
Proven In Bringing Criminals to Justice
Our solutions have been used in some of the biggest cases involving dark web activity by law enforcement teams – proven to bring perpetrators to justice. Investigators gather evidence on dark web criminals including groups that are dealing arms, drugs, and CSEA, or are connected to hostile intelligence, ransomware gangs, organized crime, and human trafficking.
How do you investigate criminal activity on the dark web?
Criminals use networks like Tor and I2P for their anonymity, which makes dark web investigation difficult for law enforcement – but not impossible. In this short video our CTO Dr. Gareth Owenson talks about the techniques that investigators can use to catch criminals operating on the dark web.
Dark Web Investigation Tools For Law Enforcement
A powerful dark web search and investigation platform. Investigators with or without dark web experience can use Cerberus to search and access more than 15 years of archived dark web data to uncover criminal activity that was previously unobtainable.
Advanced capabilities for investigating the dark web
Criminal activity on hidden dark web sites, forums, and marketplaces is a crucial source of information for cybercrime investigators. However, accessing this information can pose risks for the investigators and their organizations.
Our dark web investigation tool makes it easier to identify, preserve, and share evidence related to ransomware, criminal activities, and threat group operations – with powerful search and case management tools to accelerate investigations.
Dark web virtual machine for secure investigations
Securely access dark web sites and conduct anonymous investigations with our Stealth Browser while automatically protecting your identity and network.
The Stealth Browser eliminates the risks associated with accessing the dark web by automatically masking your digital fingerprint, allowing investigators to quickly and securely access Tor, I2P, and clear web sites without risk to themselves or your organization’s infrastructure.
Understand threats in other languages
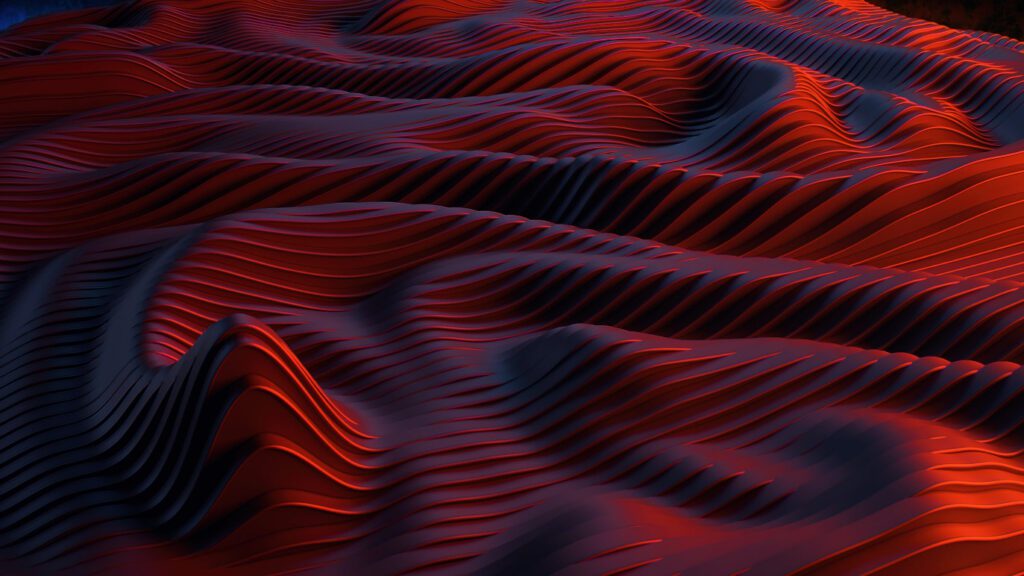
Our dark web investigation tools enable you to gather evidence on known offenders, track individual actors' posting history, and uncover other aliases they may be using on the dark web.
With automatically enriched, indexed, and translated data from the top 10 languages on the dark web, along with advanced case management, actor activity alerts, and automated reporting, you can easily maintain, audit, and report on multiple investigations and teams in real-time.
Identify Criminal Actors on the dark web
Law enforcement agencies can investigate individuals on the dark web with the ability to cross-reference aliases, usernames, and pseudonyms across marketplaces, forums, and sites to easily build a profile of high-severity criminal actors.
Dark Web Sources
law enforcement agencies Use Searchlight Cyber to Access
850,000+ dark web sites
Hosted on the Tor network, where cybercriminals believe they can act anonymously.
100+ dark web marketplaces
Selling illegal commodities ranging from arms and drugs, to malware and stolen credit card details.
70+ dark web forums
Including those used by sex offenders to share and distribute CSEA.
Clear and Deep Web Sites
Not hosted on the dark web but are nevertheless hard for law enforcement to access, such as private social media channels, and unindexed websites.
Evidential
Built for Law Enforcement and Government Agencies
Our solutions were built in close collaboration with law enforcement and government agencies to give investigators access to the dark web without putting them at risk. They are designed to be intuitive and do not require technical knowledge or special software to use, helping to reduce resource requirements for law enforcement.
Powerful case management tools
Our case management features enable you to maintain, audit, and report on investigations in a format that is accessible to other departments and the criminal justice system. Our collaboration tools mean you can work across departments within the platform and easily deconflict targets.
Trusted by the world’s most forward-thinking enterprises and cyber investigation teams
⭐⭐⭐⭐⭐
Excellent service. Great tool for breach investigation.
— Managing Director, IT Services Industry
(GARTNER PEER INSIGHTS)
⭐⭐⭐⭐⭐
Unique high-tech offering yet with people who are easy to work with.
— Security practice director, IT Services Industry
(GARTNER PEER INSIGHTS)
⭐⭐⭐⭐⭐
An amazing resource for conducting breach investigations.
— Digital marketing Analyst
(G2CROWD)

Dark Web Investigation FAQs
Our tools enable investigators to gather evidence on criminal activities occurring on the dark web. Criminal activities include the dealing of arms and drugs, CSEA, in addition to gathering intelligence on ransomware groups, organized crime syndicates, and human trafficking networks.
Our solutions were developed in collaboration with law enforcement and government agencies, to give investigators secure access to the dark web. Regardless of their dark web experience, investigations can use our browser-based tools to intuitively search and gather evidence on the dark web.
Law enforcement faces several challenges during dark web investigations. First, the anonymity and encryption provided by tools like TOR and I2P hinder criminal identification, necessitating deep technical expertise to navigate hidden services. When investigating criminal groups like Lockbit, jurisdictional complexities arise across state and international borders. Third, keeping up with the evolving dark web tactics and managing the overwhelming volume of data pose resource challenges for investigators.
Searchlight offers comprehensive platform onboarding to help investigators and analysts get the most from our dark web investigation and monitoring platforms. However, we’ve learned from conversations with our customers that often the dark web is complex to navigate for investigators – even for experienced professionals.
That’s why we launched The Dark Web Academy. This two-day instructor-led training helps law enforcement and security professionals bridge the dark web skill gap and tackle threats using the Cerberus dark web investigation platform. Through hands-on exercises, attendees will develop their technical skills, as they work with real-world dark web data – gaining the critical skills and confidence they need to conduct investigations using the Cerberus platform. Visit our training page to learn more.
Criminals on the dark web will often use specialist browsing software such as TOR or I2P to conceal their activities and identity. Tor operates using the concept of “onion routing”. This involves data being sent through a circuit of nodes, similar to an athletics relay race. However, unlike a relay race, you only know the identity of the person who handed you the baton and the person you’re passing it on to – thus keeping the identity of the user anonymous. However, the threat posed by criminals on the dark web also offers an opportunity to security and investigation teams. Searchlight provides automated dark web monitoring and dark web investigation tools. These tools allow cybersecurity professionals to access information that cybercriminals wish to keep hidden. By using Searchlight, they can identify the earliest warning signs of an attack and conduct criminal investigations to unmask the identity of the criminals behind the dark web aliases.
Investigating cybercrime is a complex process that often involves multiple teams, regions, and countries. As such, law enforcement agencies require access to case management features that allow them to maintain, audit, and report on multiple investigations across multiple teams. Searchlight’s dark web investigation tool gives investigators access to tools they need to gather evidence from the dark web, easily share with other teams, and build cases, so they can focus on deconflicting targets.





