In this blog we discuss External Attack Surface Management and how – used in conjunction with dark web monitoring – businesses can identify points of exposure.
What is External Attack Surface Management?
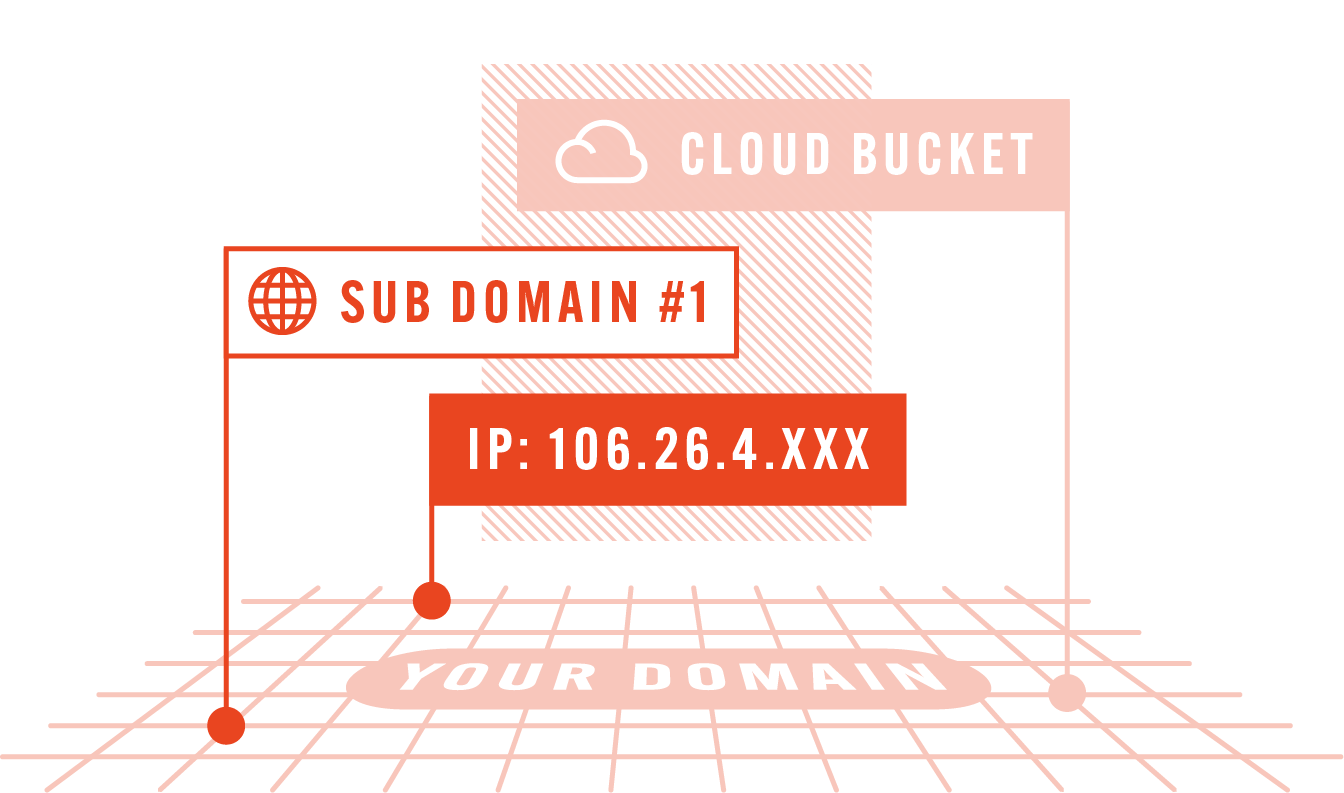
Do you have a holistic view of all the internet connected assets in your organization or are there potential entry points for cybercriminals that you don’t know about?
See your publicly accessible digital assets – so you can see what ports, repositories, and shadow IT are exposed before they can be exploited.
Keeping track of all the software, cloud services, and public-facing systems employees are using is a challenge for all businesses.
This is where External Attack Surface Management (EASM) and dark web monitoring tools can help.
EASM is a proactive security practice focused on identifying, assessing, and managing potential vulnerabilities within an organization’s public-facing digital footprint. The digital attack surface refers to all IT assets that are exposed to the internet, including cloud services, servers, and other publicly accessible systems.
EASM provides organizations with a comprehensive view and inventory of these assets, including those cybersecurity teams weren’t aware of (aka shadow IT), helping them to understand the risks and potential attack vectors that could be exploited by malicious cybercriminals.
The primary goal of EASM is to identify corporate IT assets and pinpoint any vulnerabilities , such as misconfigurations or outdated software. By having a real-time view of an organization’s external digital footprint, EASM ensures that security teams can detect and remediate weaknesses before they are exploited.
Ultimately, EASM is a critical component of a broader cybersecurity strategy, providing a proactive approach to managing external threats, reducing vulnerabilities, and maintaining a secure, resilient digital environment. But we can actually take EASM one step further by integrating the practice with dark web monitoring and investigations.
How EASM and dark web monitoring work together
EASM on its own can assess the exposure and risk to your organization, so how can dark web monitoring complement this strategy?
EASM and dark web monitoring can work together to provide a more comprehensive view of potential threats to a business. While EASM focuses on identifying vulnerabilities and exposures within an organization’s public-facing digital assets, dark web monitoring helps to detect if any sensitive data, credentials, or sensitive information has been compromised and shared on the dark web in forums, marketplace or by Initial Access Brokers.
By integrating EASM tools and dark web monitoring, businesses can get a complete view of their threat landscape, ultimately expanding their defensive radar and gaining visibility of threats earlier. EASM helps organizations to continuously assess and secure their external attack surface, while dark web monitoring provides early warning signs of attacks and breaches. Together, these tools can provide a comprehensive and proactive approach to cybersecurity, leading to:
- Faster detection.
- Stronger defense.
- More informed incident response.
Examples of EASM and dark web monitoring collaboration
Here are just some examples of how EASM and dark web monitoring can collaborate and enhance threat detection and mitigation:
Detecting credential leaks and weak passwords
EASM can identify weak access controls and other security gaps that leave an organization’s credentials exposed to attacks. Coupled with dark web monitoring, cybersecurity teams can track employee credentials that have been compromised, either from data breaches, or from malware infected machines. This enables organizations to take proactive action to reset passwords, remediate the source of infection and even monitor for compromised customer accounts.
Early warning of targeted threats
EASM tools give cybersecurity teams visibility into which public-facing assets are vulnerable and could easily lead to an attack, helping to reduce attack surfaces. Additionally, dark web monitoring can identify if a business or any specific assets are being discussed as potential targets by threat actors. Dark web forums may reveal early signs of an intent to attack vulnerabilities, giving cybersecurity teams an opportunity to take preventative actions based on intelligence from both sources.
Mitigating or lowering the impact of a data breach
If EASM identifies a vulnerability such as unpatched software or misconfigured security settings that could lead to a data breach, the organization can respond quickly to resolve the issue. On top of that, in the eventuality there is a data breach, dark web monitoring can track if any data has been leaked on the dark web, allowing you to assess what the impact of that data being shared publicly is. By assessing data from both tools, cybersecurity teams can take steps to limit further leaks and additional cyberattacks.
Monitoring insider threats
While EASM focuses on external attack surface vulnerabilities and exposures, dark web monitoring can also identify additional insider threats, such as exposing company information from public GitHub repositories, poorly configured marketing mini-sites, or even employees unknowingly interacting with phishing emails. Much like our previous points, dark web traffic monitoring in particular can then help to identify whether any of the vulnerabilities employees have opened themselves up to have led to data breaches on the dark web.
Improving Threat Intelligence and Incident Response
EASM alerts cybersecurity teams to unknown potential vulnerabilities and exposures in real time, but dark web monitoring can supplement EASM by providing actionable intelligence on whether a breach has already occurred or is in progress. This intelligence can include ransomware group monitoring, forum chatter, and TOR traffic to and from your network. This allows organizations to respond to incidents with insights of the cybercriminals tactics and intentions. Incident response teams will be able to go back and see structured historic data to understand what has led to this specific attack. How did the attack start? Are there any Initial Access Broker posts? Or have there been any conversations on forums about your organization?
Knowing this information gives cybersecurity professionals the ability to patch any vulnerabilities before another attack escalates.
Searchlight Cyber’s approach to EASM
EASM is an important tool in the cybersecurity armory but – used alone – it doesn’t always paint the full picture of the cybersecurity threats to your organization. This is why Searchlight Cyber has always offered EASM in its dark web monitoring platform.
Taking under 10 minutes to set up and discover known and unknown threats, our dark web monitoring solution DarkIQ automatically monitors for external threats to your infrastructure, encompassing the public-facing digital assets your organization has.
DarkIQ’s EASM capabilities can:
- Automatically identify public-facing assets that could be entry points for attackers by inputting a single domain.
- Create an inventory list of active and discovered attributes that are clearly categorized for easy management.
- Create dashboards to communicate high level risk and guide effort as a security team.
- Produce exposure and risk management alerts, with clearly prioritized actionable intelligence.
- Embed the Mitre ATT&CK Framework to add context to alerts and suggest solutions for future hardening.
- Create reports to show the current state of play with analysts comments, recommendations or summaries of any mitigation steps taken.
Dark web monitoring and EASM further enhances current cybersecurity strategies by alerting organizations when their assets or infrastructure are being actively targeted on the dark web. This closed-loop between internal exposure and external threat intelligence ensures that both known and emerging threats are proactively addressed.