The MITRE ATT&CK framework, which has long been a popular tool for security professionals, is also useful for explaining the value of dark web intelligence.
What is the mitre att&ck framework
Open to all organizations and freely accessible, The MITRE ATT&CK framework has long been a popular tool for security professionals across all industries to map their defenses against the Tactics, Techniques and Procedures (TTPs) cybercriminals use to infiltrate their network and execute attacks.
The framework is also useful for explaining how dark web intelligence can shine a light on attackers right at the beginning of their operation, informing organizations’ defenses so they can stop their adversaries right at the beginning of the “kill chain”.
the mitre ATT&CK Enterprise matrix
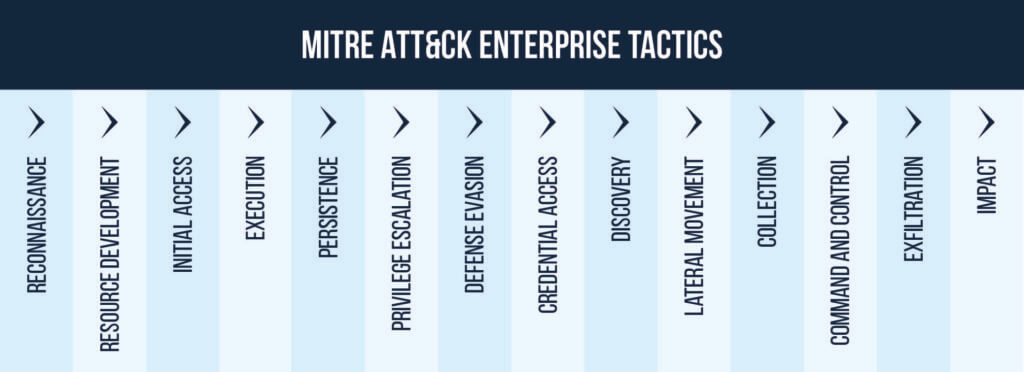
The MITRE ATT&CK Enterprise Matrix represents the chain of tactics that threat actors can use to execute an attack on an organization’s network. Each tactic is broken down into further detail on the techniques attackers might use at each stage, with recommendations for how organizations could defend themselves against each one:
The first two tactics, Reconnaissance (TA0043) and Resource Development (TA0042) are where dark web intelligence has a role to play. As a short overview of each:
- Reconnaissance – consists of techniques that involve adversaries actively or passively gathering information that can be used to support targeting, which may include details of the victim organization, infrastructure, or staff/personnel.
- Resource Development – an adversary establishes the resources they can use to support operations, including techniques that involve adversaries creating, purchasing, or compromising/stealing resources that can be used to support targeting.
These tactics are unique because they are the only ones in the framework that focus on the period of time before the network is breached. This is significant because it means that these are the only points where organizations have a chance to stop the breach from happening.
The integration of the pre-att&ck framework
Interestingly, the Reconnaissance and Resource Development tactics are two relatively recent additions to the Enterprise Matrix, having previously sat in a separate PRE-ATT&CK framework (which is still viewable as the PRE Matrix) while the Enterprise Matrix focused exclusively on “the behaviors that adversaries perform after they’ve broken into an environment”.
In October 2020, MITRE ATT&CK made the decision to integrate them into the Enterprise Matrix acknowledging that their omission had previously “left pre-compromise adversary behaviors uncovered” in the main framework and based on feedback from a “number of organizations over the years that Enterprise ATT&CK’s coverage of only post-compromise behaviors held up their ability to adopt it”.
This change from MITRE ATT&CK reflects a broader industry demand for pre-attack intelligence on adversaries, so that organizations are not limiting their defense only to mitigation methods once a threat actor is already inside the perimeter but are also taking proactive actions to pre-empt attacks.
Mapping dark web intelligence to the mitre ATT&ck framework
As MITRE ATT&CK states, mitigating attacks at this pre-attack stage can be challenging as the tactics “take place in a space outside of an enterprise’s defenses and control”.
However, dark web intelligence gives security teams an opportunity to extend their view out beyond their organization’s environment and into the Reconnaissance and Resource Development stages. This is because the activity of threat actors at this point in time largely takes place on deep and dark web forums, marketplaces and groups – where they believe they can act with impunity, out of reach of cybersecurity teams and law enforcement.
Armed with intelligence on this activity, security teams can modify and enhance their defenses based on greater clarity of exactly who is planning to attack the organization, and how they plan to do it.
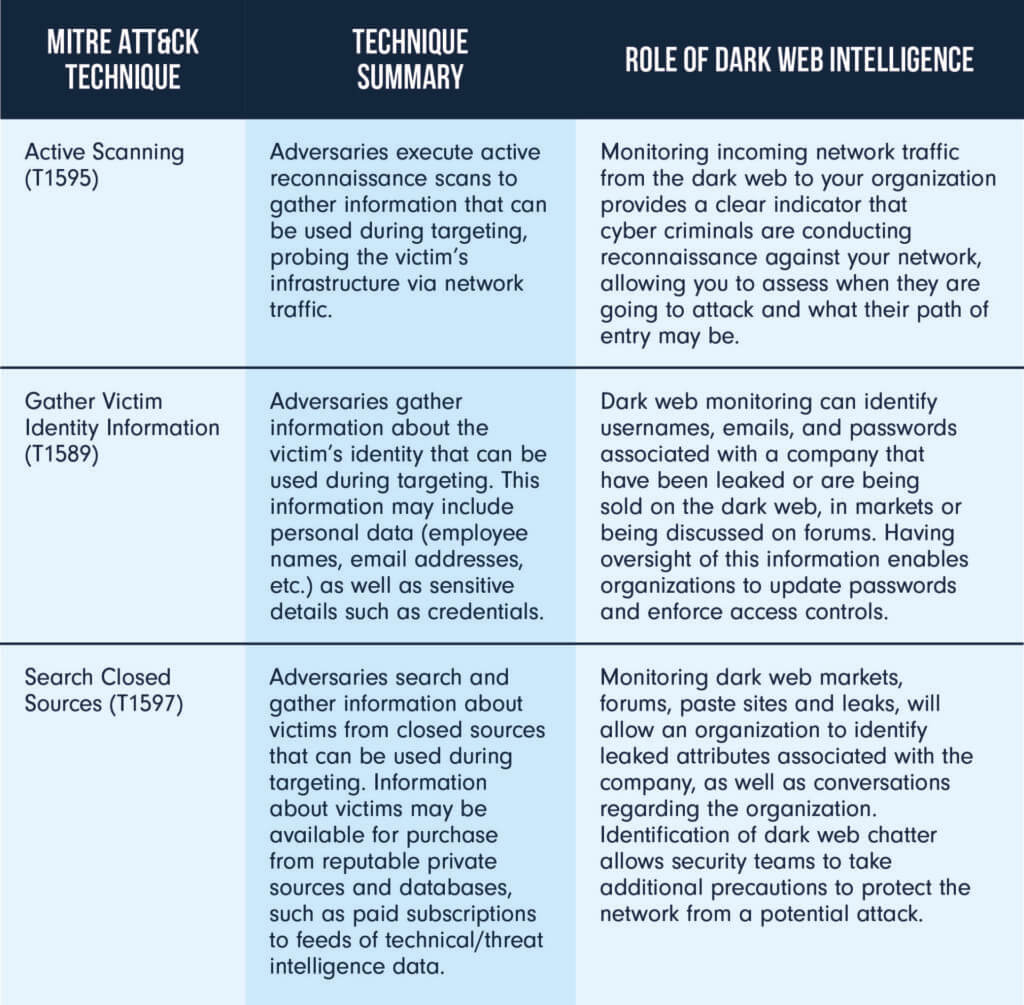
In many cases, dark web intelligence can be directly mapped onto the PRE Matrix techniques of the MITRE ATT&CK framework. These are just three examples:
Using the dark web for pre-attack intelligence
The introduction of PRE-ATT&CK into the main framework acknowledges the reality of cybercrime – that attacks don’t start on the network. In fact, they start weeks, months or even years before as threat actors do their due diligence on their target, plan their path of attack, coordinate their efforts, and purchase the tools, credentials or access they need to execute their operations.
Dark web intelligence allows security teams to undermine the Reconnaissance and Resource Development of cybercriminals. By arming themselves with the adversarial knowledge they need to pre-empt and prevent attacks, they can reduce the chance of breaches and – in turn – the cost of cybercrime to their business.