Detect when your files are exposed in undisclosed ransomware attacks. This feature lets you search and set alerts for keywords found in the file names within unpacked file trees.
The Ransomware File Explorer securely downloads and indexes ransomware leak-site file-tree data into Cerberus. This enables pre-emptive detection of compromised files, accelerating your incident response even when your organization is not the primary victim.
Key Benefits
- Save time identifying and accessing file trees on leak sites
- Pre-emptively detect leaked PII & intellectual property
- Prevent operational, legal, or reputational damage
Saving security and investigation teams time
Although leak data is publicly accessible, obtaining and processing the file-tree structures and data behind them is highly time-consuming. Searchlight automatically gathers and indexes this information, making it searchable forever – even if the file-tree is later deleted from the dark web.
“Before Searchlight, we had to manually identify the source and review ransomware files to check if we were mentioned. This process can take hours, and sometimes the files are removed before we can analyze them.”
– Managing Director, Enterprise Organization
How it works
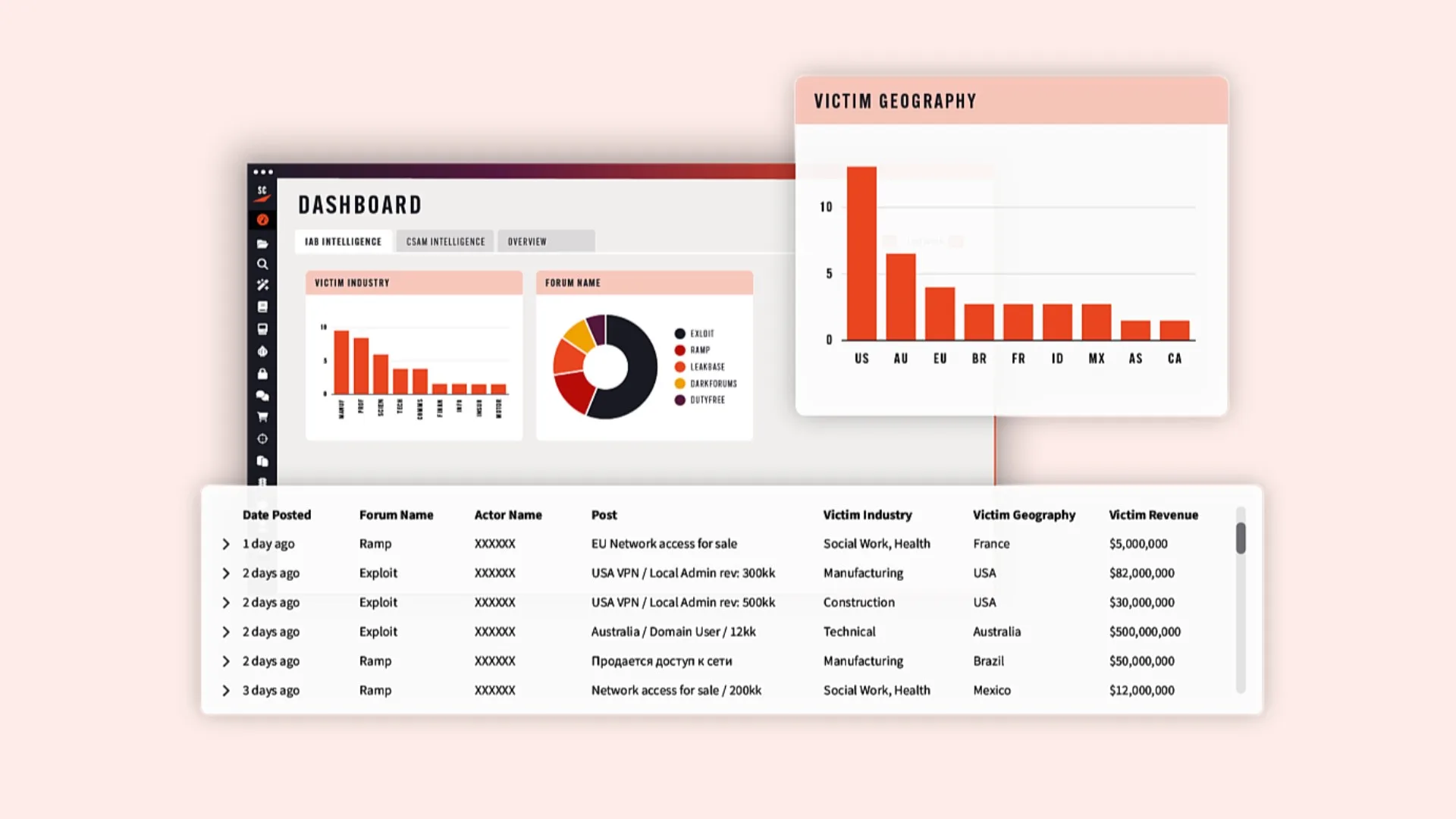
Within the victim search tab in the Ransomware Search and Insights Dashboard, Searchlighters can now search and set alerts to identify file names that may contain sensitive documents, files, and intellectual property belonging to your organization that have been leaked, ranging from roadmaps and financial reports to PII. Keyword search also enables alerting on organization-specific variables, for example:
- Finance Report Searchlight Cyber 2025
- Finance Report SL Cyber 2025
- Finance Report SLC 2025
Early success stories
Although this feature has only just been released to Searchlighters, during testing, our Threat Intelligence team was able to use the Ransomware File Explorer to identify a database containing over 300GB of personal data records belonging to a major sportswear manufacturer, and preemptively alert them to this potential breach.