Our recent webinar covered challenges facing SOC teams and how dark web intelligence can help them to identify threats earlier.
Dark web data for SOC teams
As part of our ongoing cybersecurity webinar program, we were thrilled to welcome trusted partner, DigitalXRAID to discuss how integrating dark web data into security operation center (SOC) teams can enhance intelligence and defensive capabilities. Here are five actionable takeaways from this session.
If you missed the webinar, here’s a link to the on-demand recording.
What are the most common threats seen by SOC teams?
Tony Batten, Lead SOC Engineer at DigitalXRAID opened the webinar by talking about the broad spectrum of organizations for whom his team offers managed security services. This ranges from central government and finance companies to international football/soccer clubs – essentially anyone with sensitive data that needs protecting from malicious actors. As someone who works with diverse organizations, Tony has invaluable insights into the most common threats and trends that cybercriminals are leveraging. In this clip, he gives a rundown of what these look like for his SOC and highlights the rapid rise of ‘quishing’, or QR phishing, as a growing security risk.
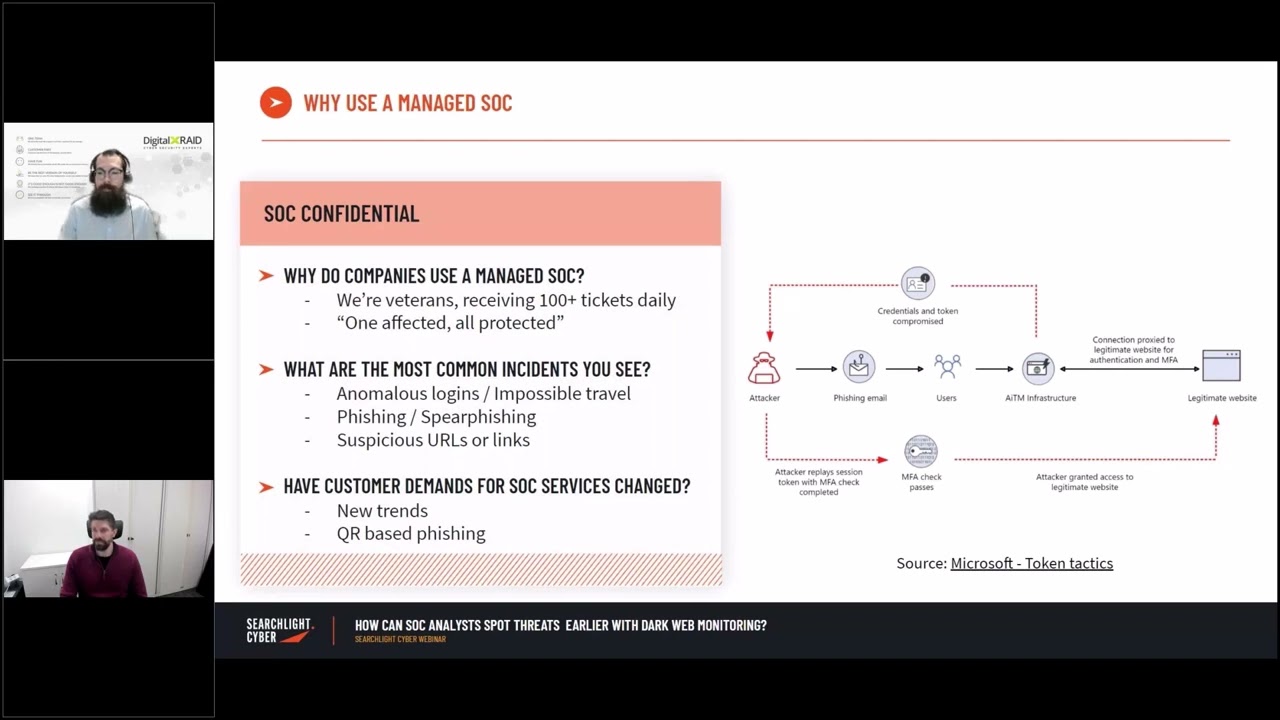
How effective is MFA against account takeovers?
Experienced product manager Dave Osler was on hand to ask questions throughout the webinar. In this section, he asked Tony whether he thinks multi-factor authentication (MFA) is an effective defense measure against data leaks. As we learn, unfortunately, MFA is not a silver bullet since it can be circumvented using techniques like QR phishing. Tony explains that if a threat actor can intercept the MFA details they can reuse the token until it expires; often, this is set to the system default of 30 days. DigitalXRAID says that they often see threat actors sitting in the user’s mailbox as part of their reconnaissance and sometimes try to gain information that can be used as part of a spear-phishing attack. This gave us two takeaways: firstly consider reducing your token session timeouts from their system default, and secondly, ensure you have tools in place to automatic dark web monitoring using our dark web monitoring tool for mentions that your organization may have been breached.
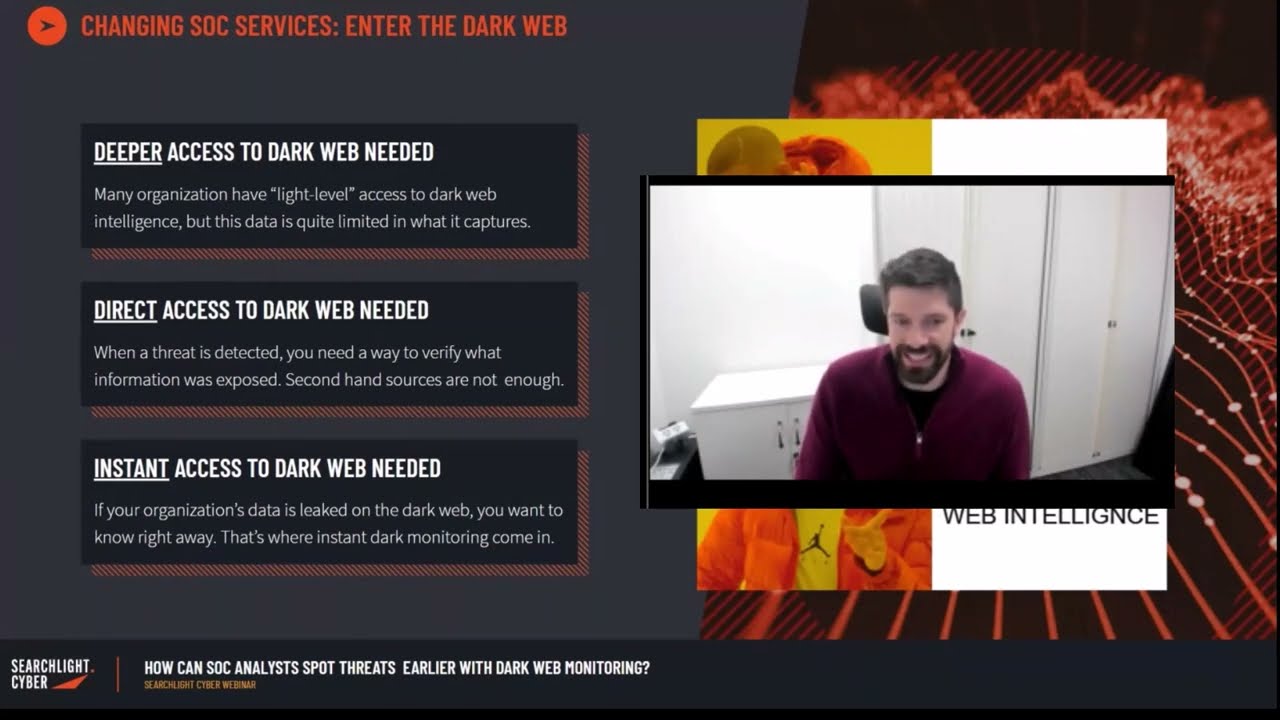
The challenge of collecting dark web data
There are two common approaches when it comes to collecting dark web data. The first is point-in-time investigations, where you create login credentials to access these sites to gather intelligence. While the cheapest option, it’s also the most time-consuming – and assumes you’re able to gain access and collect the information that you’re looking for before it has been deleted (as frequently occurs on activity like initial access broker posts). The second approach is automated collection – creating processes to programmatically gather and archive this data for use in alerts and investigations. While great in practice, as Dave explains, unlocking access to this goldmine of criminal activity is easier said than done. The biggest challenges include gaining and maintaining access to forums, being able to automatically bypass site CAPTCHAs, and scrape and structure data in a way that can be easily queried by security teams. After trying these two approaches, organizations often find it easier to bring in outside expertise, such as those offered by Searchlight Cyber’s automated dark web intelligence tools.
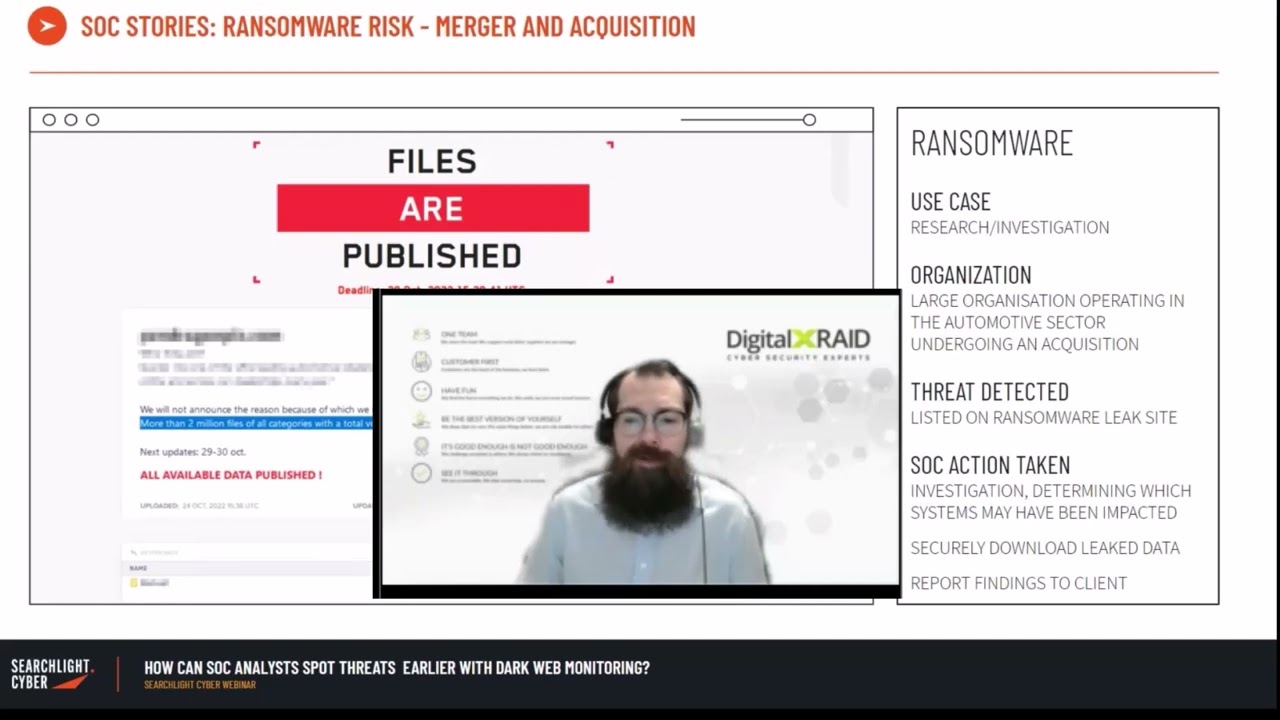
Customer story: Investigating Lockbit activity for an M&A transaction
In the first of two case studies, Tony demonstrated how dark web threat intelligence data can be used for due diligence processes for mergers and acquisitions (M&A). A large automotive organization approached DigitalXRAID when looking to acquire another company as they were aware that this company was a victim of a recent ransomware attack. As part of their due diligence, they were looking for assurances that the company they were acquiring was not exposing them to risk. Through the investigation, it was discovered that LockBit claimed to have over two million of the company’s files. However, through the use of our dark web investigation platform, Cerberus, it was revealed that all was not what it seemed. The final deliverable to the client was a full report giving assurances that the data gained was not critical and greatly exaggerated by LockBit. Ransomware groups behaving dishonestly and inflating numbers – who’d have thought it?
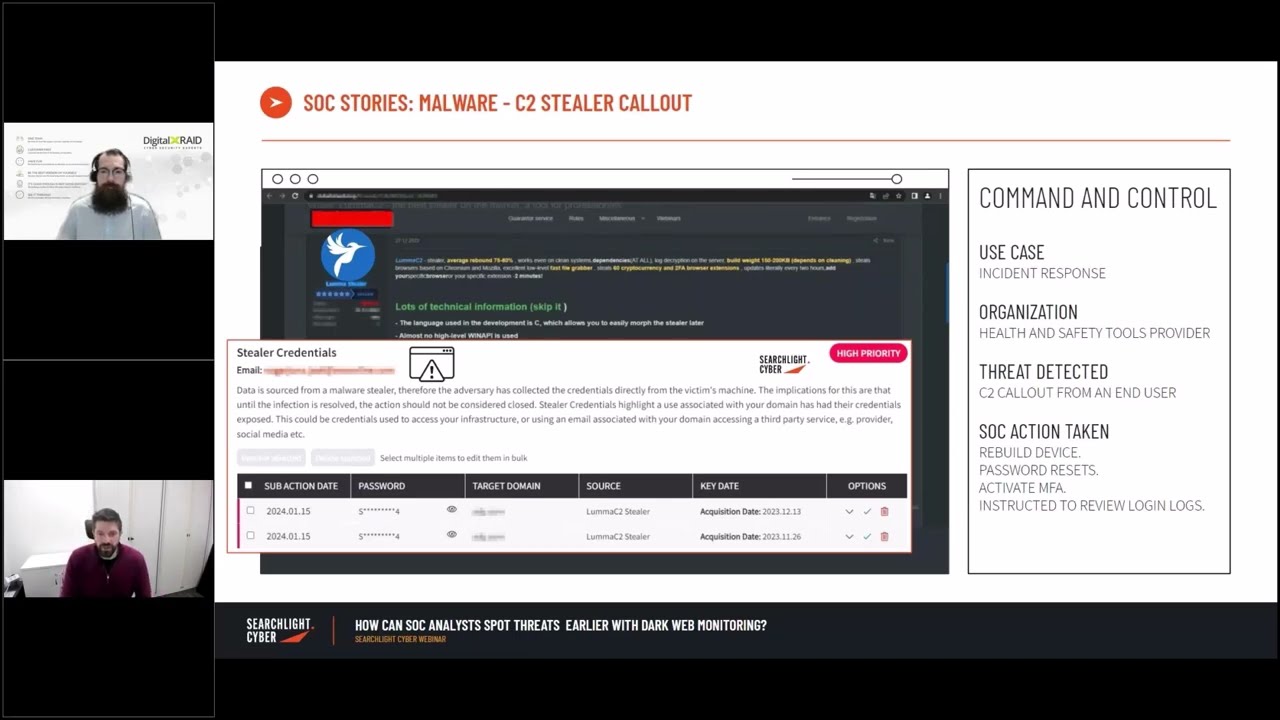
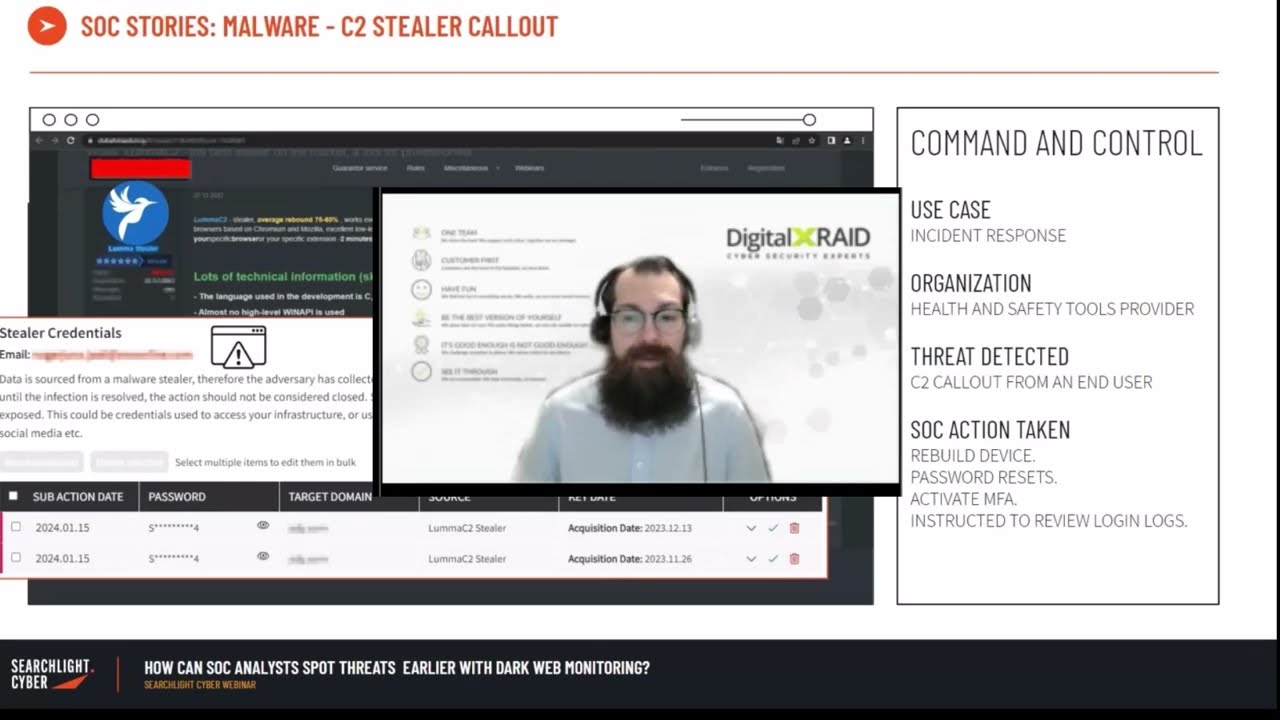
Customer story: SOC teams vs Malware – catching infostealer credentials in the wild
In this final case study, we learn how dark web traffic monitoring was able to identify a command and control callout from an end user’s device as part of the incident response engagement by DigitalXRAID, using Searchlight Cyber’s tools. The customer in this example was a health and safety tools provider who was using Github and wanted to understand whether any data had been exfiltrated in a recent breach and was being sold on the dark web. After creating a profile on DarkIQ, the DigitalXRaid team quickly identified high-risk stealer credentials, including a credible password granting access to sensitive payroll information. Prompt action was taken to mitigate the threat, preventing the exploitation of this information in potential subsequent attacks against the organization.