In this blog we look at the growing threat of hacktivists, their attack methods, and how businesses can protect themselves.
What are hacktivists?
Hacktivists are a specific type of hacker (or, more typically, a group of hackers) that choose their targets based on factors such as geopolitics, religion, social issues, race, or other values. They often work to promote issues related to freedom of speech, human rights, or information ethics.
These groups primarily use chat applications such as Telegram, which have a lower barrier to entry than dark web forums and much broader reach, which means that the hacktivists can gain a larger following. They use their Telegram channels to organize their activities, disseminate information that supports their ideologies, and publicize their attacks.
They have always been a part of the underground landscape, but the wars in Eastern Europe and the Middle East have certainly contributed to notable hacktivist activity taking place in recent years, in parallel to the physical conflicts. A recent report by Orange revealed that one prominent pro-Russian hacktivist group targeted Europe – primarily Ukraine, Czech Republic, Spain, Poland, and Italy – with 96 percent of their attacks, marking the region as their primary focus. The report also shows that Europe is the second most impacted region by cyber extortion, with victim numbers increasing by 18 percent year-on-year.
In this blog we examine what the hacktivism threat means for businesses.
How are hacktivists a threat to organizations?
While most hackers and cybercriminals are driven by financial gains, hacktivists are driven by ideology, which makes the outcome of their actions unpredictable and potentially more damaging. For some hacktivists, the goal is to destroy data or disrupt business continuity. They may use ransomware or deface a business website to convey their message. Hacktivists seek to draw attention to their cause, so they want the targeted victim to know they are unhappy with the business or government’s actions. Website defacement publicizes the hacktivist’s message, and ransomware installation destroys company productivity.
DDoS and the disruption of operations for staff and customers
DDoS is a tactic used by hacktivist groups to overload computer systems and crash company websites using multiple devices, with the aim of degrading its performance or even making it completely inaccessible.
DDoS attacks are more effective than attacks from a single source because they generate more attacking traffic. The fact that traffic is spread across many sources also makes it harder to distinguish attacker traffic from legitimate traffic. This makes incident response and remediation a longer and potentially slower process, incapacitating the organization for an extended period of time. This type of attack disrupts business continuity, and a strong DDoS attack can persist for days, impacting revenue when the organization cannot process payments or fulfill customer requests.
Data leaks and reputational damage
Hacktivists may use doxxing or data leak attacks to expose sensitive information, such as internal communications, customer data, or classified documents. These attack methods are based on the fact that hacktivists can hack into organizations’ systems and weaponize the information against them. The outcome of these attacks can lead to embarrassment and reputational harm. Even if the technical impact of an attack is minimal, leaking internal practices or policies can cause long-term and lasting damage.
Defacement
Defacement is a type of website vandalism where an attacker finds a way to modify the contents of an organization’s website without their permission. They’ll change the contents of the website to something intended to embarrass or air their grievances about a business.
Website defacement attacks differ from other “traditional” cybersecurity threats because the hacktivist rarely stands to gain from the action unlike ransomware campaigns. Instead of stealing user credentials or taking money from organizations, hacktivists are trying to make noise and draw attention to their message.
Examples of hacktivists groups and attacks
With hacktivism a growing threat, as per the report by Orange, there have been some notable hacktivist groups and cases.
Noname
Noname is a pro-Russian hacktivist group that was formed in March 2022 and claimed responsibility for over 6,000 cyberattacks on Ukrainian, American and European government agencies, as well as media and private companies. Noname is an unorganized and free pro-Russian activist group that exists to attract attention in Western countries and silence organisations the group deem to be anti-Russian.
Local authorities across the U.K. became the latest of Noname’s targets in 2024. A number of councils up and down the country were affected by DDoS attacks, which flooded their websites with traffic and caused disruption to their services.
A statement from “NoName057(16)” on X published details of the DDoS campaign which it claimed was retribution for British military support for Ukraine. “The Russian embassy in the UK has accused the British authorities of using the issue of grain corridor protection to conceal arms deliveries to the Ukrainian Armed Forces,” it wrote.
“While the Russophobic UK authorities continue to sponsor the criminal Kiev regime, we are launching our attacks on that country’s websites.”
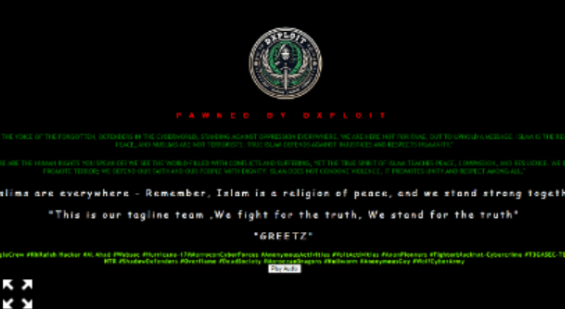
DXPLOIT
DXPLOIT is a hacktivist group that has been carrying out website defacement attacks, with a focus on spreading ideological messages. They claim to advocate for justice, human rights, and the peaceful representation of Islam. Their attacks combine technical skills with a clear agenda, often targeting high-profile websites across multiple industries and countries.
In December in 2024 DXPLOIT defaced the website of OneStep Disability Services.
The defaced website of OneStep Disability Services
The message on the website read: “WE ARE THE VOICE OF THE FORGOTTEN, DEFENDERS IN THE CYBERWORLD, STANDING AGAINST OPPRESSION EVERYWHERE.
“WE ARE HERE NOT FOR FAME, BUT TO UPHOLD A MESSAGE: ISLAM IS THE RELIGION OF PEACE, AND MUSLIMS ARE NOT TERRORISTS. TRUE ISLAM DEFENDS AGAINST INJUSTICES AND RESPECTS HUMANITY.”
After being alerted to their defacement of their website by the press, Onestep were able to contact their hosting provider and restore their website.
Counteracting hacktivist threats
Hacktivism is a growing threat, especially with the changing geopolitical landscape. While many public sector organizations will expect and plan for threats from hacktivists, businesses in the private sector may not have historically considered themselves to be targets. This threat requires security teams to add a new dimension to their toolkit so they can prepare for attacks such as DDoS, website defacement, and doxxing, which may not have been considered high-risk attack types before now.
Threat intelligence tools allow organizations to access the parts of the internet where hacktivists are active, whether that be the dark web or encrypted communication channels such as Telegram. Having a window into a hacktivist group’s world allows organizations to analyze the capabilities and assess the threat of hacktivists operating on the dark web in real-time.
The intelligence gained from these tools provides valuable and actionable insights on particular hacktivists by reviewing previous posts linked to an alias, finding associated profiles on other dark web sites, and assessing links to other hacktivist groups. This intelligence allows security professionals to understand the threat, identify the groups that are most likely to target them, and prepare their defenses for the tactics specific groups use.
Protect your organization from the threat of hacktivists
As hacktivist movements grow, so must the defenses used against the potential threat. By leveraging threat intelligence tools cybersecurity teams can gain deeper insights into the motives and methods used by hacktivists.