Read this blog from our CEO Ben Jones to learn more about how cybercriminals use the dark web this Cybersecurity Awareness Month.
Cybersecurity Awareness Month
This Cybersecurity Awareness Month we’re focused on raising awareness and understanding of the dark web – a part of cybersecurity that is much discussed but often misunderstood or misrepresented.
Almost everyone knows that the dark web is home to a vast array of criminal activity and cybersecurity professionals in particular are aware that there are threats on the dark web that could impact their business.
However, we often find that people are unclear on exactly how the dark web works, how cybercriminals use it, and – most importantly – how cybersecurity professionals themselves could be using it to gather intelligence on their adversaries.
Increasing understanding of the dark web is important because it is precisely these knowledge gaps that have allowed the dark web to become the domain of cybercriminals, where they believe they can act with impunity. In this blog I’ll cover some of the fundamentals that every cybersecurity professional should know about the dark web. Let’s start with the basics:
What is the dark web?
People often use “the dark web” as a catch all phrase for malicious sites on the internet but the real definition is slightly more technical than that because, in reality, there are a lot of malicious websites on the clear web (what is commonly thought of as the “regular” internet) and deep web (websites that aren’t indexed on search engines) as well.
The largest and most active dark web can only be accessed with specialist software, The Onion Router (Tor). Tor is an internet anonymizing protocol that allows users to browse websites – and to host sites – while concealing their identity. These anonymously hosted sites (also known as “Hidden Services” or “Onions”) make up what is commonly known as the dark web.
Read our blog How Tor Works for the technical details of how this anonymity is achieved.
What’s the Relationship Between the Dark Web and Cybercrime?
The anonymity of the dark web has made it attractive to all types of criminals, who believe that it is a “safe haven” where they can operate out of reach of law enforcement. This includes cybercriminals.
In fact, over the past decade the dark web has become a fundamental part of the cybercriminal ecosystem. Hacking communities use dark web forums to communicate with each other, choose their targets, and plan their attacks. They have established dark web marketplaces where they buy and sell everything from malware, to exploits, and stolen data. And they use the dark web to host and obscure the technical infrastructure they use to conduct their attacks.
What Cybercriminal Activity Takes Place on the Dark Web?
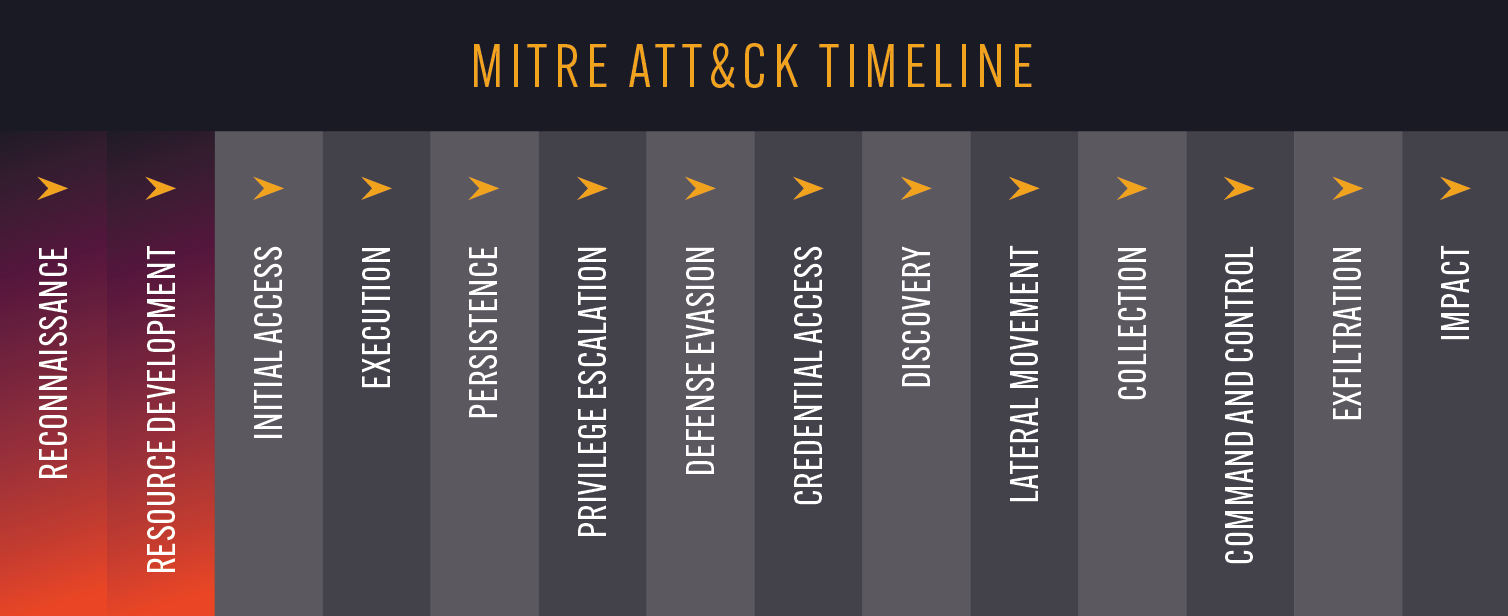
The most common activities we observe on the dark web fit into the categories of “cybercriminal reconnaissance” and “resource development”, the two tactics right at the start of MITRE ATT&CK’s enterprise matrix:
The reason behind this is simple: this is the part of the “Cyber Kill Chain” where cybercriminals need to collaborate and communicate. Once they’re on their target’s network they can execute their objectives without making much noise but before that point they often have to stick their head above the parapet. For example, we routinely observe:
- Cybercriminals buying and selling malware – for example, Remote Access Trojans, Botnets, and Infostealers.
- Initial Access Brokers – who (as their names suggest) specialize in selling access points to a company’s network, which could be as simple as admin credentials but other common types including webshells, remote network access, and SQL injections.
- Insider threats – either with cybercriminals trying to recruit employees on dark web forums, or employees actively reaching out to criminal gangs to offer their services in conducting attacks.
- Infrastructure reconnaissance – where cybercriminals share all the technical information they have gathered on a target ahead of an attack and scan ports from the dark web to identify potential vulnerabilities.
- The sharing of educational materials for conducting cybercrime – ranging from guides to conducting phishing attacks, to detailed information Operational Technology systems.
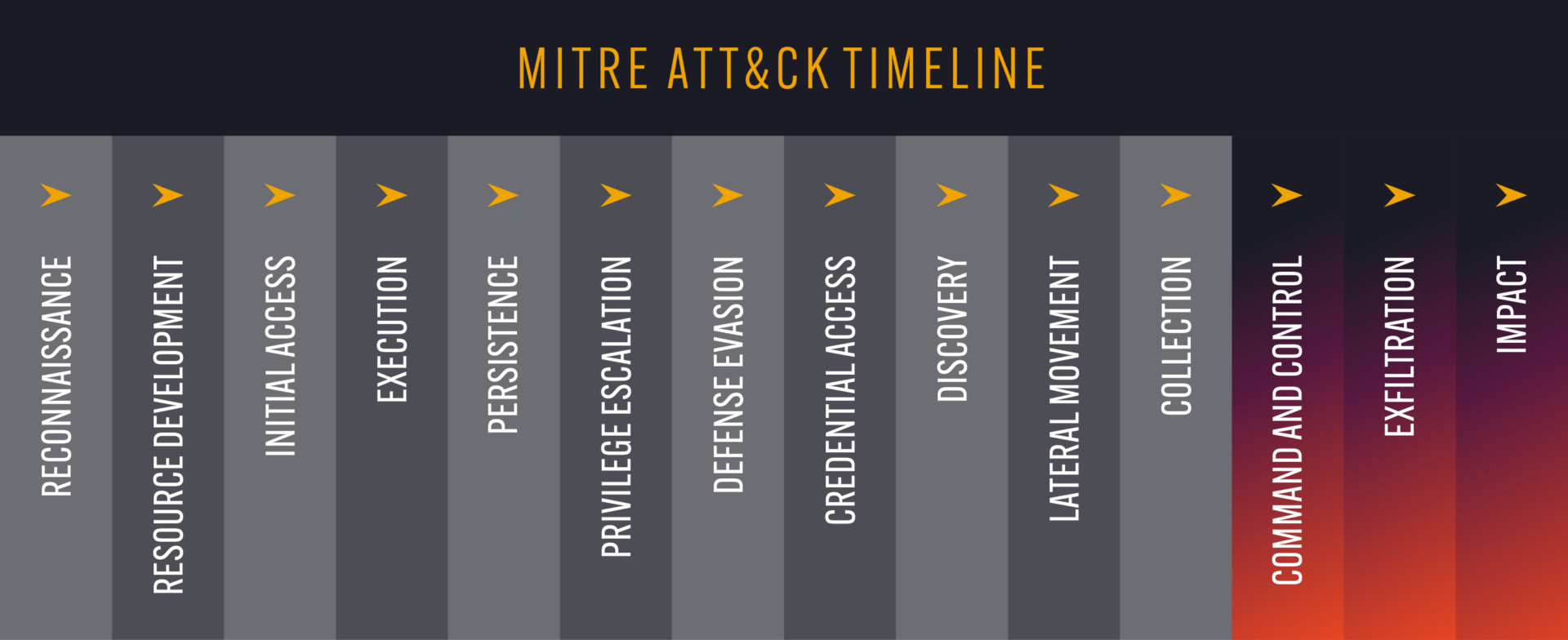
The other cybercriminal activity we observe takes place right at the other end of the “Cyber Kill Chain”, illustrated by the final phases of the MITRE ATT&CK Framework:
- Command and Control – as previously mentioned, many cybercriminal gangs use the dark web to mask their infrastructure, including Command and Control servers.
- Exfiltration – once data is exfiltrated it usually makes its way to (you guessed it) the dark web, where it is put on sale to the highest bidder.
- Impact – while most of the impact of a cyberattack is felt on the company network, ransomware groups in particular use the dark web as part of their attack, as a place to apply pressure on their victims and to try and extort a ransom in return for not leaking or deleting the data they have seized.
How Can the Dark Web be Used to Improve Cybersecurity?
With an understanding of how and why cybercriminals use the dark web, organizations can then start to think about how they can use this information to their advantage. Remember, in effect, this is a moment when cybercriminals are exposed. They’re using the dark web to limit the risk of being identified by law enforcement but they are forced to provide key information, for example on their target victims, on the tools they are using, on the cybercriminals they associate with, on their preferred methods of access, and more. This intelligence is gold for security professionals.
As a starting point, organizations looking to improve their cybersecurity should:
- Monitor the dark web for signs of cybercriminal reconnaissance – where there is a key window of opportunity when they can prevent the incident altogether if they can identify the early warning signs of a cyberattack.
- Monitor the dark web for signs their network has already been breached – such as a leaked company database appearing on a dark web marketplace, a ransomware group listing the organization on their leak site, or network traffic going from a company device to Tor (which is an indicator that a Command and Control Beacon has been established).
- Use the dark web to gather threat intelligence on their adversaries – the dark web is an invaluable first party collection source on how cybercriminals operate, their capabilities, and the potential risk they pose to your organization.