we explain the systems put in place by hacking forums to facilitate trust and cooperation between threat actors
Who uses hacking forums?
Hacking forums have been around since the early 2000s. Most of them were created as a safe place for the cybercriminal community to discuss new techniques, share tips, learn new tricks, and generally keep up to date with anything that is not commonly discussed on mainstream websites.
Members of these forums are either “hackers”, a term that is not derogatory in its essence and refers to computer enthusiasts who have the capability to find their way through systems by using atypical means, or “threat actors”, who are hackers that use their skills for malicious purposes.
One of the main benefits of forums for threat actors is that it allows them to monetize their work – most threat actors are financially motivated, after all. As well as allowing a space to discuss tactics, many hacking forums also offer a marketplace section. Sounds like a straightforward setup for a functional cybercriminal community, right? Not exactly.
no hacking forum utopia
One of the main differences between hacking forums and mainstream forums is anonymity – users create an account using a handle of their choice and verification of identity is virtually non-existent. This enables the cybercriminal element to trade goods of an illicit nature, but also means that a significant number of scammers lurk around forums looking to deceive other members.
Consequently, forum administrators have had to implement measures to help serious buyers and sellers to identify the likelihood of being scammed. Again, some of these measures are common-stay on other types of forums, such as reputation points and forum rankings, so can be quickly implemented and easily understood. Other methods are more unique to hacking forums, such as cryptocurrency deposits and escrow services.
reputation scoring on hacking forums
The methodology of reputation scores differs from hacking forum to hacking forum. Therefore, an actor with 50 positive reputation points on Exploit isn’t necessarily less trustworthy than an actor with 350 reputation points on Cracked. To demonstrate this point, we are sharing two examples of actor profiles on two different forums.
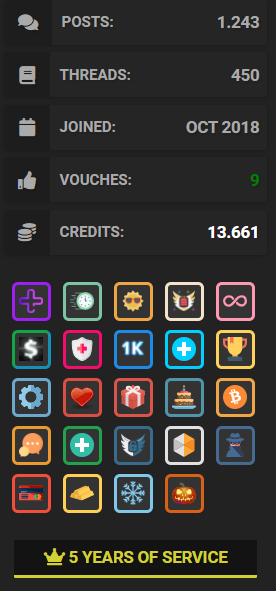
Figure 1: The profile of Fraudlash, a threat actor on the hacking forum Cracked
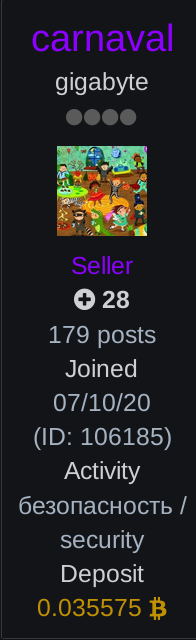
Figure 2: The profile of carnaval, a member of the Exploit hacking forum.
A like-for-like comparison of the two suggests that Fraudlash (Figure 1) would be the more reputable individual, with 1,135 reputation points compared to carnaval’s 28 (Figure 2). However, there are a lot of competing factors to be considered.
Firstly, Cracked forum allegedly has about 4.5 million registered users, while Exploit only has just above 62,000, meaning that higher scores are to be expected thanks to the larger user base. This is especially skewed because Cracked members with upgraded account packages can award up to six reputation points to a user, while on Exploit only one point can be awarded by a user, per post.
Secondly, as Figures 1 and 2 demonstrate, forums use a variety of figures and methods alongside reputation scores to indicate credibility.
Cracked has a number of statistics against the user profile that signify different things:
- Users that have made more than 15 posts can “Vouch” for an individual, which (allegedly) means that they have tried and tested a seller’s product.
- Users can also give “Likes” but this is often abused and given without proper testing of the product, so isn’t a trustworthy barometer for choosing a vendor to buy from.
- Users can also pay to upgrade their accounts on Cracked, which makes them appear more credible. Free accounts are available, “Premium” accounts are purchased for EUR 9.99, and “Supreme” accounts for 59.99. The light blue color of Fraudlash’s handle indicates that this is a Premium account.
The Exploit hacking forum has a completely different approach to Cracked to verify the credibility of users:
- Users have to pay US $200 to join Exploit, which already represents a filter for scammers as well as a barrier to entry to less serious threat actors.
- Exploit also offers a two-tier closed section that only active members have access to. The first level of access is obtained by making at least 50 forum contributions in the form of comments or opening new threads. The second tier requires passing the first tier and the explicit recommendation of another second tier member, which is then subject to voting and administrator approval. This is the highest level of credibility and scamming at this level is extremely unlikely.
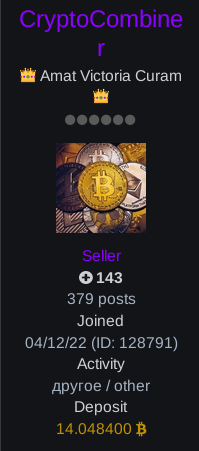
- Users can also deposit any amount of cryptocurrency, usually in the form of Bitcoins, which has no benefit other than to demonstrate how much money the user will forfeit if they are found to have scammed another forum user. As visible in Figure 2, the user carnaval has deposited 0.035575 Bitcoins, roughly the equivalent of US $2,391. As a more extreme example, actor CryptoCombiner (Figure 3) has deposited 14.048400 Bitcoins, roughly equivalent to US $944,400.
Figure 3: Another actor on the Exploit forum, whose profile indicates that they have deposited 14.048400 Bitcoins as security.
Finally, we have to consider the activity that awarded each individual the points they have earned. Fraudlash obtained their reputation by cracking and sharing various tools, including credential stuffing-enabling tools, stolen accounts and more, while carnaval obtained their reputation by actively buying initial access and is a known affiliate of a ransomware-as-a-service program. To some, carnaval’s 28 reputation points may therefore outweigh Fraudlash’s 1,135 reputation points, due to the complexity of carnaval’s activity.
escrow services within hacking forums
Another form of verification many hacking forums have implemented for the buying and trading of goods is escrow – the use of a middleman between the buyer and the seller. When using an escrow service, the money and the product are sent to the middleman, who is a trusted member of the forum – usually the administrator – who checks the product before releasing the funds. In exchange for the escrow service, the middleman takes a percentage of the transferred sum, which is sometimes as much as 10 percent, although this can vary based on the value and type of product.
Using an escrow service provides an extra layer of security when dealing with threat actors. Refusal to use the service is often not only perceived as a red flag but is also against the rules of many hacking forums, where not using the service may result in a ban.
However, there are limitations, as some trades cannot be verified due to their nature. There are also instances where scammers managed to trick the middleman by proving their product works, but only barely and not exactly like described in the initial deal.
Some hacking forums have explored ways of making the escrow process quicker by automating it, although often there is suspicion that this means the product isn’t checked properly (if at all). For example, the XSS forum provides an automated service but also provides a manual option for sensitive deals above US $50,000 in value. Actor profile data on XSS also indicates the number of successful transactions carried out by using an Escrow service (Figure 5), showing potential buyers that the seller has been reliable in the past.
Figure 5: Profiles on the XSS forum indicate how many successful escrow deals the seller has completed.
Other Methods for Assessing a Threat Actor’s “Legitimacy”
Beyond reputation scores and escrow services, there are a few other methods that some hacking forums administrators and members use to assess the “legitimacy” of a threat actor:
- Barriers to entry: Some forums have experimented with creating more stringent processes for creating an account in order to weed out scammers. RAMP forum, for example, is notable for requiring a $500 down-payment to sign up, although some actors are granted free access if they could prove they had an established reputation on “friendly” forums such as Exploit or XSS. Even more extremely, the administrator of the Kick Ass forum was known to hold private interviews with those looking to join the community.
- Arbitration: Some forums have “arbitrage” sections where someone who believes they have been scammed can petition the administrator of the forum to act as judge. The “victim” submits a scam report (also known as a “Black Report”), both parties are invited to share proof of their claims, and the administrator makes a decision. If the administrator finds someone at fault they are usually asked to either return the money or replace/fix the product. If they refuse they are immediately banned from the forum and their deposit (if present) is used to reimburse the accuser.
- Track record: Of course, beyond reputation scores, administrators and forum users also make judgment calls based on the historic activity of the person they are dealing with. For example, whether a seller has been posting in the “Knowledge” section of the forum, whether they’d previously asked for advice around developing the malware they are now selling, and whether they have interaction with other experienced actors. Buyers will often cross-check the seller’s contact information (such as Telegram usernames and Jabber IDs) against open sources or other forums to see if they have a reputation or have been accused of scamming elsewhere.
Understanding the hacking forum underworld
If there is one takeaway from this blog, it is that there is a huge divergence between the meaning associated with the numbers associated with profiles on different hacking forums. For the cybersecurity and law enforcement community, understanding the meaning behind these numbers – and generally how threat actors interact with each other – is more than just an intellectual curiosity. Knowledge of how these forums work, who the big players are, the types of goods they are selling, and who collaborates with who, are all important aspects of assessing the credibility of a potential threat.
This information can be critical, for example, if an organization observes an Initial Access Broker selling access to a business that matches the profile of their company (an activity we routinely observe on hacking forums). Their security analysts then need to assess the risk associated with the threat actor – asking questions like:
- Do they have a reputation in this or other forums?
- Are they linked to any notable cybercrime groups?
- Have they got a track record of selling access to other organizations?
- What are their typical TTPs?
- Who are they potentially going to be selling this access to?
In this scenario, understanding whether 28 is a good reputation score on Exploit – or not – can make all the difference in accurately assessing the threat and deciding whether to prioritize mitigating actions.