IN THIS EDITION OF BEACON SPOTLIGHT, THREAT INTELLIGENCE ANALYST, VLAD, TAKES A CLOSER LOOK AT THE CRIMINAL REACTION TO TELEGRAM’S PRIVACY CHANGES
Telegram is an instant messaging platform launched in 2013 used by 900 million users worldwide, appreciated by many (including those in the criminal underworld) for its lack of moderation and perceived focus on privacy. Besides instant messaging, the platform offers several features, including the ability to create bots to perform various tasks, such as easily manage an in-app shop or marketplace or automatically deliver files or text obtained from other sources. While these features are useful when used in legitimate ways, they are also welcomed by threat actors, scammers, data thieves, malware operators and more.
We invite you to read more about attack vectors commonly seen on Telegram in our previous series of blogs.
In this blog we’re going to take a closer look at the fall-out of two major developments for Telegram in recent months: the arrest of its CEO in France in August and the subsequent update of its privacy policy, where it stated that it would comply with law enforcement requests for user’s IP addresses and phone numbers. How did the criminal underworld react?
Criminals React to the Arrest of Telegram’s CEO
The recent arrest by French police of Telegram’s CEO, Pavel Durov, was met with uncertainty about the platform’s future. Criminals using Telegram started speculating about the outcome and the possible interference of law enforcement with the application. Some groups went as far as making threats and expressing their support for the arrested individual (Figure 1) while others started attacking (Figure 2) France-based entities, sometimes even governmental agencies in a distributed denial-of-service (DDoS) campaign. The campaign launched by the hacktivist group known as RipperSec took place between September 2nd and September 9th, 2024.
Figure 1: Dxploit and Khilafah Hackers threatening France in the wake of the arrest of Telegram’s CEO, Pavel Durov.
Figure 2. The RipperSec hacktivist group announces one of its DDoS attacks on a French government agency on its Telegram channel.
Criminals Look for Alternatives After Telegram Changes its Privacy Policy
After Durov’s release on bail after being charged with multiple crimes, an updated privacy policy was released for Telegram. Some key changes included the possibility of sharing phone numbers and IPs with law enforcement when requested. Another change implied that the search function was altered in order to make “problematic” content more difficult to find. These changes understandably upset cybercriminals, with some already looking for alternatives.
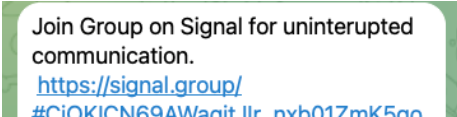
The administrator of a Telegram channel dubbed JB Services, which was known for selling bank account “drops” in Canada (bank accounts created with fake or stolen identities) was observed inviting customers to join their Signal group chat.
Figure 3. The administrator of the Telegram channel JB Services encourages followers to join its Signal group chat.
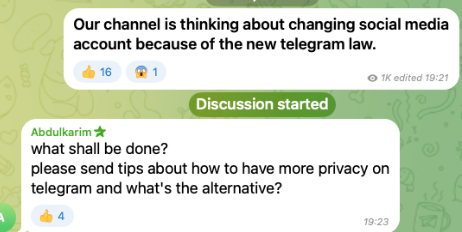
The pro-Palestine hacktivist group Anonymous Collective, which has more than 9,000 followers on its Telegram channel, was also looking for suggestions to change platforms (Figure 4).
Figure 4. Anonymous Collective asks its Telegram followers for recommendations of new social media platforms following the “new Telegram law”.
Another hacktivist group known as AnonymousActivist, part of the Holy League alliance, also claimed to abandon Telegram and move to Signal (Figure 5).
Figure 5. AnonymousActivist claims to be leaving Telegram, in favor of Signal.
Discussions on the topic also appeared on cybercrime forums such as Exploit and Breach Forums (Figure 6). The general consensus appears to be that, in case a change of platform becomes unavoidable, Signal would be a good choice. Some actors even suggested a return to Jabber (also known as XMPP). This used to be the default choice of secure communication in the underground world, especially when using the Off-the-Record Messaging (OTR) extension, which allows encrypted messages. Nowadays, an even more secure extension known as OMEMO is available. Other suggestions included Tox, Session, Matrix, Keybase, Element.
Figure 6: Individuals on Exploit and BreachForums discuss their preferences of alternatives to Telegram.
However, while the suggested apps can be used for their instant messaging functionality, they fail to replace some of Telegram’s key features. Telegram allows users to create bots to serve specific tasks, create channels, and most importantly, has a much larger user base that could be easily attracted to cybercriminal activities.
It should be noted that these are just the initial reactions that we have observed following the news related to Durov and Telegram’s policy changes. We are yet to see any significant activity definitely showing a trend that criminals are moving away from Telegram. Some actors are clearly taking pre-emptive steps but it’s unclear how they will proceed when the initial hysteria calms down. There is also a possibility that a hybrid approach will take place, where only particularly sensitive discussions will be moved out of Telegram, while the platform could still be used for operating news channels, advertising, and reaching wider audiences.
Similarly, we could see an increase in cybercriminals using Telegram adopting additional OpSec measures, such as using virtual private networks (VPNs), proxies, or other similar services to mask their IPs and buying burner SIM cards to register fresh accounts. This is a situation we will monitor closely.