If you missed our “Dark web intelligence for MSSPs – From SOC to Incident Response” webinar, this blog takes you through the key takeaways.
Why MSSPs leverage dark web intelligence
A recent report from IBM noted that the global average cost of a data breach in 2024 is $4.88m, an increase of 10 percent over the last year, and the highest total ever. With that in mind, it’s no surprise that two-thirds of MSSPs say customers have asked for dark web threat intelligence.
In this webinar our two experts discuss how dark web intelligence can help MSSPs unlock commercial opportunities and differentiate themselves against competitors.
Let’s dive into the three key takeaways from this recent MSSP focused webinar.
Dark web intelligence that delivers actionable insights to support SOCs
The dark web has a vast and astonishing amount of data that is varied, and constantly evolving. Navigating the data on the dark web to extract meaningful insights is a challenging task. Unlike the clear web where search engine’s index and organize content, the dark web is intentionally unstructured, making it difficult to analyze.
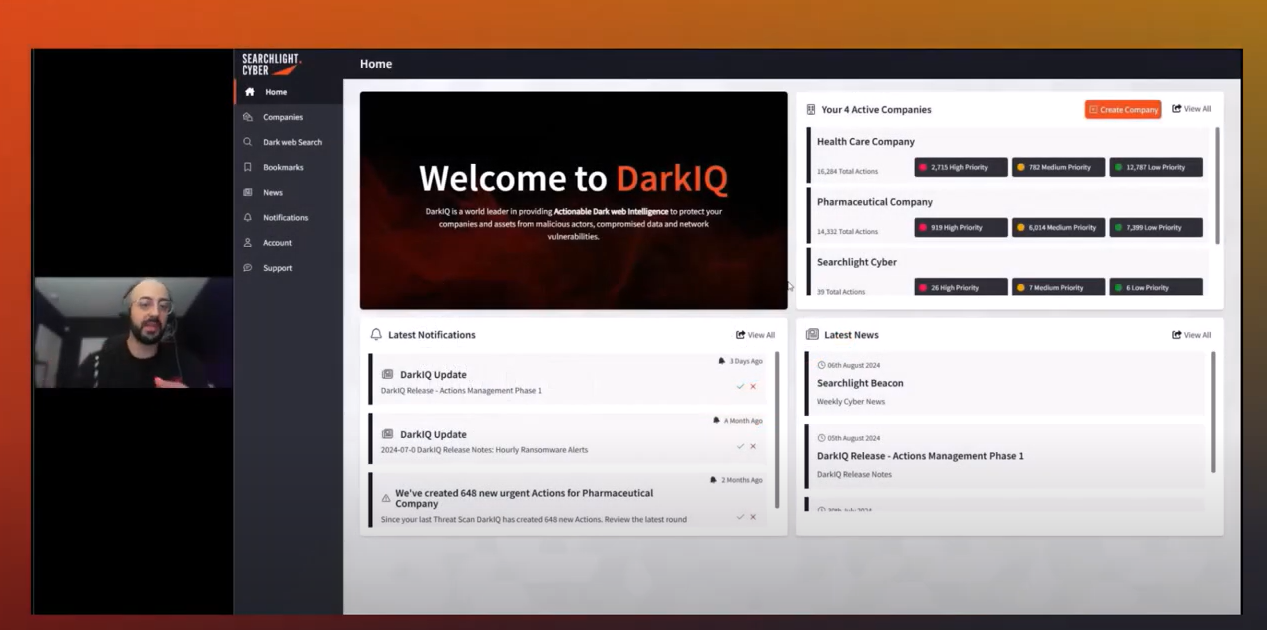
However, dark web monitoring tools structure and index dark web data with a view to present SOC analyst’s with actionable insights, limiting the amount of time spent triaging cybersecurity alerts for not only themselves, but also clients. This actionable data helps to establish a proactive team that can help resolve and prevent client cybersecurity issues in a timely fashion, adding value to more traditional cybersecurity methods.
Steven Bar, Senior Threat Intelligence Engineer demonstrates the insights SOC analysts can see and action using DarkIQ:
Dark web intelligence adds value to incident response
Once an attack has happened and a clients’ infrastructure has been compromised, it’s important to understand how the infiltration started and how MSSPs can prevent them being victims again.
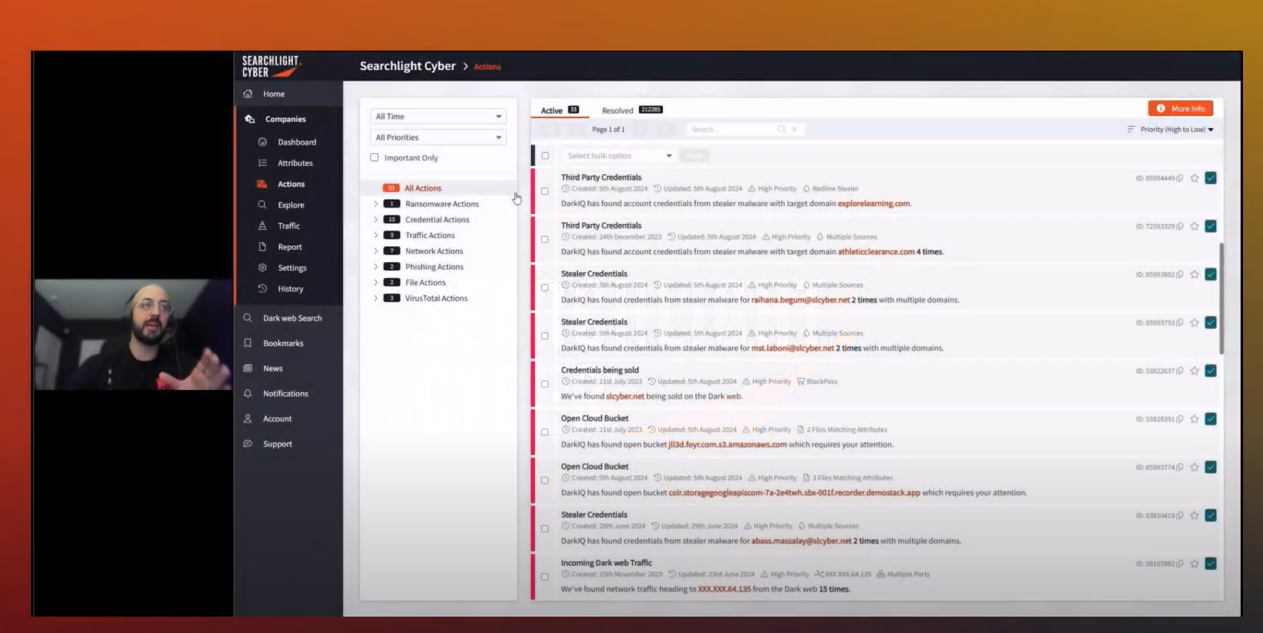
We’ve already mentioned the vast amounts of data there is on the dark web, but with attacks potentially going back 12 months, structured historic data allows incident response teams to go back in time and see what has led to this specific attack. Dark web investigation platforms that store historic dark web sites, marketplace and ransomware leak site posts, and chat that happens on forums, give incident response teams the chance to easily look back and retrace the steps of the cybercriminal. How did the attack start?, are there any Initial Access Broker posts selling access to your clients organization?, have there been any conversations on forums about your clients brand? Knowing this information gives cybersecurity professionals the ability to patch any vulnerabilities before another attack escalates.
In this next clip, Steven delivers an overview of how incident response teams can go back in time and review the steps taken by cybercriminals before the cyberattack took place:
Using dark web intelligence for one off client investigations
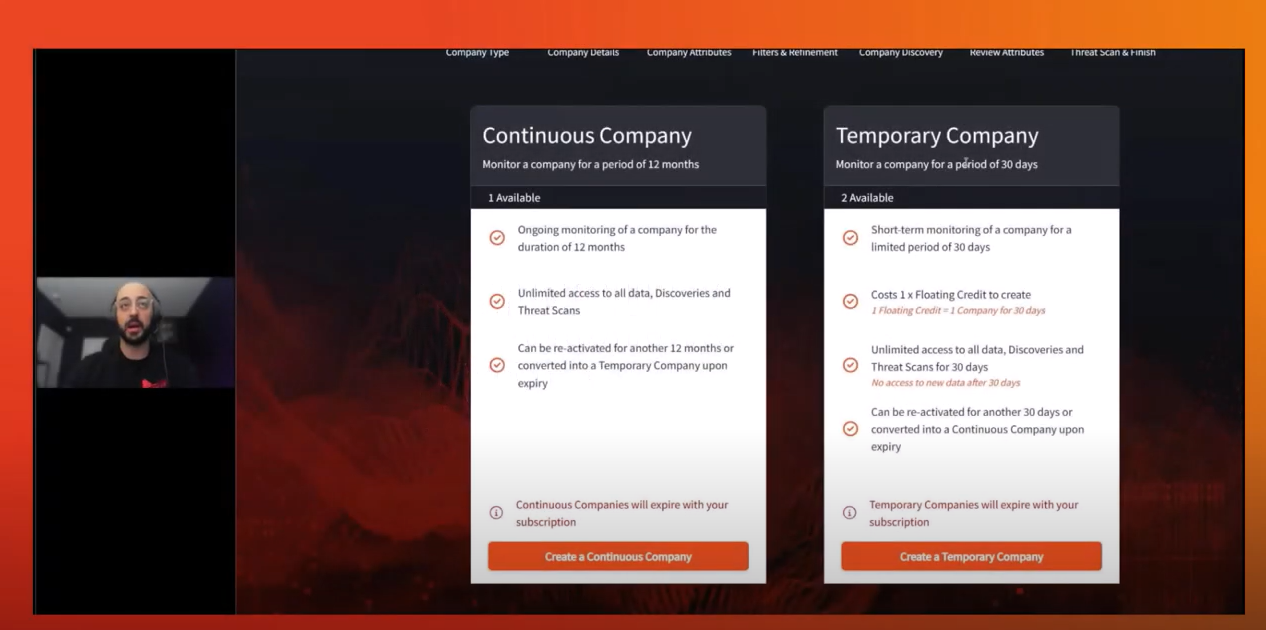
While dark web investigation and intelligence is often used to enhance the current infrastructure of your clients, there will be clients that you are working with for a one-off project, or a short period of time. These projects can be penetration testing, incident response, cybersecurity audits, or assisting with mergers and acquisitions.
Dark web monitoring tools play a crucial role in assessing a company’s cybersecurity risk, especially in the instance of mergers and acquisitions. By identifying such indications early, organizations can evaluate the security posture of their acquisition and take proactive steps to mitigate risks before the buying company ingests them into their network.
In this final clip, Steven demonstrates how threat hunters can use dark web insights when it comes to assessing the cybersecurity risk of the merging organization:
Enhance your security services with dark web intelligence
Become your clients trusted advisor on the dark web, demonstrate added value, and grow your revenue by unlocking new opportunities with dark web monitoring and investigation tools. Give your analyst team secure access to cutting-edge technology and data, reducing the time it takes them to research and respond to emerging threats.