Spot threats earlier with dark web monitoring by Searchlight Cyber
Automatically monitor the dark web for external threats and prevent security incidents against your brand, suppliers, and people.

The power of dark web intelligence
Criminals don’t send courtesy emails before they breach your network. But by monitoring dark web marketplaces, forums, and hidden chats, you can identify threat actors before they strike.
Know critical intelligence first and empower analysts to defend against:
Cyber risks
Get threat tailored alerts, including leaked credentials, open ports, code repos, and software vulnerabilities.
Criminal activity
Receive automated alerts when your brand or its employees are mentioned by threat actors or groups.
Hidden threats
Identify indicators of insider threats, the sale of initial access on hacking forums, ransomware group listings, and supply chain attacks.
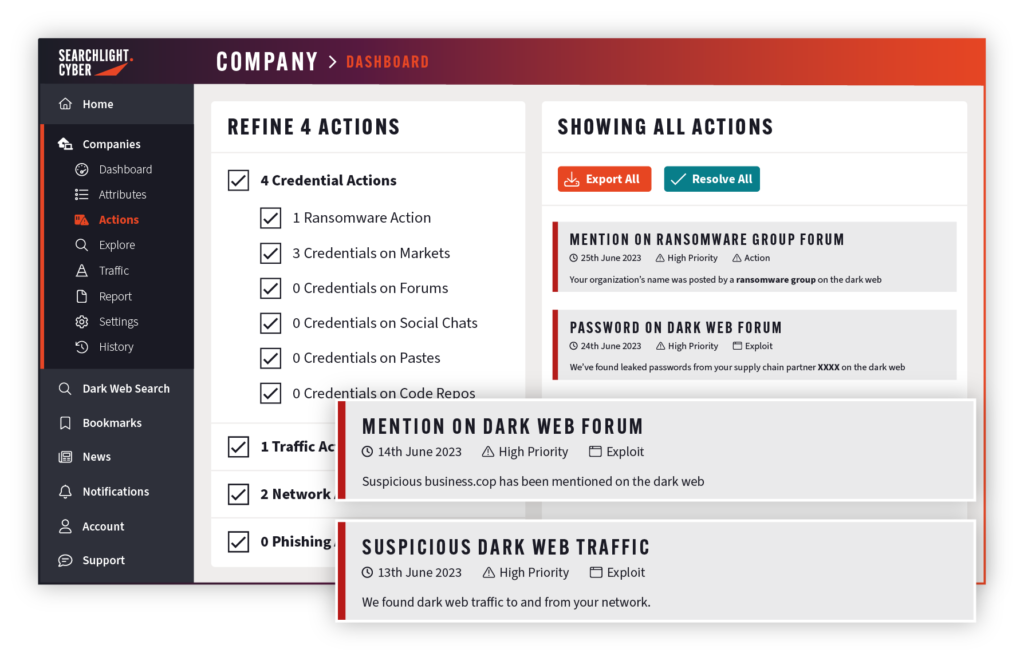
Identify imminent threats on the dark web
Be the first to know when cybercriminals on the dark web are targeting your company
Searchlight continuously monitors the dark web for hidden cybercriminal activity. Think of us like your automated analyst. We detect, categorize, and alert you to imminent threats such as software vulnerabilities, leaked credentials, and supply chain threats so you can take action against cybercriminals before they strike.

Spot anomalies in your network traffic
Monitor Tor traffic: A key indicator of malicious activity
Get agentless visibility into live and historical Tor traffic to and from your network. Searchlight’s proprietary technology helps security teams detect the telltale traffic patterns associated with malware installation, insider threats, and data theft.

Cutting-edge technology and Dark Web data
Analyst time-saving platform
Just enter your organization’s attributes, such as domains, IP addresses, and employee credentials, and Searchlight will automatically scan them against over 8 million dark and deep web records. Searchlight then categorizes and proactively alerts you to imminent threats against your organization – saving your analysts valuable time.
Benefits of dark web monitoring
Unlock Dark web intelligence for your organization
Automatically spot the earliest warning signs – including leaked company credentials, new vulnerabilities, or dark web chatter about you or a supplier on the dark web – before they impact your business.
Easy to deploy
Agentless deployment with our outside-in approach to data collection
Continuous monitoring
AI-powered scanning of your attributes, including domains and IP addresses
Actionable alerts
Increase SOC efficiency with prioritized alerts based on dark web intelligence
Trusted by the world’s most forward-thinking enterprises and cyber investigation teams
Excellent service. Great tool for breach investigation.
— Managing Director, IT Services Industry
(GARTNER PEER INSIGHTS)
Unique high-tech offering yet with people who are easy to work with.
— Security practice director, IT Services Industry
(GARTNER PEER INSIGHTS)
An amazing resource for conducting breach investigations.
— Digital marketing Analyst
(G2CROWD)

