Searchlight is used by security professionals and investigators to surface criminal activity and protect businesses. Book your demo to learn more about our:
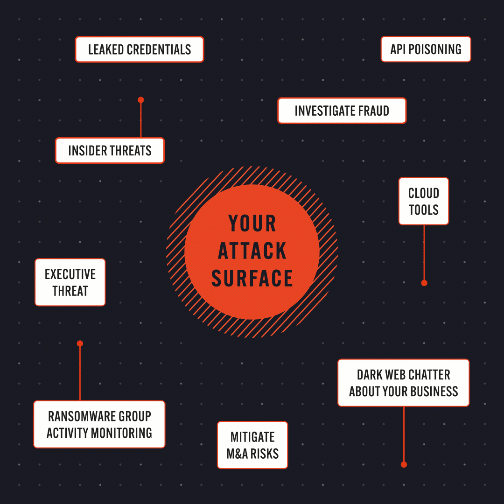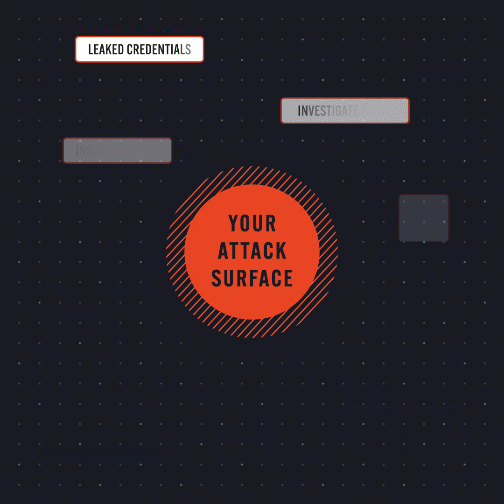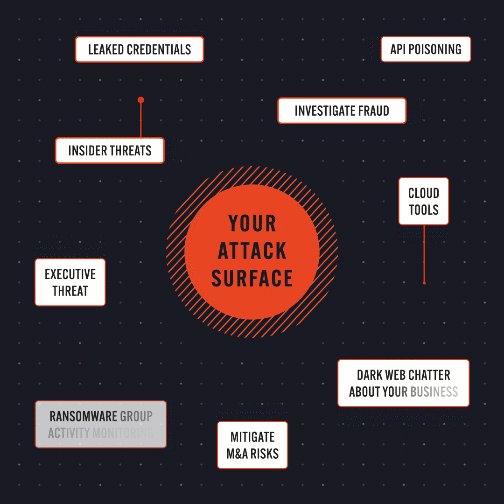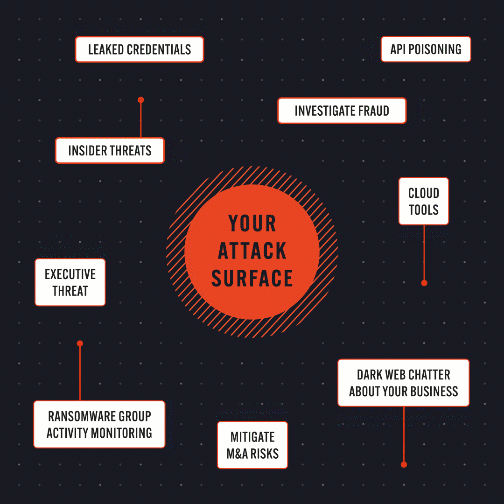
Preempt emerging threats across your attack surface and the dark web
Security teams need complete visibility of their attack surface – internal, external, and hidden.
That’s where Searchlight comes in.
Trusted by leading organizations like Afterpay, Qantas, and Twilio, our preemptive threat exposure management suite provides complete visibility, helping teams detect, investigate, and mitigate risks before they escalate into costly cyber incidents.
The Preemptive Advantage
Faster mitigation
The window between vulnerability exploitation and the use of breached credentials is shrinking. Our hourly scans catch exposures before they can be exploited, helping you remediate threats faster.
Higher signal with verified alerts
False alarms slow teams down. Searchlight automatically detects and prioritizes version-specific exploitable exposures, so you can focus on real threats - cutting noise and improving response time.
Novel security research
Our security researchers identify new vulnerabilities and monitor the dark web for criminal activity, while our data scientists analyze breach data from 20,000+ organizations to measure risk and provide early warnings before threats become active.

World-class security research, built in as standard
Led by recognized industry leaders: Shubham Shah, a top 50 HackerOne bug bounty hunter, and Dr. Gareth Owenson, a global authority in Tor dark web research, our security team identifies hidden risks in the tools your team uses every day and emerging threats on the dark web before attackers can exploit them.

96% faster than other vendors
Your attack surface deserves more than a daily scan. Searchlight scans your entire environment hourly – giving you continuous visibility into exploitable threats while cutting your maximum exposure window from 24 hours to 1 hour.

Proprietary technology that delivers.
Our proprietary and intuitive, no-install monitoring, investigation, and cyber risk tools make your team’s life easier – preemptively flagging cyber risks before they become incidents – while strengthening your organization’s cybersecurity.
Shine a light on hidden risks with our unique capabilities
Stay ahead of novel vulnerabilities
Our researchers hunt zero-day vulnerabilities in enterprise software and deliver personalized alerts months before public disclosure – giving your team a head start on defense.
Tailored alerts from closed-source intel
Continuously monitor for mentions of your organization across underground forums, marketplaces, and encrypted Telegram and Discord chats.
Ransomware group and market dashboards
Access pre-aggregated intelligence on the most active markets and vendors – making it easier to focus on local or mission-specific threats.
High-signal exposure engine
Get hyper-personalized alerts on verified exposures, going beyond basic CVEs, with actionable findings and proof-of-concepts for every issue.
Dark web traffic monitoring
Advanced network traffic analysis provides visibility into all incoming and outgoing dark web traffic to any IP address, CIDR, or domain using our proprietary technology.
Instantly quanitfy and price risk
See, score, and manage cyber risk in real time – across your portfolio and vendor network – using real attacker data instead of error-prone spreadsheets.
Build your own checks with Custom Signatures
Run your own security checks, using our powerful exposure engine and IOC capabilities. Develop custom checks for a wide array of scenarios, including HTTP, Javascript, TPPE, or IOC based-threats.
Stealth Browser, dark web virtual machine
Anonymously investigate I2P and Tor directly from the browser, safe in the knowledge that your identity is protected and malware can’t jump to your live network.
AI-Powered Research Assistant
Surface insights faster with AI: Query the dark web with natural language to generate reports on threat actors, ransomware groups, and pull tabulated intelligence directly related to your organization.
Join the companies taking a preemptive approach to security
See how Searchlight can identify hidden assets and emerging threats before attackers exploit them
Automated asset & threat discovery – hourly (not daily) scans detect exposed assets and third-party risks faster than any other ASM
Hyper personalized, high-signal alerts – automatically prioritize what matters most
Unique pre-attack intel – align threat insights to business objectives with visibility into exposed assets, leaked creds, and dark web attack vectors