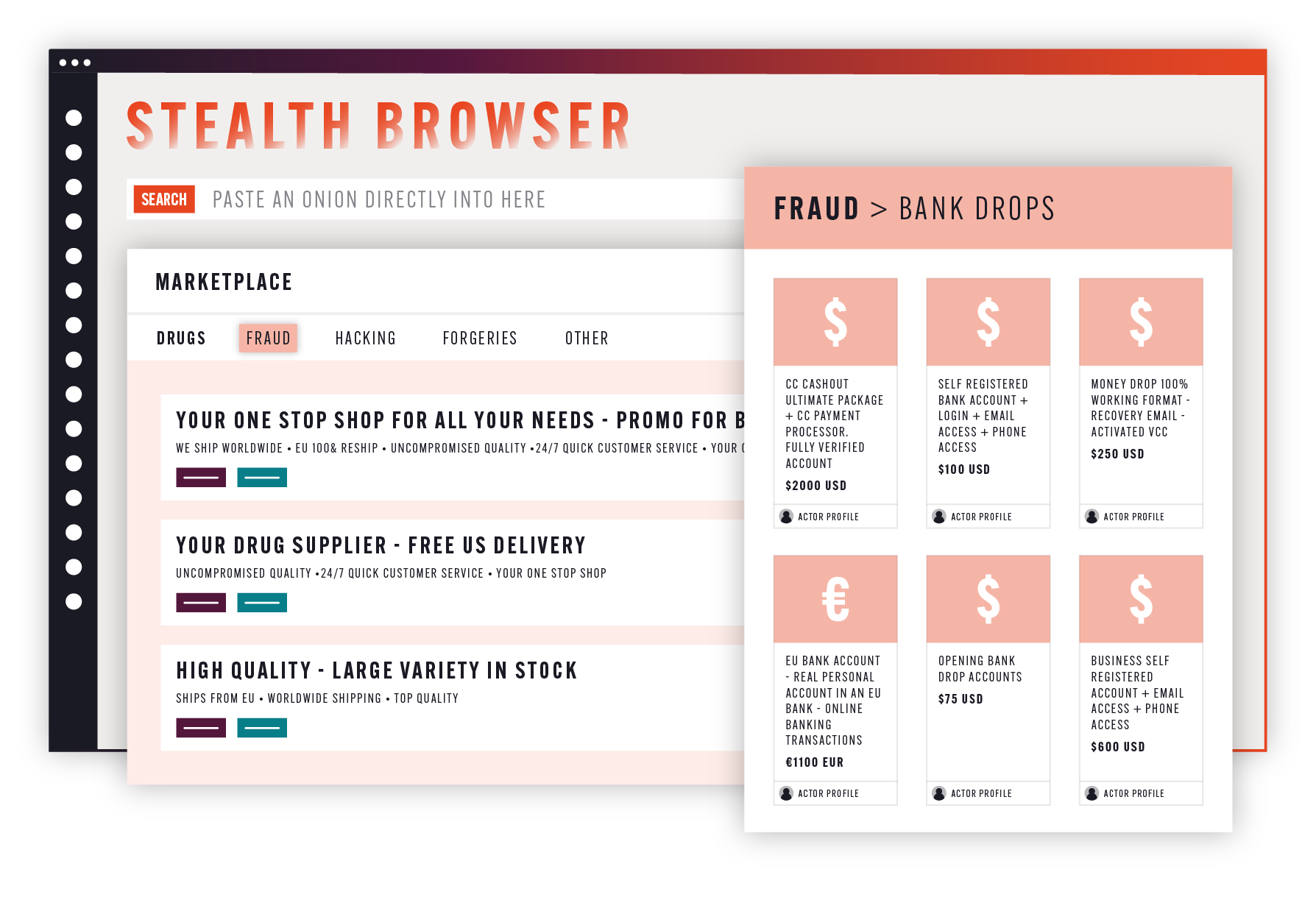
Searchlight Cyber, the dark web intelligence company, has launched Stealth Browser, a secure and user-friendly virtual machine for cyber professionals to access the dark web and conduct investigations anonymously, without risk to themselves or their organization. Stealth Browser is an enhancement to Searchlight’s Cerberus investigation platform, which is used by law enforcement agencies, enterprises and MSSPs to uncover criminal activity on the dark web, and has been used in some of the biggest criminal cases involving dark web activity.
The dark web is a critical source of intelligence for cybersecurity professionals, but accessing it carries risks for the investigator and their organization’s infrastructure. On their own systems, they run the risk of accidentally installing malware, exposing their digital fingerprint/proprietary IP address, or inadvertently leaking sensitive information. Stealth Browser eliminates these risks by automatically masking the investigator’s digital fingerprint, allowing both novice and experienced investigators to quickly and securely access Tor and I2P onions on the dark web without risk to themselves or their organization’s infrastructure.
With one-click, Stealth Browser allows the investigator to generate a virtual machine directly from any internet browser without the need to install any software. This is in stark contrast to the complex setup usually required to safely access the dark web, and allows analysts to get the relevant information they need more easily, without the need for lengthy administrative and approval processes.
Ben Jones, CEO and co-founder of Searchlight Cyber commented: “As with all of our solutions, Stealth Browser was developed in collaboration with our customers to address the challenges they face when conducting critical dark web investigations. Many organizations struggle with providing scalable and secure access to investigate threats on the dark web. Stealth Browser was created to allow any threat analyst, regardless of expertise, to get the information they need while always staying safe and secure.
“Threat hunters and investigators put themselves at risk when collecting intelligence on cybercriminals and malicious actors who are lurking in the shadows of the dark web. We created the Cerberus platform to allow organizations to securely investigate previously unobtainable dark web activity. The release of Stealth Browser is the continuation of this mission, further reducing risks in the fight to bring cyber criminals to justice.”
Stealth Browser is available now to all Cerberus customers.
aBOUT SEARCHLIGHT CYBER
Searchlight Cyber provides organizations with relevant and actionable dark web intelligence, to help them identify and prevent criminal activity. Founded in 2017 with a mission to stop criminals acting with impunity on the dark web, we have been involved in some of the world’s largest dark web investigations and have the most comprehensive dataset based on proprietary techniques and ground-breaking academic research. Today we help government and law enforcement, enterprises, and managed security services providers around the world to illuminate deep and dark web threats and prevent attacks. To find out more visit slcyber.io or follow Searchlight Cyber on LinkedIn and Twitter.