
With the release of the new Stealth Browser, Dave Osler, Head of Product at Searchlight Cyber looks at what this means for analysts and investigators as they carry out research on the Dark web.
Who keeps investigators safe on the dark web?
Here at Searchlight Cyber, our mission is to protect society from the threats of the dark web. Pretty simple, huh? Well, what about protecting people as they protect others from the threats of the dark web? This is becoming a little like the film Inception, but bear with me while I take you through some of the work we’re doing and how that helps protect our customers and speeds up their investigations. I’ll start with a brief background on the deep and dark web, just in case you’re new to this.
A brief background to the deep and dark web
As deep and dark web ecosystems have grown, underpinned by the panacea-like promise of anonymity, they’ve attracted criminality spanning Initial Access Brokers, to ransomware groups, to sellers of drugs, firearms, and other illicit items. The popularity of these services has increased over time, which subsequently has led to increased attention from both law enforcement and cybersecurity teams, in an attempt to understand the threats and to get a step ahead of the curve.
Gaining access to intelligence on the dark web gives an incredible insight into the types, quantities, geographic regions, and industries that are being targeted, whether that is through the sale of “VPN credentials to a large oil and gas company in the midwest” for example, or to the sale of “amphetamines to the UK with shipping from Germany”. This can be gold to investigative teams as they have a starting point with which to begin to model threats and direct and target their resources.

The Risks of Monitoring and Investigating the Dark Web
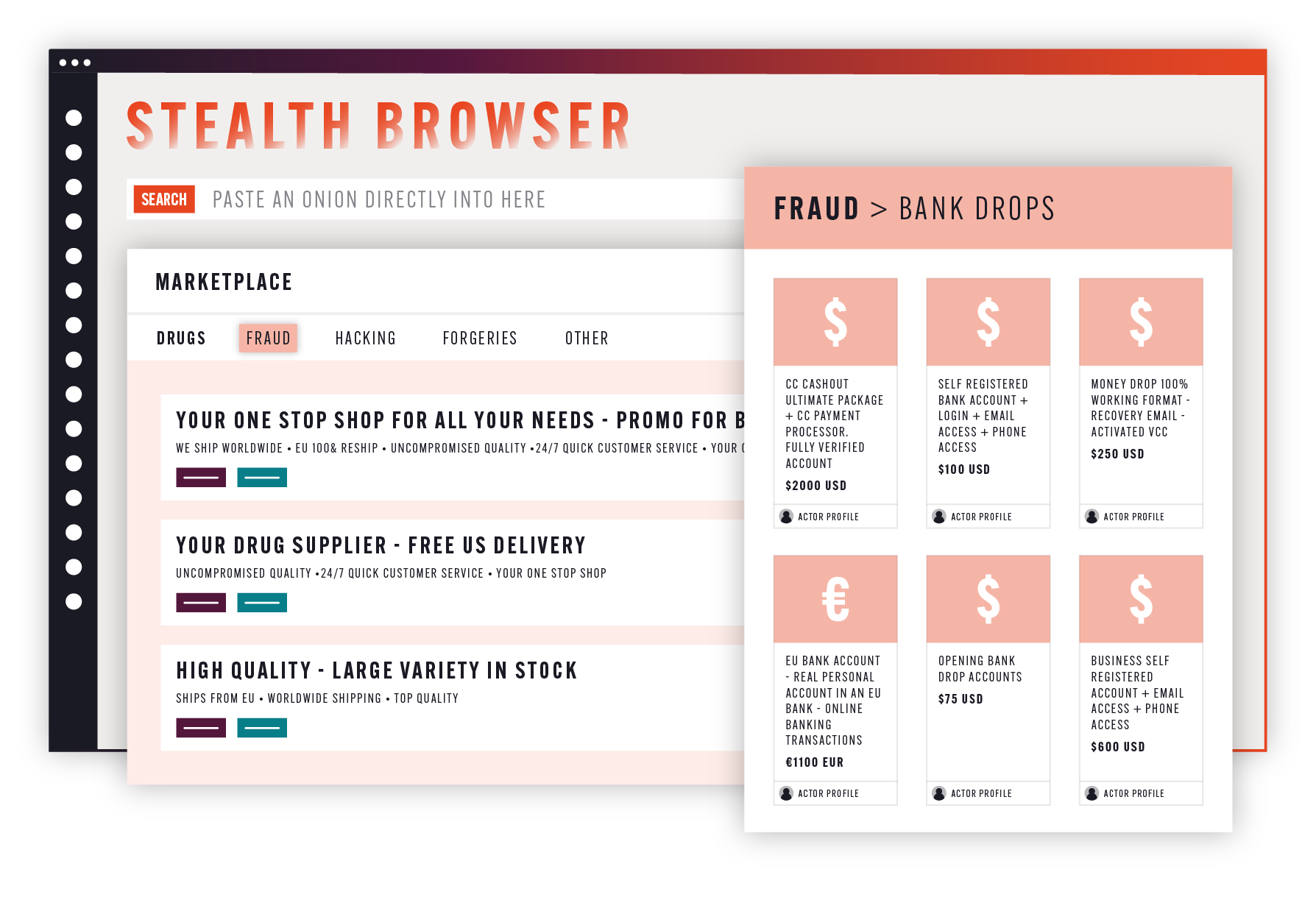
I’d be remiss not to mention our award-winning platform Cerberus. In fact, it’s probably in my contract somewhere that I must. The platform collects, processes, and displays deep and dark web data collected from a range of sources that have been assessed by our threat intelligence team to be valuable collections.
This allows investigators to easily search and identify key intelligence as part of their investigative process, and drill down into associated actors, profiles, OSINT, and more. However, we understand that investigations don’t live in a single platform and that there are times when investigators need to actually go to live data sources and conduct their own assessments on the dark web.
Visiting the dark web comes with inherent risks. For example, investigators being identified or exposing their network to malware. Organizations can mitigate this risk through additional infrastructure such as virtual machines (VMs) that isolate the user’s actions and provide a level of protection. From discussions with customers, we found that there can be sporadic availability of VMs for staff, or delay times in setting up this infrastructure when it’s required, as well as inefficiencies in moving between sources such as those in Cerberus to their VM for further investigation.
That is why we have recently introduced a new feature into Cerberus called Stealth Browser, which provisions VMs on demand for users, directly from inside Cerberus, with the software needed to reach the dark web (such as Tor and I2P) already installed.
This means that users can click on a link within Cerberus and automatically be taken to a fresh VM with that data source loaded directly within it. We’ve been using this tool internally within Searchlight for some time now and it’s a great pleasure to make it more widely available to our users so that they can also experience the benefits.
dark web VM use cases for analysts and investigators
Personally, I spend a lot of time within Cerberus tracking actors in order to build out intelligence profiles, whilst regularly switching between Cerberus and my VM, copying and pasting onion URLs between the two, and switching between screens. Having a VM loaded, ready, and waiting has saved me countless hours and allowed me to stay in the flow of an investigation by remaining on a single platform.
OPSEC is another area that is always a concern to me as I, and my team, carry out my investigations. Knowing that they are using correctly and safely configured VMs that live outside of our internal network and are available from whatever machine they are using helps to reassure me that the correct processes are being followed and the correct protections are in place.
Looking at this from an enterprise level, the same benefits are evident. Providing simple, safe, and effective investigative tooling built into the platform that staff are already carrying out investigations within makes a huge amount of sense from a productivity and security standpoint. Providing an analyst with the capability to identify potential threats across a broad range of sources, and then letting them deep dive into those live data sources in order to analyze and assess risk is key to delivering strong threat intelligence.
Similarly with law enforcement investigations, providing investigators with the capability to identify targets, conduct assessments and then collect evidential material directly from dark web source ensures a robust investigative process.
In a nutshell, what the Stealth Browser offers is a combination of efficiency and safety, which cannot be ignored nowadays where trade-offs between the two are rarely accepted in a business and law enforcement environment. Providing this feature to users of Cerberus allows us to continue delivering on our mission of protecting society from the threats of the dark web, whether those users are analysts working hard to defend their organization, or law enforcement investigators protecting the public.
Want to see the Stealth Browser in action? BOOK A DEMO TODAY.
Related Content


CISO Report: How Enterprises Are Using Dark Web Intelligence
Report
Clear, Deep, and Dark Web: Beyond the Iceberg
About The Dark Web Law Enforcement
Fighting For Child Protection On The Dark Web
Law Enforcement
How Tor Works
About The Dark Web Law Enforcement
