Our latest report looks at the most common threats we observe against the banking sector on the dark web – including Initial Access Brokers, insider threats, and supply chain attacks.
new banking sector report
Today we’ve published our latest threat intelligence report: Dark Web Threats Against The Banking Sector. This research contains a multitude of examples of observed activity against the banking sector and provides guidance on how this dark web intelligence could be used by defending teams to protect their organizations from cyberattacks.
You can download the full report here but these are the highlights:
key findings
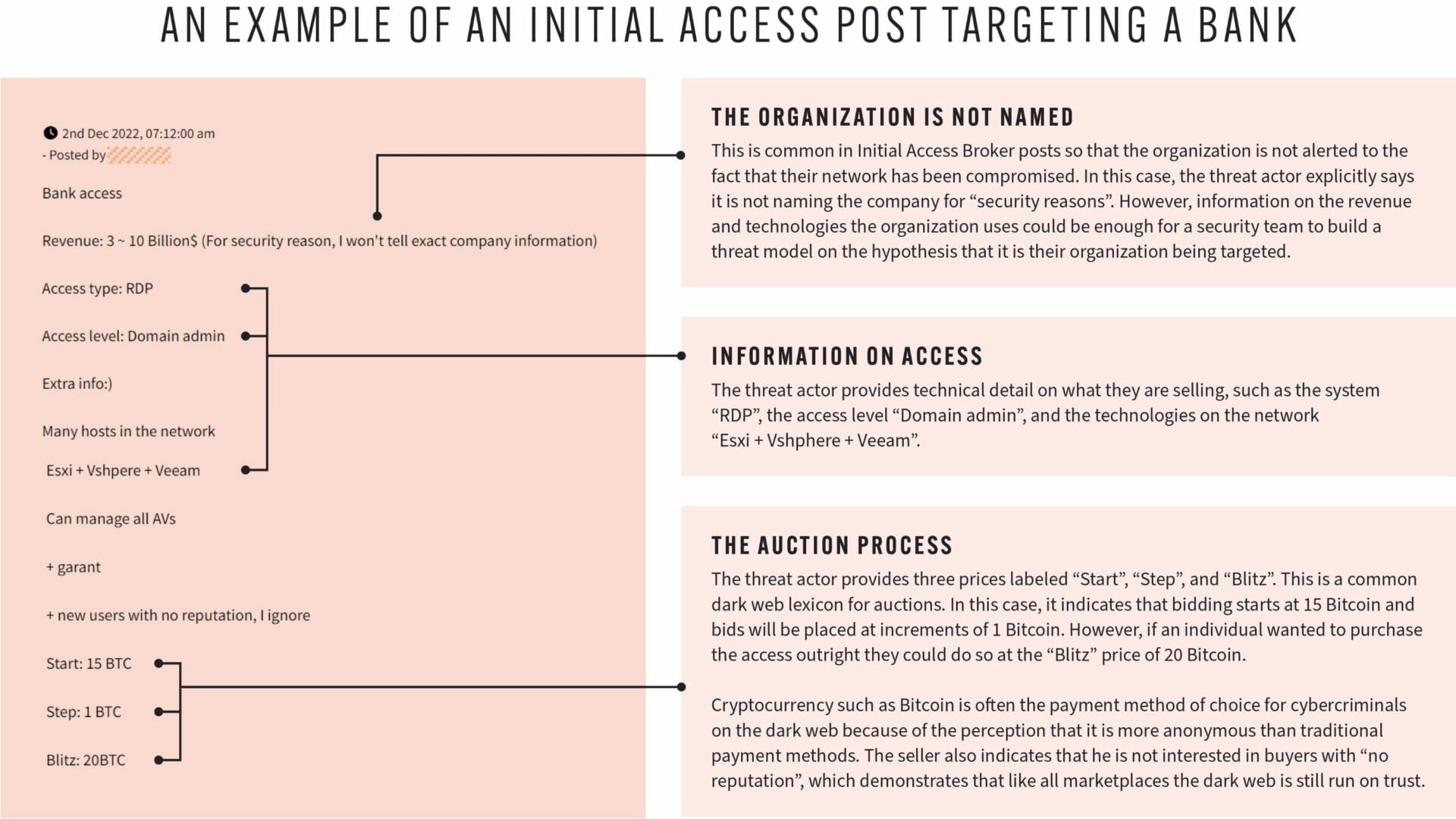
1. Initial Access Brokerage – where threat actors sell system access on forums – makes up the vast majority of dark web activity we observe against the banking sector.
This makes sense because Initial Access Brokers have a clear incentive to post on the dark web: they need to sell their goods. The report includes a number of examples of different types of access being sold on dark web forums such as Exploit, XSS, and BreachForums. Most commonly: remote network access, webshells, remote code execution, and SQL injection.
These communications between sellers and buyers provide cybersecurity professionals with a valuable opportunity to learn about potential attackers and their capabilities. It can also provide them with an “early warning sign” if they match the profile of the target, based on the information threat actors provide in a post. See the example below:
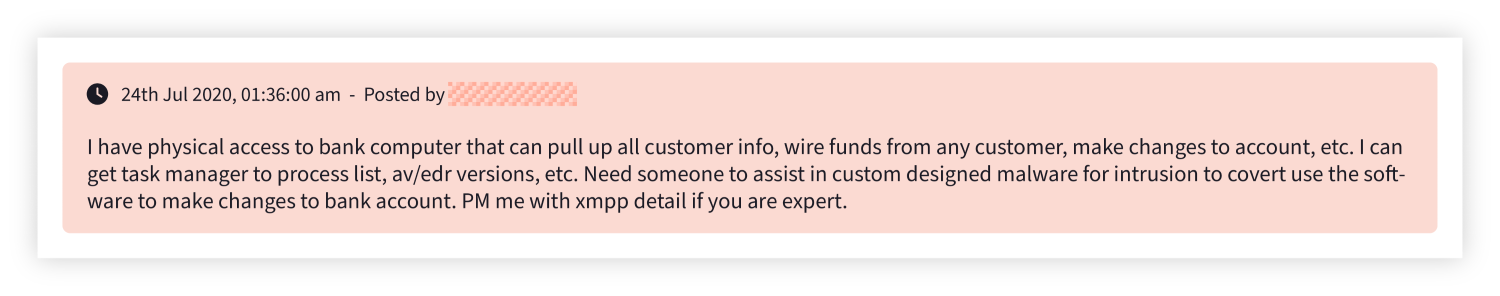
2. Insider threats within banks can be observed on the dark web.
For the purposes of this report when we say “insider threat” we aren’t talking about accidental employee malpractice. We are focusing on malicious insiders who are intentionally looking to compromise the organization from within.
This is an activity we observe frequently against banking sector organizations and there are two main opportunities to spot it: when employees with access advertise it on the dark web, or when threat actors try to recruit malicious insiders. Our report includes examples of both and explains how a security team could use this intelligence to build threat models around the hypothesis that the employee is within their organization.
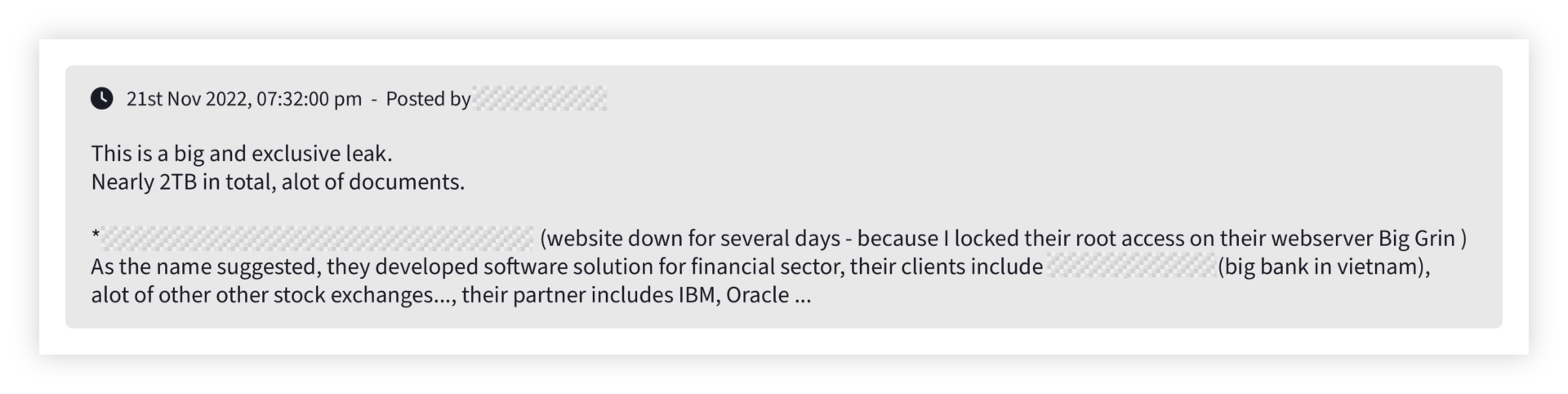
3. Infrastructure reconnaissance – including cybercriminals targeting banks through their supply chains.
In the reconnaissance stage of a cyberattack, threat actors go through a process of gathering as much data as possible on their victims to identify potential weaknesses and create an effective attack strategy. This can include information about the network topology, operating systems and applications, and user accounts.
Often this reconnaissance leads them to an organization’s supply chain as the initial point of compromise and it is no mystery why. Most banks will have very large, very complex supply chains and extremely little visibility into the cybersecurity that their suppliers have in place because it is outside of their own infrastructure. This makes it a potential point of weakness.
However, monitoring the dark web for the details of key suppliers can help organizations to gain visibility into potential threats by identifying when they are being targeted by threat actors. For example, our report includes a threat actor attempting to sell the source code of a software supplier to several banks. The criminal uses both the name of the supplier and names several banks who use their software.
From the perspective of a security team, this early warning that a supplier is being targeted could help them to quickly determine whether they are vulnerable. In the scenario that they do use the supplier, they now have valuable time to put additional security measures in place before the source code is sold or a threat actor has time to use it to target their organization.
gathering pre-attack intelligence
While this activity – and the dark web in general – sounds scary, the point of this report is not to alarm. In fact, it’s to demonstrate the opportunity the dark web provides to security teams to identify threats and stop follow-on actions using data collected from the dark web, before the criminals launch the attack on their network.
Banks are always going to be a target for threat actors. What can change is how banks meet this threat. With dark web intelligence that alerts them to potential malicious activity while criminals are still in the “pre-attack” stage of their operations, security teams can adjust and improve their defenses based on what might happen in the future – not just respond to things that have happened in the past.