
Bookmark this quick reference guide for everything you need to know about the dark web. covering: how the dark web works, how threat actors target finance companies on the dark web, and defense strategies for financial institutions.
According to recent research, 63 percent of financial institutions experienced an increase in destructive attacks in 2022, a 17 percent increase on the previous year.
Unfortunately, banks have always been prime targets for cybercriminals because:
- They handle huge sums of money (great for big payouts).
- They hold huge amounts of data (which can be sold or encrypted in a ransomware attack).
- They have a vast attack surface to exploit (especially since the explosion of digital banking).
In this short guide, we’ll explain what the dark web is, how it works, and give advice on how to effectively communicate the importance of dark web intelligence to senior executives in your organization.
What is the Dark Web?
The dark web refers to a part of the internet that is inaccessible through regular search engines or internet browsers. It is notoriously associated with illegal activity that is intentionally hidden to avoid scrutiny from law enforcement, governments, and other entities like internet service providers.
Websites on the dark web network Tor are called onions or hidden services. These domains end in .onion, proceeded by a random combination of characters.
You might have seen the total internet represented as an iceberg before. In this metaphor, the deep and dark web are the bottom of the iceberg. These make up the unindexed parts of the internet, hidden out of sight, below the water line.
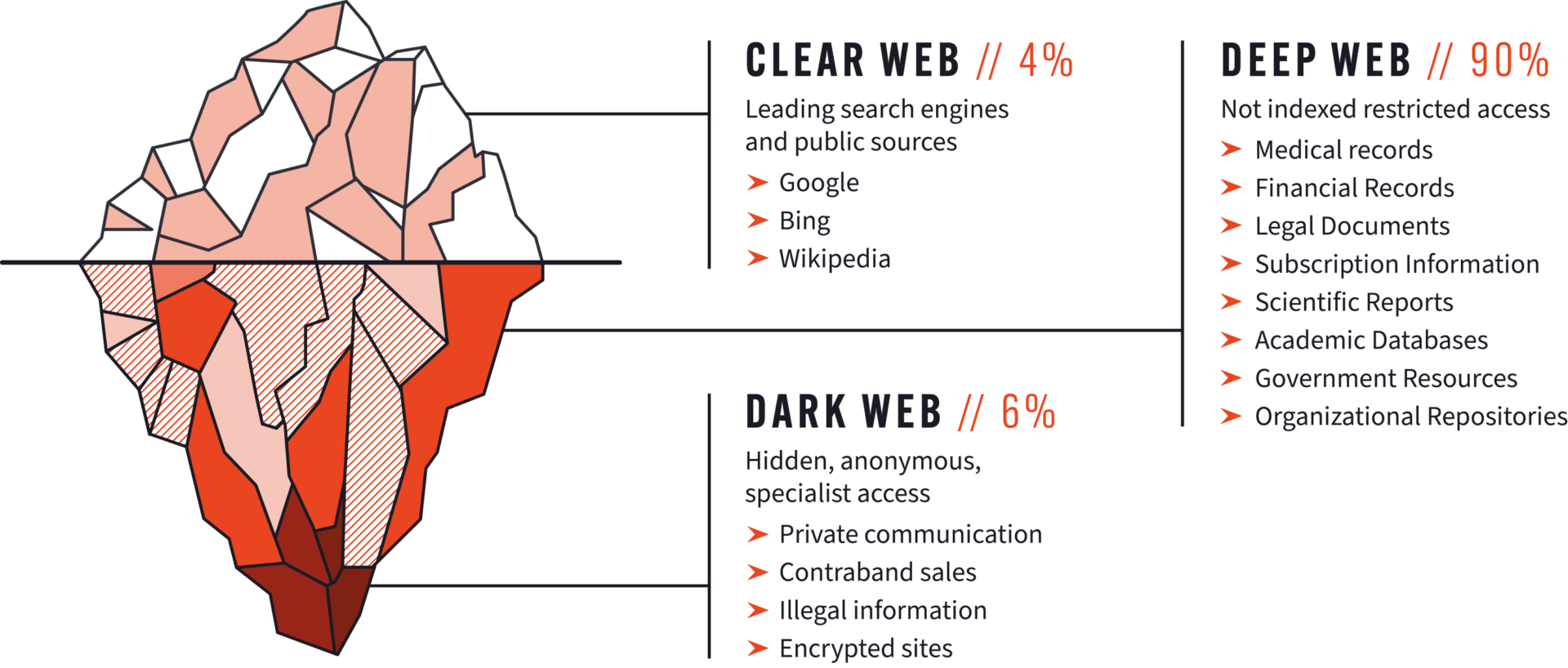
Related resources:
→ In this video our founders Dr Gareth Owenson and Ben Jones explain what the dark web is and how it works:
How does the dark web work?
To access the dark web you need specialist browsing software, such as Tor. Tor was originally developed by the US government for secure communications but is now run by a non-profit called The Tor Project.
Tor operates on the concept of “onion routing”, which involves data being relayed through a circuit of nodes. It’s a bit like an athletics relay race where you only know the identity of the person who handed you the baton and the person you’re passing it on to, but you have no idea where the race started or where it will end.
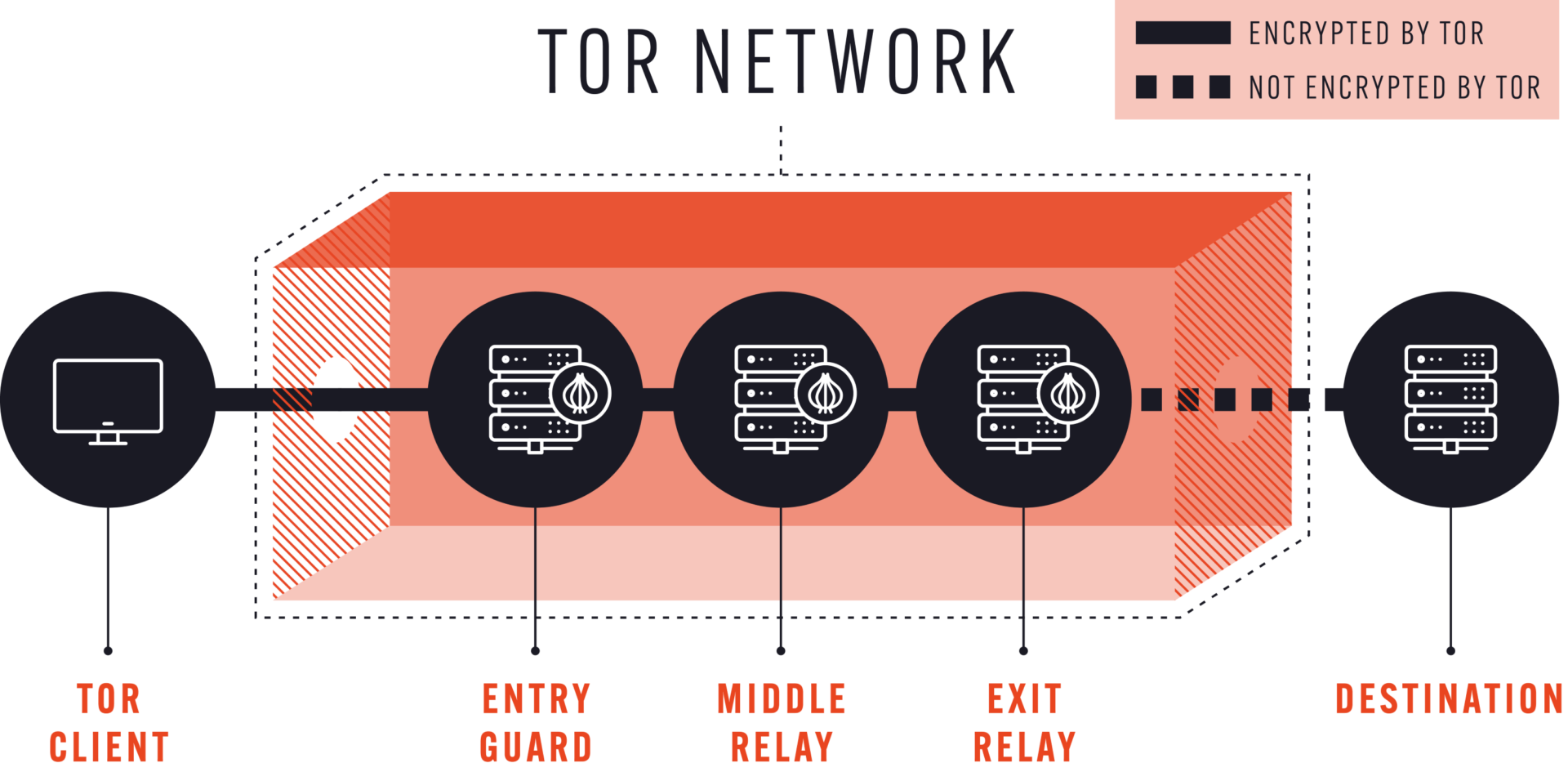
As illustrated in the above image, each relay only knows the identity of the previous and next node. With sufficient nodes, and wrapping each hop in a separate layer of encryption, it is possible to keep the identity of the user anonymous.
Related resources:
→ In this clip from our webinar “Defeating the Dark Web”, our CTO and world-renowned dark web expert Dr. Gareth Owenson explains how Tor works:
what is on the dark web?
The stated aims of the Tor Project are to create an anonymous environment that supports privacy and freedom of speech and the dark web can be used by people with positive intentions, including by whistleblowers and those residing under repressive regimes.
However, we know from our research that the vast majority of sites and activity on the dark web host illegal content. This encompasses various illicit activities such as drug sales, ransomware as a service (RaaS), the trade and dissemination of breached data, financial crime and fraud, and child abuse.
Related resources:
→ Visit our Dark Web Hub for an overview of marketplaces, forums, and ransomware leak sites on the dark web.
what are the biggest dark web threats against the finance sector?
One of the biggest and most persistent threats to banks and financial institutions is ransomware. The planning, initial access brokerage, and reconnaissance for these attacks often take place on the dark web or in encrypted chats using tools like Telegram. Research from FS-ISAC reveals that the finance sector is routinely in the top three most targeted industries by ransomware groups.
Our recent report Dark Web Threats Against the Banking Sector examined the most common threats against banks that can be observed on the dark web:
- Initial access brokers: Where threat actors are auctioning and selling vulnerabilities such as webshells, SQL injections, and remote network access. Our threat intelligence showed that this makes up the vast majority of dark web activity against the banking sector.
- Insider threats: Employees communicating with cybercriminals on the dark web to share sensitive data or offering access to the corporate network.
- Supply chain risk: Where cybercriminals target suppliers to impact multiple companies – as demonstrated recently by the MOVEIt breach orchestrated by the Cl0p ransomware gang.
Related resources:
→ Read the full report Dark Web Threats Against The Banking Sector
HOW CAN FINANCIAL INSTITUTIONS DEFEND THEMSELVES FROM DARK WEB THREATS?
With the knowledge that cybercriminal reconnaissance begins on the dark web, security teams at financial institutions should be using dark web intelligence to identify the early warning signs of attack, learn more about their adversaries, and inform their defenses.
Financial institutions should be continuously monitoring the dark web for attributes related to their organization’s external threat surface – such as domains, ports, IP addresses, employee credentials, software, devices, network components, and company datasets – to identify when they are being targeted by cybercriminals on forums, marketplaces, or messaging platforms like Telegram. This early warning from dark web monitoring gives security teams invaluable time to adapt their defenses based on likely threats and – consequently – a far greater chance of preventing costly cyberattacks.
Security teams should also be conducting dark web investigations to learn more about their adversaries, establish where the next attack is coming from, and how it might be conducted. This use of dark web data should form part of an intelligence-driven security strategy. For example, if a security team identifies an Initial Access Broker post on the dark web that could relate to their organization, a threat hunter could conduct a dark web investigation into the actor in order to find additional intelligence – such as any linked accounts, any email addresses, crypto-wallets etc., but also information about how the actor operates, which may be vital to pinpointing where the vulnerability may be. Security teams should use dark web intelligence to inform their threat models – the process by which potential threats can be identified, enumerated, and prioritized from a hypothetical attacker’s point of view.
Related resources:
→ You can read our guide to threat modeling here.
How do you communicate the value of dark web intelligence?
In our recent survey of CISOs, 99 percent of those at finance organizations said they were concerned about dark web threats. However, in spite of being acutely aware of the challenge, financial institutions have been slower in using intelligence from the dark web in their security practices. For example, only 23 percent of financial organizations are using the dark web to find leaks of customer data, and only 24 percent are using the dark web for threat hunting.
Often this comes down to explaining the value of collecting data from the dark web to senior stakeholders. In this final section, we’ll provide three ways security professionals can explain the value of dark web data:
1. advance warning of attack
If your executives were given advance warning of criminals targeting your supply chain or an employee leaking information to the dark web, would they expect you to act on it? I’m sure your phone would be blowing up with missed calls if this was the case.
Criminals don’t send courtesy emails before they leak sensitive data or compromise your network. However, dark web intelligence allows you to identify threat actors while they are in the “pre-attack” or reconnaissance stage of a cyberattack and take action before it’s too late. Knowledge of when a cybercriminal is targeting you, with what resources, and which vulnerabilities they are looking to exploit – is a hugely powerful resource for defenders.
2. shift left in Cyber defense
This “pre-attack” stage of a cyberattack is aptly described by two frameworks: the Cyber Kill Chain and the MITRE ATT&CK framework. Both of these can be effective tools for explaining to executives how dark web intelligence allows you to take action against cyberattacks earlier than most cybersecurity tooling is capable of. This can help demonstrate a change in strategy to your shareholders – as you move to preventing, rather than just mitigating cyberattacks.
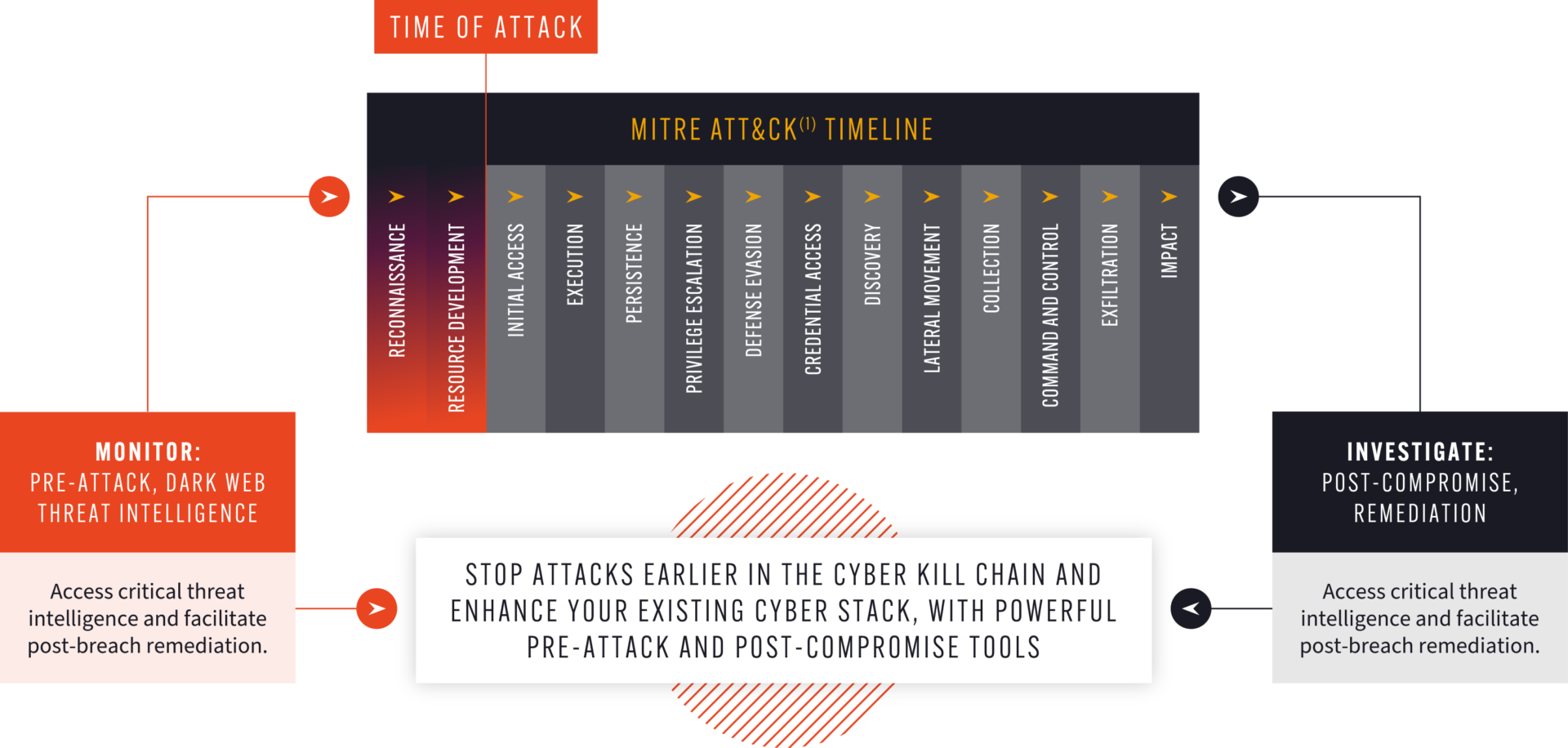
Dark web intelligence also has a role to play on the other side of the scale: providing incident response teams with crucial data on the events that took place outside of the network, in the run up to the attack. This can be used inform the remediation of an incident, or to gain visibility into the exposure of your vendors, suppliers, and interface partners.
3. the wedge of hindsight
The next step is to explain the benefits of “shifting left” in terms of time and cost savings to your business. Simply put, the earlier you can detect a threat, the less cost and damage there will be to your organization. We call this the wedge of hindsight:
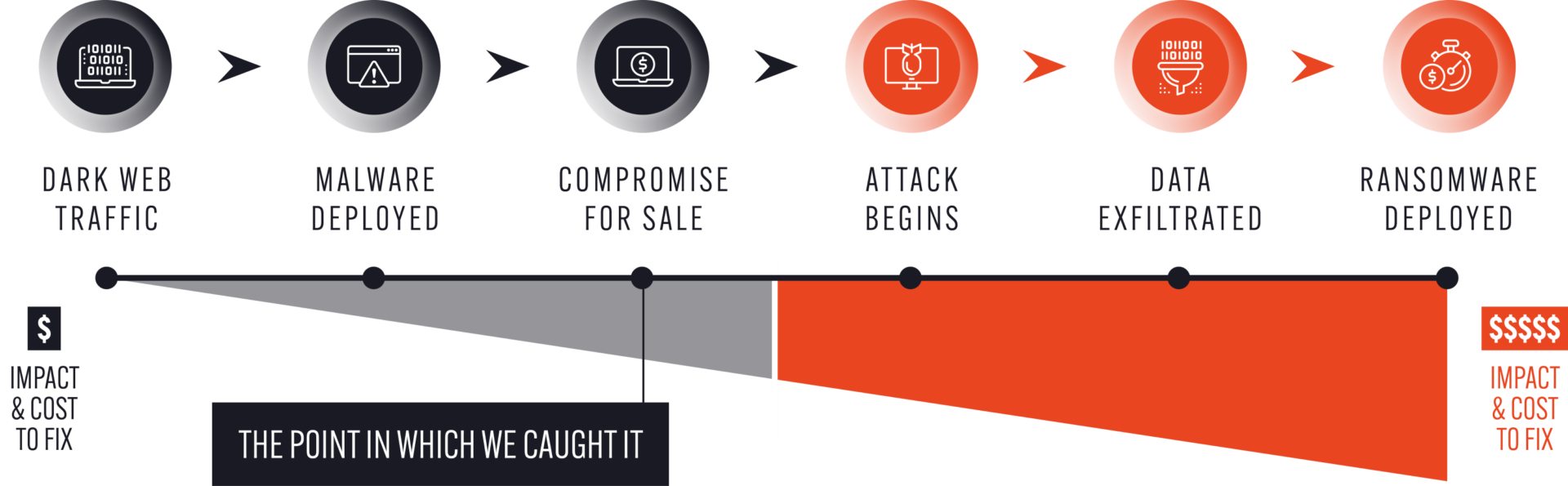
As a concrete example, we recently helped a government agency to mitigate a vulnerability based on our intelligence that their network was compromised by a webshell that a threat actor was advertising on a dark web forum. Consequently, the organization was able to neutralize the webshell and effectively stop the attack – and all its potentially negative consequences – before it happened.
Related resources:
→ Read our report Government Agency Targeted to learn about how we helped an organization spot and stop a threat actor before the cyberattack could be executed.
STRIKE BACK AGAINST CRIMINALS TARGETING THE FINANCE INDUSTRY ON THE DARK WEB
Want to learn more about how dark web intelligence can be used to pre-empt and prevent cyberattacks? Visit our dedicated financial services page to learn more or book a demo with our experts today.




