
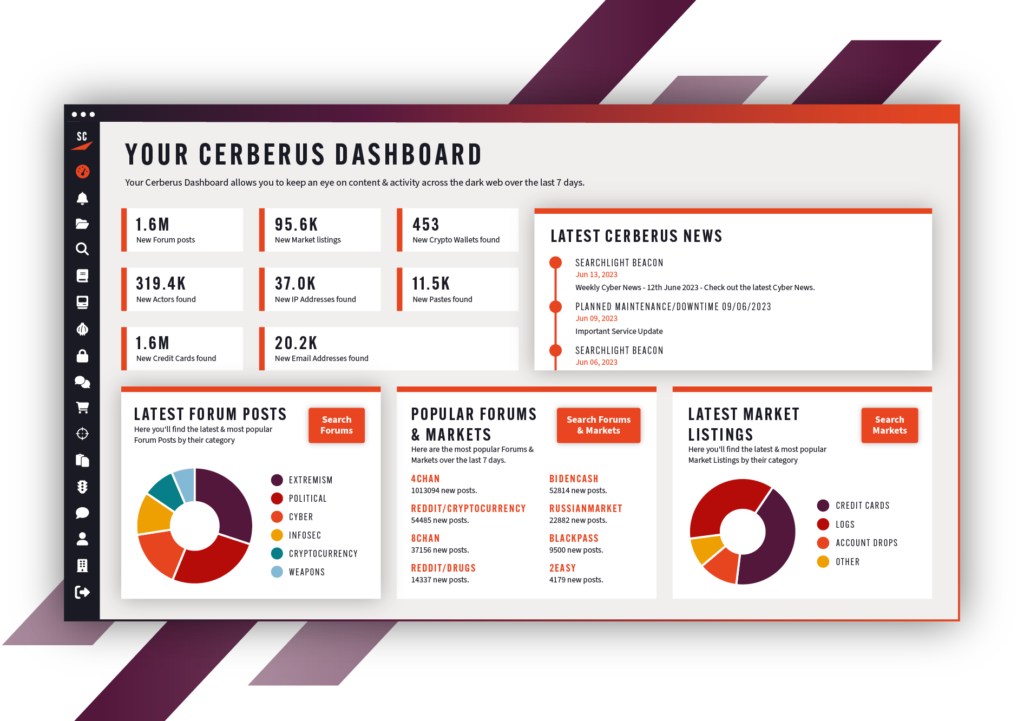
Cerberus uses proprietary techniques developed by world-leading researchers to deliver the most comprehensive dark web database on the market, providing access to intelligence that was previously unobtainable.
Trusted dark web database
The world's leading analysts and investigators use Cerberus to keep their people and countries safe online. It has been used in some of the biggest cases involving dark web activity and has had a proven impact in bringing perpetrators to justice.
Cerberus is designed to reduce labor for enterprise teams, law enforcement and government agencies. It does not require technical skills, background or knowledge to use and allows your people to investigate dark web data without putting themselves at risk or having to download any special software.
Our case management features enable you to maintain, audit, and report on multiple investigations across multiple teams. Automated alerting, reporting, and sharing of resources means that cases can be built in real-time and the ability to collaborate across departments within the platform means that you can easily deconflict targets.

Gather Threat Intelligence On Ransomware Groups
Ransomware continues to be one of the greatest concerns for governments and security professionals alike. The Cerberus Ransomware Search and Insights module helps investigators gain the advantage on ransomware groups with access to continuously updated intelligence on their latest tactics, known members, and victims.
More on Ransomware Search and Insights
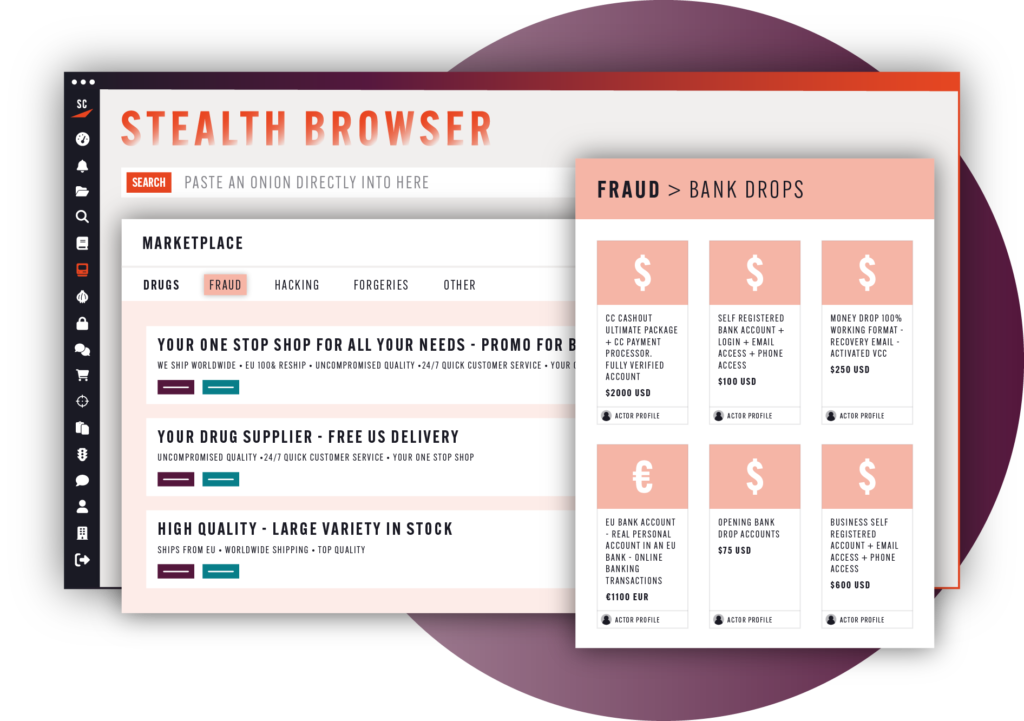
Your virtual machine to anonymously investigate the dark web
The dark web is a critical source of data and intelligence for cybersecurity professionals, but accessing it carries risks for the investigator and their organization. Stealth Browser eliminates these risks by automatically masking the investigator’s digital fingerprint, allowing investigators to quickly and securely access Tor and I2P onions on the dark web without risk to themselves or their organization’s infrastructure.
Learn more about the Stealth Browser
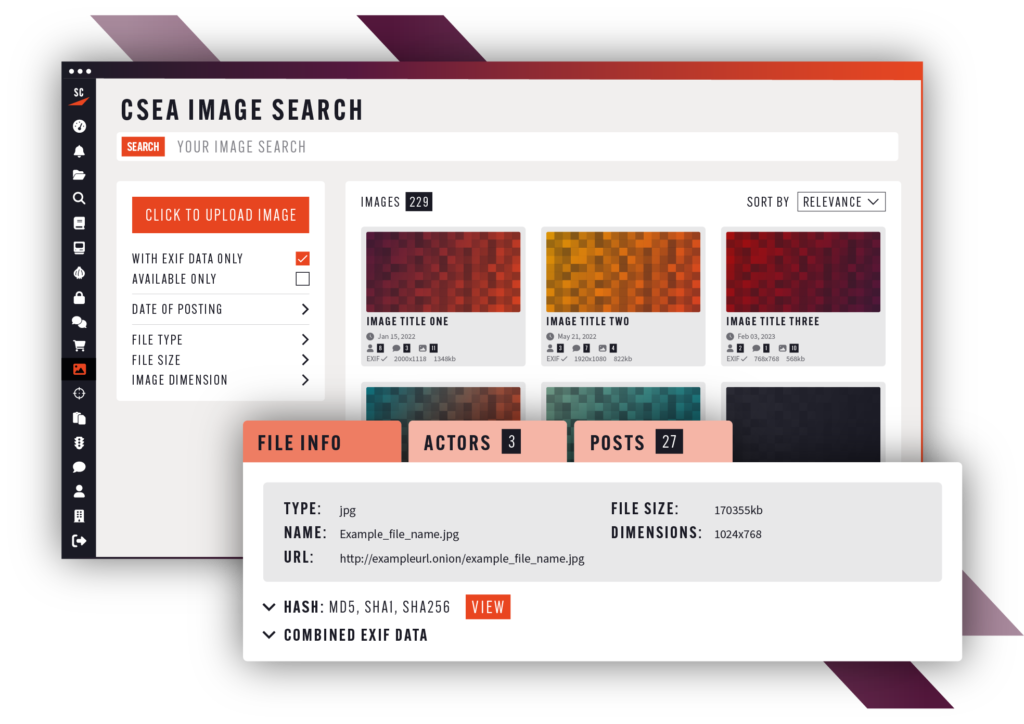
Identify victims of Child Sexual Exploitation. Prosecute offenders.
Provide your law enforcement officers with access to our intuitive CSEA image search. Regardless of their dark web experience, they can search by keyword, image metadata, or image upload to gather evidence on high-risk actors.

AI-powered language translation
Instantly translate data in the top 10 languages used on the dark web, including Russian, Chinese, and French. Searchlight translates full sentences as accurately as a human using Neural Machine Translation (NMT) and has been trained to understand Russian dark web slang – so you can decipher what criminals are really saying.
Dark web data sources
Cerberus creates a mirror image of the dark web so your teams can safely navigate the most comprehensive database of clear, deep, and dark web sources. Investigate live sites or search back through more than 15 years of historic dark web data.
Extracting data from the dark web is challenging and dangerous. There are many risks for organizations or enforcement teams who access the dark web without using Cerberus, including malware, trojans, and phishing attacks. Cerberus mitigates these risks by hiding your digital footprint, which means investigators can search dark web data, safe in the knowledge that their identity is protected and malware can’t jump to their organization’s live network.
Searchlight Cyber gathers data from different sources on the dark web, including underground forums, marketplaces, and encrypted chats, using automated and manual techniques. Our threat intelligence team has a wealth of experience in law enforcement, cybercrime, and the military. We utilize advanced tools such as cutting-edge web crawlers and natural language processing to extract context-rich information from dark web data.

Dark web dataset benefits
Understand the scale of criminal activity on the dark web to inform resourcing and investigation.
Gain visibility into the sale of credentials, vulnerabilities, malware, drugs, arms, child exploitation materials, and more on dark web marketplaces.
Investigate individuals and groups with the ability to pivot on usernames, aliases, and historic activity.

Uncover the activity of cybercriminals in the pre-attack phase, to inform cyber defenses.
Powerful reporting features within the platform allow you to meaningfully share findings with other teams or senior leadership.
Build case files of evidence gathered from your investigations into activity on the clear, deep, and dark web.

There are many ways data ends up on the dark web, often involving illicit activities, including:
We gather our data from different sources on the clear, deep, and dark web, including underground forums, marketplaces, and encrypted chats using a combination of automated technology and manual techniques in accordance with US, UK, and European law. As soon as Searchlight Cyber detects exposed credentials – like customer or staff usernames and emails – we’ll automatically cross-reference these details against more than 475 billion recaptured data points.
Commonly found data on the dark web includes compromised usernames, crypto wallets, IP addresses, passwords, email addresses, cookies, financial, medical, and personal information that could be used in a social engineering or phishing attack. Searchlight Cyber gives security teams easy access to billions of recaptured data points from marketplaces, forums, and leak sites across the deep and dark web.
Our dark web investigation platform, Cerberus, is designed to reduce the time it takes for cybercrime investigators, threat intelligence analysts, and law enforcement officers to investigate and manage cases using dark web data. There are no technical skills or dark web knowledge needed to use our tools to securely access the dark web, query data on dark web groups and threat actors, manage investigation cases, or collaborate across departments on the platform to deconflict targets.
Investigating criminals on the dark web poses challenges due to the anonymity and encryption tools in use. Searchlight Cyber’s dark web investigation and monitoring platforms, make it possible for investigators to identify and build cases on criminal dark web activities, safe in the knowledge that their identity is protected and malware can’t jump to their organization’s live network. Our dark web investigation platform has been used in some of the biggest cases involving dark web activity and has had a proven impact in bringing perpetrators to justice.