In this blog, we explain what dark web monitoring means, the benefits it adds on top of your existing cybersecurity infrastructure, and the best way to execute it.
Going beyond traditional cybersecurity monitoring
If you already know what the dark web is (watch our quick explainer video if you aren’t up to speed) but you aren’t sure why you should be monitoring it as part of your wider cyber threat model, this blog is for you!
Organizations around the world continue to invest in their defenses, proven by the cybersecurity market value standing at an estimated $172.32 billion in 2023. There is an ever increasing number of capabilities and methodologies on offer for security teams to deploy but the focus has remained around the identification of malicious activity within the network.
Dark web monitoring represents a different approach – adding an additional view of activity that is happening outside of your network – before it reaches the delivery stage and escalates. It involves continuously tracking and scanning dark web forums, marketplaces, and other dark web sites where illegal activities occur, to identify threats.
These threats could range from the leak of sensitive information related to your business (including staff or customer data, credentials, intellectual property, all the way to personal information about the CEO), to indications that a cybercriminal is targeting your organization, or has identified a vulnerability in your tech stack. Dark web monitoring enables cybersecurity teams to detect these threats earlier, mitigate the risks faster, and enhance their overall security posture.
Where does a cyberattack begin?
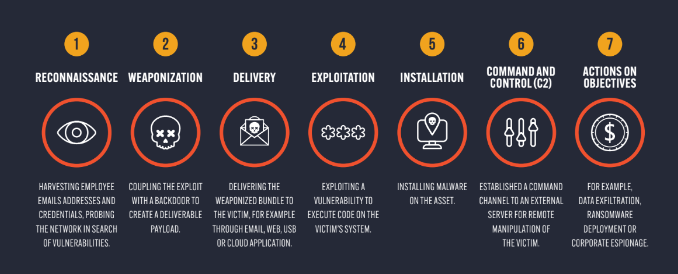
Dark web monitoring addresses a fundamental truth when it comes to cybersecurity threats: that a cyberattack doesn’t start on the network. In fact, it starts weeks, months or even years before, when threat actors do their due diligence on their target, plan their attack, coordinate their efforts, and purchase the tools, credentials or access they need to execute their operations. Often, this reconnaissance activity takes place on the dark web.
Of course, understanding how threat actors maneuver their way through an organization’s infrastructure is valuable for informing network security and incident readiness, but it does little to help security teams prevent their network being breached in the first place. Organizations need dark web monitoring to glean intelligence on cybercriminal pre-attack activity that takes place on the dark web, in order to take action to stop a breach.
Dark web monitoring and intelligence gives organizations the capability to view that activity and strike back against threat actors at the earliest stage in the Cyber Kill Chain (see graph) – before a network is breached – enabling them to take a much more proactive approach to cybersecurity. It allows cybersecurity teams to monitor for the earliest warning signs of an attack, helping to prevent security incidents against organizations.
The benefits of monitoring the dark web
By providing visibility into threats earlier in the Cyber Kill Chain, dark web monitoring provides the following benefits:
- Ability to take proactive measures to prevent or mitigate potential cyberattacks before they are “launched”.
- Informing business risk by delivering insights into specific threats and vulnerabilities and their potential impact.
- Making informed cybersecurity decisions and empowering senior leaders and decision-makers with accurate and timely threat information.
- Intelligence that allows organizations to develop more effective incident response plans.
- Profile of high-risk actors, such as ransomware groups, hacktivists, or nation-state actors, helping to better understand their motivations and tactics.
- Ability to tailor defense strategies and build security measures that are more resilient to likely threats.
- Meet compliance and regulations that require organizations to gather threat intelligence and take reasonable measures to prevent an attack.
The challenges of dark web monitoring
Now we have established the many benefits of dark web monitoring, how can cyber threat intelligence teams best execute it?
Before working with a dark web monitoring vendor, many organizations will often have tried different levels of monitoring themselves, but this can often be too time consuming and resource heavy to make it cost-effective or materially reduce the risk of a cyberattack. Many organizations would need to consider multiple monitoring multiple channels such as supply chain threat monitoring.
Point-in-time dark web investigations
The first tactic many organizations try is to manually access dark web sites to find information related to them and their business. While this is undoubtedly the cheapest option, there are a number of challenges and flaws to this approach to dark web monitoring in the long run:
- Finding dark web sites – this approach relies on analysts firstly being able to identify all of the sites that could be relevant to their business, which could be into the hundreds. Bearing in mind that dark web sites aren’t indexed and that their addresses are a random combination of letters and numbers, just finding the sites can be a time consuming and arduous task.
- Accessing dark web sites – once the analysts have found the sites, they then have to access them. Often this includes creating login credentials for the sites and sometimes there are additional hurdles that hacking forums and marketplaces use to try and stop security and law enforcement professionals from accessing them. For example, some forums may ask for a down payment of cryptocurrency or even require a referral from another member.
- Consistently monitoring – dark web sites are continuously being updated and contributed to, which makes continuous monitoring a challenge for human analysts.
- Finding historic data – posts can also be deleted or altered, which means that if the analyst isn’t monitoring the site at the exact time a threat reveals itself, it could be missed.
Automated dark web monitoring
Next, many organizations try to create processes to programmatically gather and archive dark web data. While this is the right idea in theory, in practice automating data collection from the dark web also has challenges. Most notably, in maintaining access. Dark web marketplaces and forums are aware that this is an approach security teams will try to take and they build in mechanisms to try to prevent automated crawling and data scraping from their sites. For example, many use customer-made, complex CAPTCHAs to prevent non-human access to the sites.
How should I monitor the dark web?
If you have tried point-in-time or automated collection, and neither of those methods have worked for your organization, how should you be monitoring the dark web?
It’s actually quite a simple answer. The right way to go about dark web monitoring is partnering with a company whose entire focus is on monitoring the dark web.
Although on the surface you might think this is going to cost a lot of money, the right dark web monitoring partner will give you the accurate data and information you need in the long run.
Dark web monitoring vendors you should partner with, will have:
- Been established for a number of years.
- Comprehensive coverage of dark web sites.
- Historic dark web data.
- A deep understanding of the dark web.
- Automation in place for categorizing dark web data.
Having a dark web monitoring vendor that has a wealth of experience will allow your cybersecurity team and analysts to collect and interrogate the data more efficiently.
What questions should I ask a dark web monitoring vendor?
Once you establish that you have a requirement for a dark web monitoring vendor, you can then focus on evaluating potential partners by asking the right questions.
- Can the vendor fulfill your intelligence gaps?
- How regularly does the vendor collect data?
- Does the vendor have sufficient coverage of your focus areas?
- How quickly is data made available?
- Is the vendor compliant with your organization’s legal requirements
- Does the vendor offer access to unstructured or structured data?
- How intuitive is the tool and user experience?
- Does the vendor’s platform allow users to collaborate?
- What format is the intelligence provided in?
- How open is the vendor to accepting data source requests?
To get insights and guidance on selecting a new Cyber Threat Intelligence (CTI) partner, download our report, “The Essential Buyer’s Guide to CTI.”
Where does dark web intelligence fit with my cybersecurity posture?
While dark web monitoring offers multiple benefits, it’s crucial to remember that it’s part of an advanced enterprise cybersecurity posture and doesn’t replace your current cybersecurity strategy or infrastructure. Using dark web traffic monitoring as part of our cybersecurity plan can take any business from being cyber reactive to cyber progressive. Doing this gives cybersecurity teams the invaluable insight they need to change and update their infrastructure as they see potential threats appearing.
Organizations are continuing to be compromised in spite of investing in security solutions to protect their networks. In order to break this cycle, security teams need to view their existing capabilities as a solid foundation of security infrastructure, but also seek to augment them with intelligence that alerts to the possibility of attack earlier in the Cyber Kill Chain.
Dark web threat intelligence should be considered as an integral component to enhancing an organizations’ security posture. Employing a dark web monitoring capability can help to move an organization from a reactive posture and into a proactive security posture, identifying potential threats before cybercriminals can compromise the network.