
our director of threat intelligence, jim simpson, gives his top tips on building a threat model.
WHAT IS A THREAT MODEL?
Threat modeling is a process by which potential threats can be identified, enumerated, and prioritized – all from a hypothetical attacker’s point of view. The intent is to provide defenders with a systematic analysis of the probable attacker’s profile, most likely attack vectors, and the assets most desired by an attacker. There are numerous advantages to threat modeling, including (but not limited to):
- Taking a more proactive approach to security by finding security vulnerabilities while there is still time to fix them.
- Saving time, revenue and the reputation of a company by preventing costly and embarrassing security breaches.
- Documenting all of the identified threats that the organization could face, to aid prioritization and risk assessment.
- Uncovering new intelligence and gaining awareness of the latest risks and vulnerabilities.
But where do security teams start? These are our five steps to creating a threat model:
1. identify the assets your adversaries are likely to target
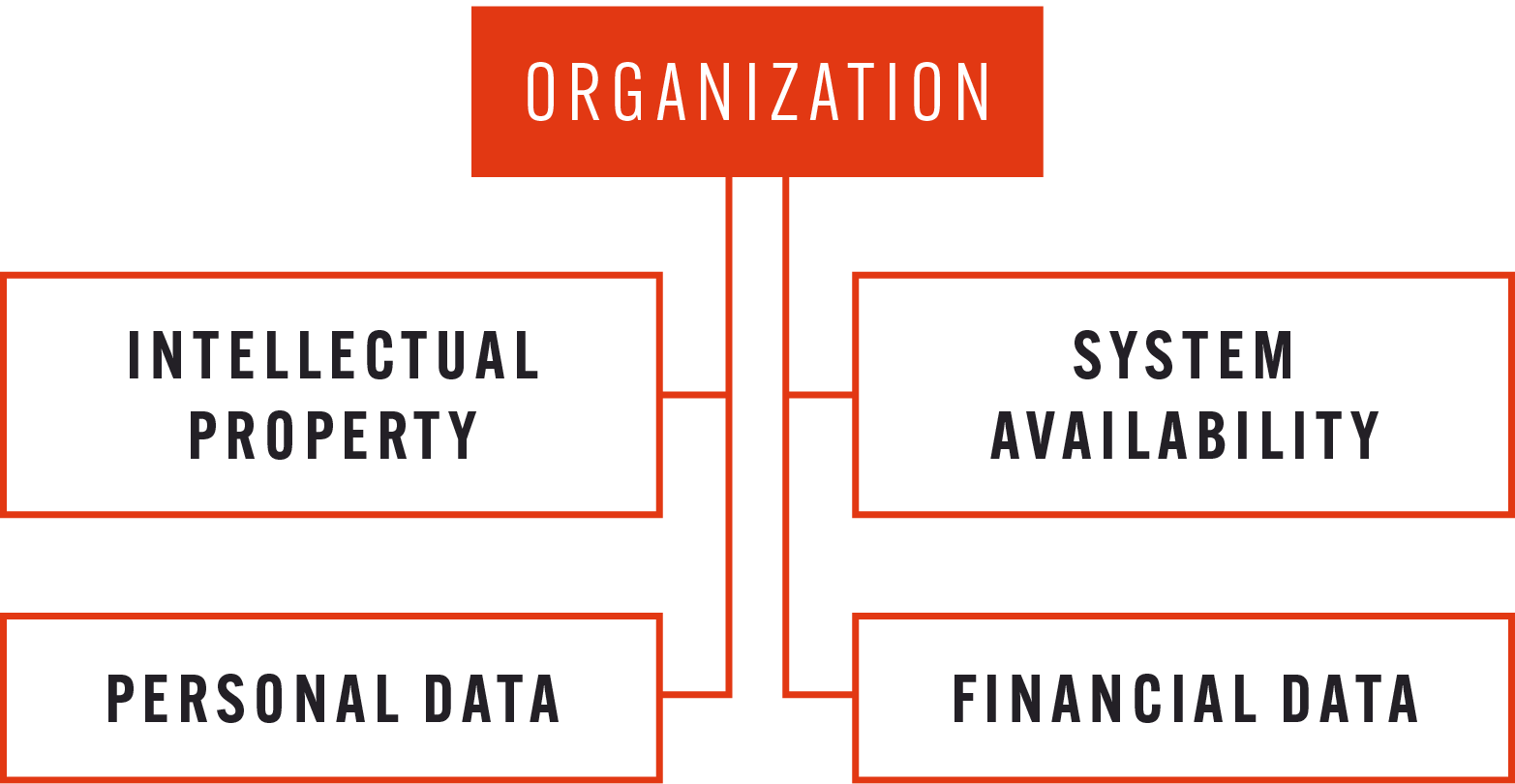
To start threat modeling, security teams first have to identify the “crown jewels”: the assets that need protecting. This is established by assessing the critical and sensitive systems and data within the business, and the assets that would be of most value to threat actors.
For most companies this will include customer data, employee data, financial data, intellectual property, and IT network information but each organization will be different. For example, critical national infrastructure organizations would need to factor in Industrial Control Systems (ICS), Operational Technology (OT) network information, and system availability.
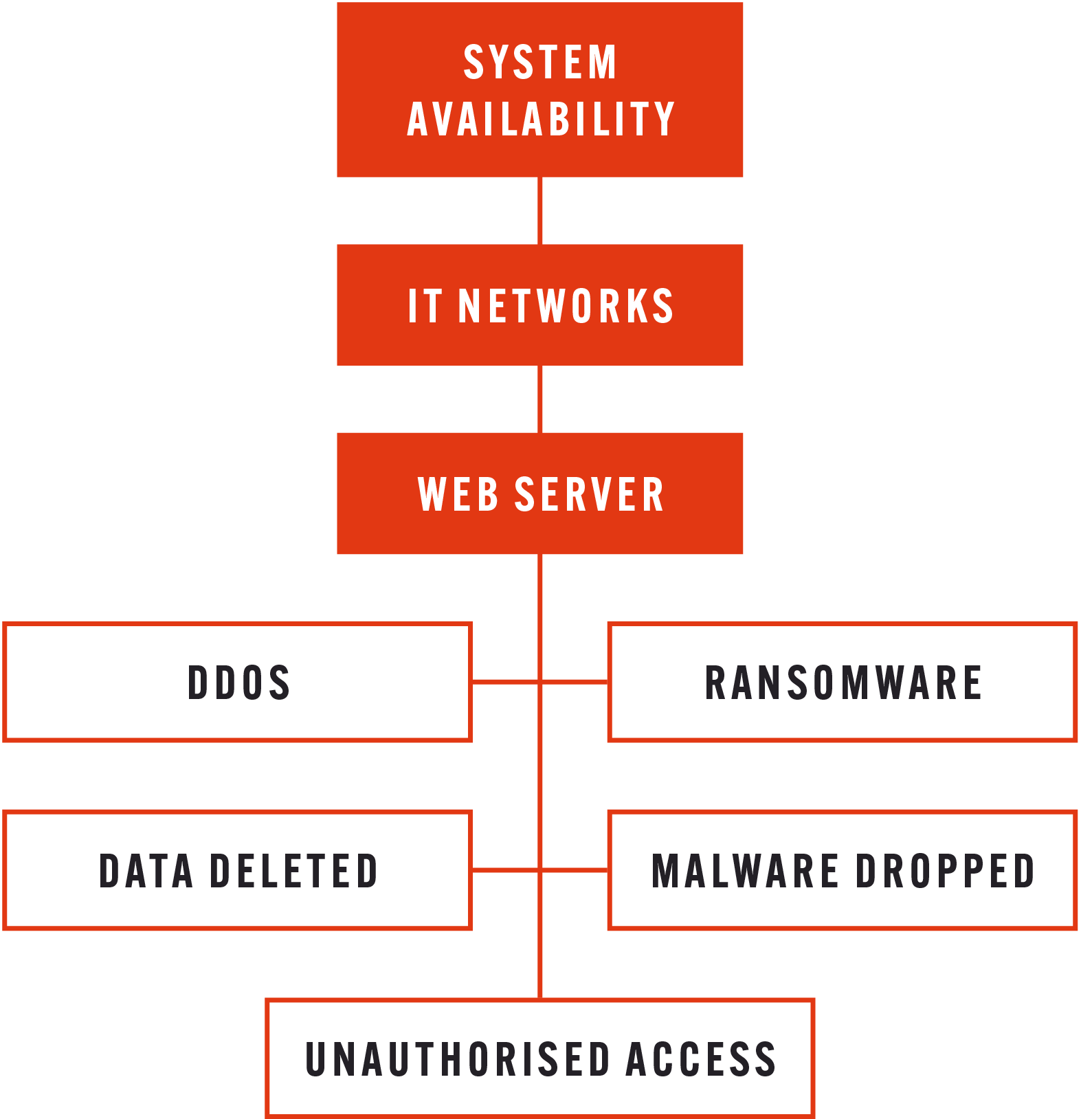
2. PIVOT OFF THE TARGETED ASSETS TO IDENTIFY AREAS OF WEAKNESS AND POSSIBLE COUNTERMEASURES
Once the “target information” has been established, security teams can break down how each asset may be attacked. The example shown is not exhaustive of all attack types and this is an exercise that needs to be continuously re-run to keep pace with the changing threat landscape.
3. ESTABLISH THE ADVERSARIES THAT TARGET THE SECTOR
Security teams then need to establish the threat actors that are likely to target the organization and their industry sector, as well as the Tactics, Techniques, and Procedures (TTPs) they use.
A combination of first party collection (i.e. threat intelligence gathered by the security team) and third party collection (i.e. open source intelligence – OSINT) can help establish the threat landscape including known threat actors, recent campaigns, and the techniques used. The MITRE ATT&CK framework is a particularly valuable asset for security teams trying to establish an overall picture of the threat landscape, and can be used as the starting point for the threat model.
Read this blog to find out more about where dark web intelligence fits into the MITRE ATT&CK Framework.
4. PIVOT OFF THE ADVERSARIES TO IDENTIFY TRIGGER EVENTS FOR THE ATTACK
This stage of the threat model looks at the “trigger event” that could lead a threat actor to initiate an attack. This may be the announcement of a new CVE in a software the organization uses, which provides the threat actor with a point of access. Or it might be tied to the motive of the attackers, for example a threat actor choosing to target a company around the announcement of its financial results. Building these events into the threat model helps organizations establish when they are most vulnerable.
5. CREATE AN ATTACK MAP
Finally, an attack map should draw together all of the components above to provide a holistic visualization of the organization’s specific threat landscape, including:
- The targeted Information;
- The types of attacks the organization is likely to face;
- The TTPs of the attackers;
- Detection opportunities with log sources that could be used to indicate any of the attacks you have determined might take place;
- And potential countermeasures that should be prioritized to prevent the most likely attacks.
AND REPEAT
Critically, threat modeling isn’t a “one-and-done exercise” – attackers change what they are doing, new actors join the party, some actors aren’t ever seen again. This means it is an ongoing requirement for security teams to gather threat intelligence (including from the dark web) and regularly (at least once a year) update the threat model to reflect how the threat landscape has evolved.




