
everything you’ve been too afraid to ask about the dark web, including how to defend your business against dark web attacks and explain the value of dark web intelligence to senior executives.
We know from our observations that organizations across all industries are targeted by cybercriminals operating on the dark web. If this is something you’re concerned about, this cheat sheet is where you can find an overview of the dark web, its potential benefits for security teams, and strategies for communicating the importance of dark web intelligence to senior executives.
- What is the dark web?
- How can I access the dark web?
- What will I find on the dark web?
- What are the major risks that businesses face on the dark web?
- How to defend your business against attacks originating on the dark web?
- How do you explain the value of dark web intelligence to senior executives?
WHAT IS THE DARK WEB?
As the word “dark” hints at, the dark web refers to a part of the internet that is in the shadows and inaccessible through regular search engines or internet browsers. To access it you need to install specific software on your computer. It is notoriously associated with illegal activity that is intentionally hidden to avoid scrutiny from law enforcement, governments, and other entities like internet service providers.
Websites on the dark web network Tor are called onions or hidden services and are not indexed by conventional search engines, like Google or Bing. These domains end in .onion, preceded by a random 56 combination of letters and numbers.
An easy way to visualize where the dark web exists on the internet is using an iceberg.
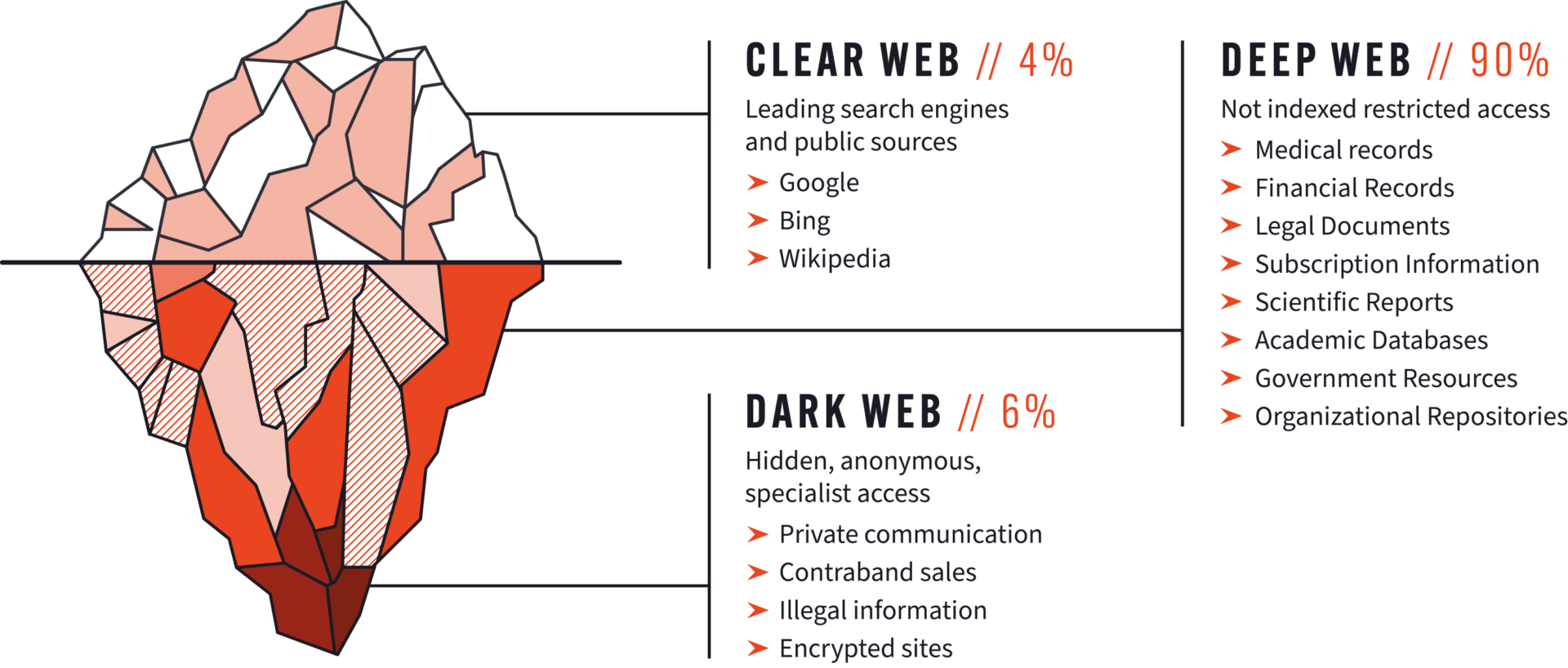
In this metaphor, the deep web and the dark web are found at the base of the iceberg. These collectively make up around 96% of the unindexed parts of the internet, out of sight of law enforcement and security teams, below the water line.
Related resources:
→ Video: What’s on the dark web and how do criminals use it?
How can I access the dark web?
If you want to access the dark web you will need to first install specialist browsing software, such as Tor or use a dark web-enabled virtual machine, like Stealth Browser. The US government originally developed Tor for secure communications but is now run by a non-profit called The Tor Project. Tor operates on the concept of “onion routing”, which involves data being relayed through a circuit of nodes. It’s a bit like an athletics relay race where you only know the identity of the person who handed you the baton and the person you’re passing it on to, but you have no idea where the race started or where it will end. Criminals value this degree of anonymity the dark web gives them. But as we’ll explain a little later on, criminals using the dark web think you can’t see them, with Searchlight you can.
As demonstrated by Robert Fitzsimons in the below video, each relay only knows the identity of the previous and next node. With sufficient nodes, and wrapping each hop in a separate layer of encryption, it is possible to keep the identity of the user anonymous.
Related resources:
→ Webinar: Our CTO and world-renowned dark web expert Dr Gareth Owenson explains how Tor works
What will I find on the dark web?
The Tor Project aims to provide a safe and private space that supports free speech. The dark web can be used positively, such as by whistleblowers or those living under oppressive regimes.
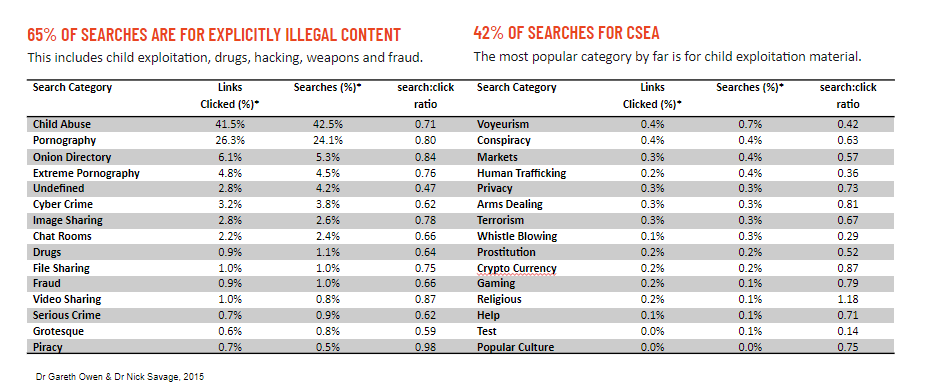
However, our research indicates that the majority of websites and activities on the dark web host illegal content. This includes various illicit activities such as drug sales, ransomware as a service (RaaS), trading and dissemination of breached data, financial crime, fraud, and child sexual abuse material.
Related resources:
→ Our Dark Web Hub gives an overview of marketplaces, forums, and ransomware leak sites on the dark web.
What are the major risks that businesses face on the dark web?
The dark web is a major threat to businesses of all sizes as it is where criminal reconnaissance occurs. The dark web is also where criminals buy and sell stolen data, including personally identifiable information (PII), login credentials, financial details, and intellectual property.
One of the biggest threats is breached and stolen credentials. Research by Verizon discovered that 89% of breaches involve the use of stolen credentials to establish access. Based on this, it couldn’t be more important for security teams to monitor for the sale of any occurrences of their data on dark web forums and leak sites.
Ransomware also remains a persistent threat to businesses across all sectors on the dark web and is closely tied to breached and stolen credentials. This risk has only grown with the rise of Ransomware-as-a-Service (RaaS) operators including CL0P, LockBit, and BlackCat making it easier for less technically capable cybercriminals to launch extortion campaigns against businesses. But it’s important to remember that ransomware attacks don’t spring out of nowhere. The pre-attack planning, initial access brokerage, and reconnaissance phases for these attacks often take place on the dark web or in encrypted chats using tools like Telegram.

Related resources:
→ Read the mitigation guide: Combatting Initial Access Brokers With Dark Web Intelligence
How to defend your business against attacks originating on the dark web?
The threat posed by criminals on the dark web also offers an opportunity to security teams. By automatically monitoring the dark web for attributes linked to your external threat surface, such as domains, IP addresses, and employee credentials, you can identify when they are being targeted by dark web hackers on forums, marketplaces, or messaging platforms like Telegram. This early warning from the dark web gives security teams invaluable time to adapt their defenses based on likely threats and – consequently – a far greater chance of preventing costly cyberattacks.
In addition to monitoring using automated tools like DarkIQ, security teams should also be conducting dark web investigations to learn more about their adversaries and establish where the next attack is coming from, and how it might be conducted. For example, if a security team identifies an Initial Access Broker post or marketplace listing from an employee (insider threat) on the dark web that could relate to their organization, a threat hunter could conduct a dark web investigation into the actor to find additional intelligence – such as any linked accounts, any email addresses, crypto-wallets etc., but also information about how the actor operates, which may be vital to pinpointing where the vulnerability may be.
Security teams should use dark web intelligence to inform their threat models – the process by which potential threats can be identified, enumerated, and prioritized from a hypothetical attacker’s point of view.
RELATED RESOURCES:
→ Five steps to building a threat model
How do you explain the value of dark web intelligence to senior executives?
In our survey of CISOs, 93% said they were concerned about dark web threats. However, despite being aware of the threat the dark web poses to businesses, only 31% of companies are using dark web data to identify compromised customer data, and only 29% are using the dark web for threat hunting.
Often this comes down to a lack of awareness from senior stakeholders as to the value of dark web data in preventing costly security incidents. In this final section, we’ll provide three ways security professionals can explain the value of dark web data:
1. advance warning of attack
If your executives were given advance notice of criminals targeting your supply chain or an employee leaking information to the dark web, would they expect you to act on it? Yes, of course they would.
Unfortunately for your executive team, criminals don’t send courtesy emails before they leak breached data or compromise your network. However, dark web intelligence allows you to identify threat actors while they are in the “pre-attack” or reconnaissance stage of a cyberattack and take action before it’s too late. Knowledge of when a cybercriminal is targeting you, with what resources, and which vulnerabilities they are looking to exploit – is a hugely powerful resource for defenders.
2. shift left in Cyber defense
This “pre-attack” stage of a cyberattack is aptly described by two frameworks: the Cyber Kill Chain and the MITRE ATT&CK framework. Both of these can be effective tools for explaining to executives how dark web intelligence allows you to take action against cyberattacks earlier than most cybersecurity tooling is capable of. This can help demonstrate a change in strategy to your shareholders – as you move to preventing, rather than just mitigating cyberattacks.
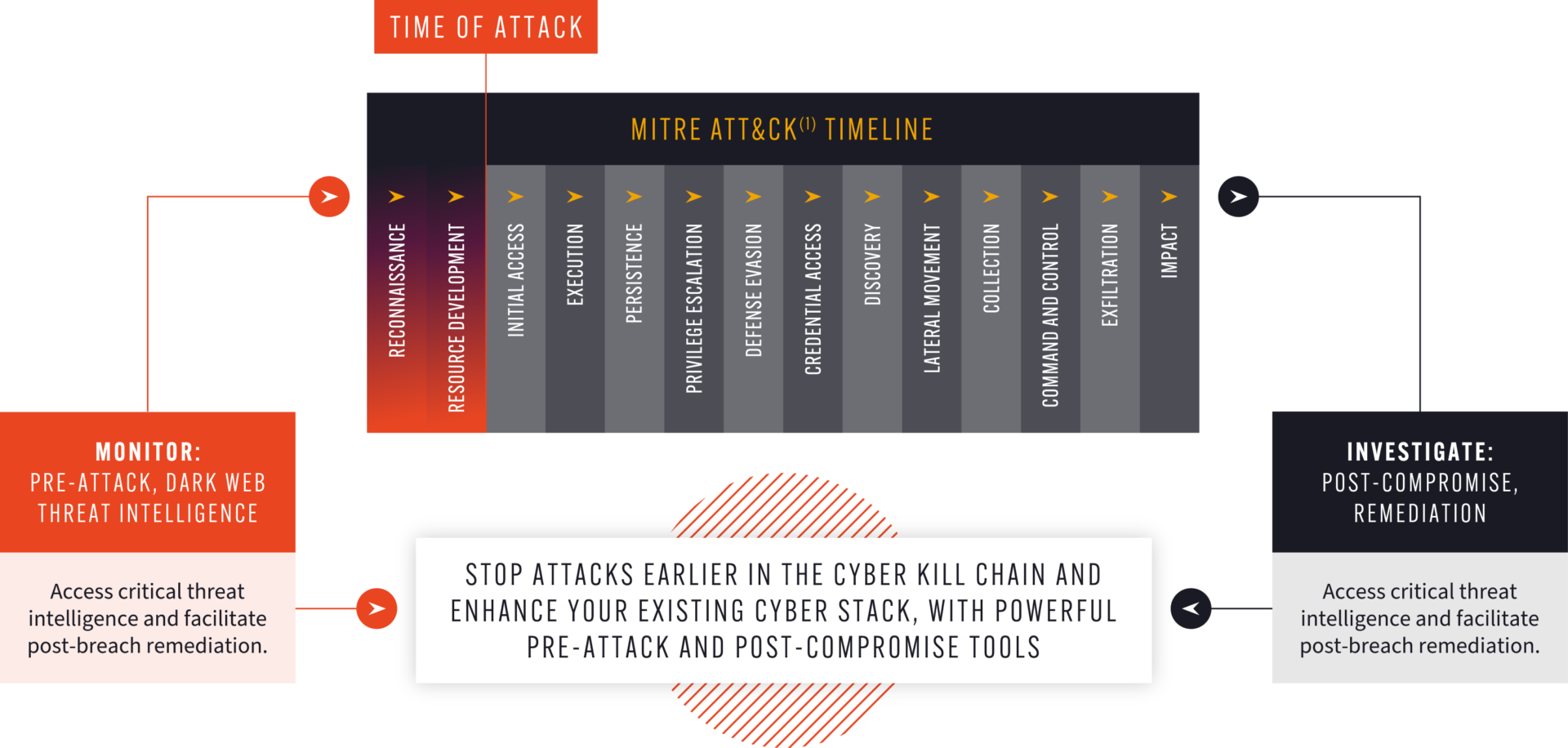
Dark web intelligence also has a role to play on the other side of the scale: providing incident response teams with crucial data on the events that took place outside of the network, in the run up to the attack. This can be used inform the remediation of an incident, or to gain visibility into the exposure of your vendors, suppliers, and interface partners.
3. the wedge of hindsight
The next step is to explain the benefits of “shifting left” in terms of time and cost savings to your business. Simply put, the earlier you can detect a threat, the less cost and damage there will be to your organization. We call this the wedge of hindsight:
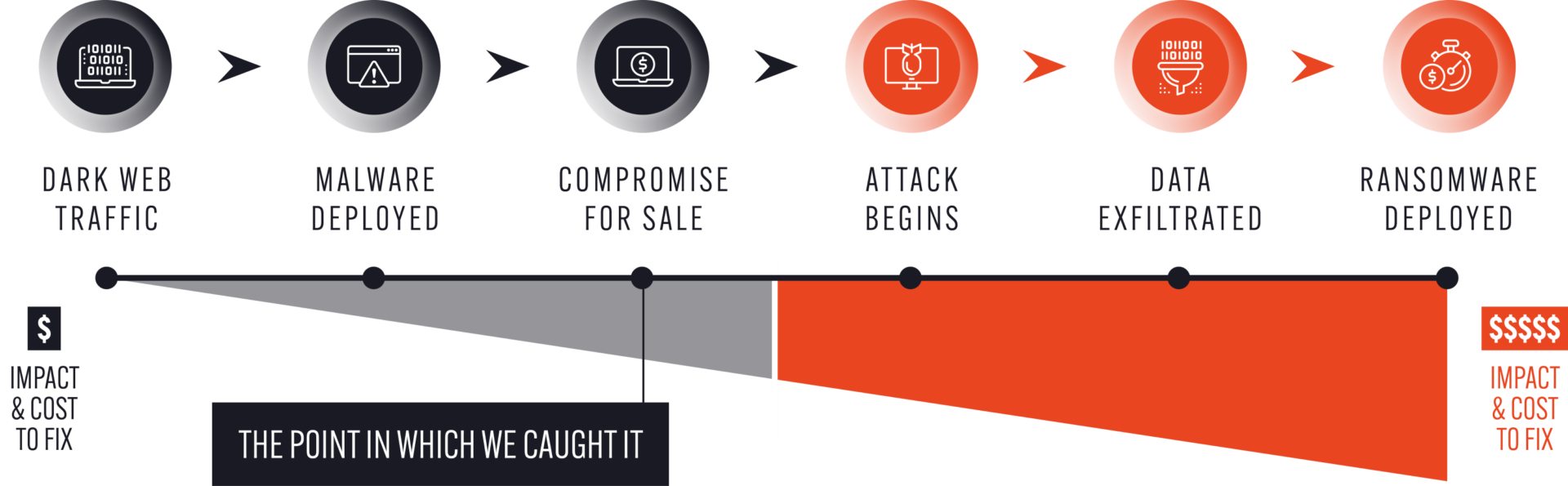
We recently helped an agency mitigate a vulnerability based on our intelligence that their network was compromised by a webshell that a threat actor was advertising on a dark web forum. Consequently, the organization was able to neutralize the webshell and effectively stop the attack – and all its potentially negative consequences – before it happened.
Related resources:
→ Read our report Government Agency Targeted to learn about how we helped an organization spot and stop a threat actor before the cyberattack could be executed.
Strike back against criminals targeting businesses on the dark web
Book a demo to learn how dark web intelligence can be used to pre-empt and prevent cyberattacks.




