When is a ransomware group not a ransomware group? Our latest Ransomware Spotlight research focuses on the Everest ransomware group, who is increasingly acting as an Initial Access Broker
ransomware spotlight
Today we have released the second report in our Ransomware Spotlight series, where we focus on the latest dark web ransomware trends. Where our first report looked at Vice Society’s dark web footprint, our second report focuses on Everest – a ransomware group that is behaving anomalously based on their dark web activity.
CLICK HERE to subscribe to Ransomware Spotlight and receive the full report, or read on for the overview.
Who is the Everest Ransomware Group?
Everest has been around since at least December 2020 and has gone through a few iterations as a group. It was originally a data exfiltration outfit, before becoming a ransomware operator, and now increasingly specializing as an Initial Access Broker (as we discuss in this report).
It targets organizations across a number of industries and regions but with a particular concentration in the Americas and capital goods, health, and the public sector. It has listed just shy of 100 organizations on its dark web ransomware leak site, and is perhaps most infamous for targeting AT&T and several South American government organizations.
Its ransomware strain was historically linked to the EverBe 2.0 family and, based on more recent analysis of its ransomware, researchers have also linked Everest to the ransomware group BlackByte.
Key Findings Of The Report
Our report focuses on Everest’s increasing output as an “Initial Access Broker” – a cybersecurity term for criminals who sell backdoors into organizations onto other criminals but don’t carry out the attack themselves. Imagine the dark web equivalent of the person who sells a burglar the keys to a house.
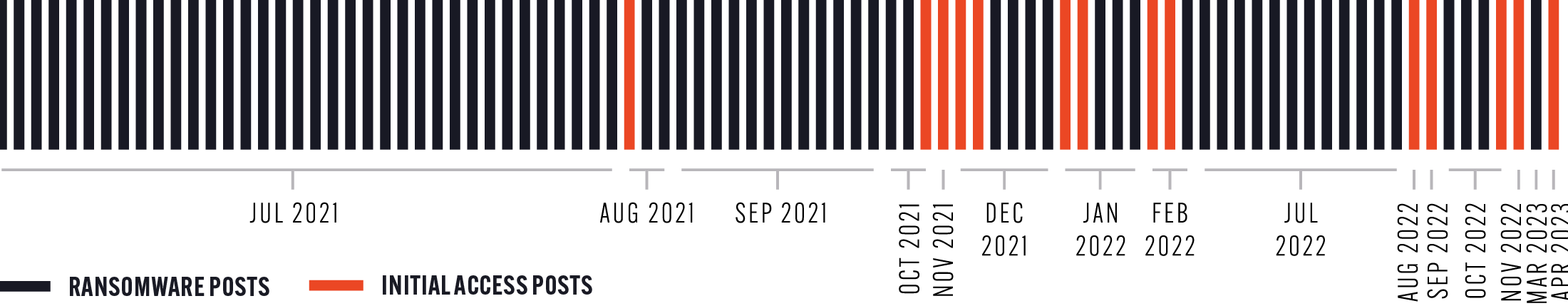
Everest was first observed as acting as an Initial Access Broker as far back as November 2021 but our dark web intelligence shows us that this activity has increased in recent months. See the graph below.
The Everest ransomware group frequently deletes its advertisements from its leak site, which means that other security professionals might not be aware of how often the group is acting as an Initial Access Broker.
Our analysts have managed to observe this marked increase because we capture deleted posts in our dark web investigation platform, Cerberus.
The Why
The next obvious question is why a ransomware group would become an Initial Access Broker, rather than just carrying out the attack themselves? This behavior is extremely rare among ransomware groups, as a ransomware attack would typically make more money than selling initial access.
It is not possible to assert Everest’s motivations with any confidence but in the report we provide a number of hypotheses to frame further research by the cyber threat intelligence community into the group. This includes trying to keep a low profile from law enforcement, a loss of personnel, or using Initial Access Brokerage as a different monetization tactic.
Sign up for the full report for the full overview of those hypotheses, as well as:
- A summary of the Everest ransomware group – including its MITRE ATT&CK TTPs.
- A comprehensive overview of the group’s dark web presence – including how it interacts through its dark web blog and profiles on hacking forums like XSS and BreachForums.
- What we can learn about Everest from what it has deleted from the dark web – using the posts from the group that we have archived in our dark web intelligence product as evidence.